Enabling and disabling Application Control rule testing
To enable or disable testing of Application Control rules in Kaspersky Security Center:
- Open the Kaspersky Security Center Administration Console.
- In the console tree, select Policies.
- Select the necessary policy and double-click to open the policy properties.
- In the policy window, select Security Controls → Application Control.
In the right part of the window, the settings of the Application Control component are displayed.
- In the Control mode drop-down list, select one of the following items:
- Denylist. If this option is selected, Application Control allows all users to start any applications, except in cases that satisfy the conditions of Application Control block rules.
- Allowlist. If this option is selected, Application Control blocks all users from starting any applications, except in cases that satisfy the conditions of Application Control allow rules.
- Do one of the following:
- If you want to enable testing of Application Control rules, select the Test rules option in the Action drop-down list.
- If you want to enable Application Control to manage the startup of applications on user computers, in the drop-down list, select Apply rules.
- Save your changes.
To enable testing of Application Control rules or to select a blocking action for Application Control:
- In the main application window, click the
 button.
button. - In the application settings window, select Security Controls → Application Control.
- Click the Blocked applications or Allowed applications button.
This opens the list of Application Control rules.
- In the Status column, select Test mode.
This status means that Kaspersky Endpoint Security always allows the startup of applications to which this rule applies but logs information about the startup of such applications in the report.
- Save your changes.
Kaspersky Endpoint Security will not block applications whose startup is forbidden by the Application Control component, but will send notifications about their startup to the Administration Server. You can also configure the display of notifications about rule testing on the user's computer (see figure below).
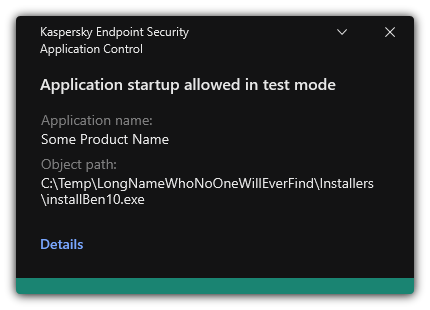
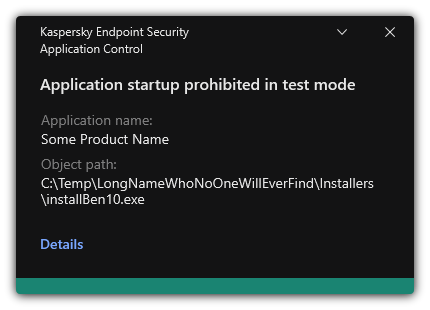
Application Control notifications in test mode
Page top