Web Threat Protection
The Web Threat Protection component prevents downloads of malicious files from the Internet, and also blocks malicious and phishing websites. The component provides computer protection with the help of anti-virus databases, the Kaspersky Security Network cloud service, and heuristic analysis.
Kaspersky Endpoint Security scans HTTP-, HTTPS- and FTP-traffic. Kaspersky Endpoint Security scans URLs and IP addresses. You can specify the ports that Kaspersky Endpoint Security will monitor, or select all ports.
For HTTPS traffic monitoring, you need to enable encrypted connections scan.
When a user tries to open a malicious or phishing website, Kaspersky Endpoint Security will block access and show a warning (see the figure below).
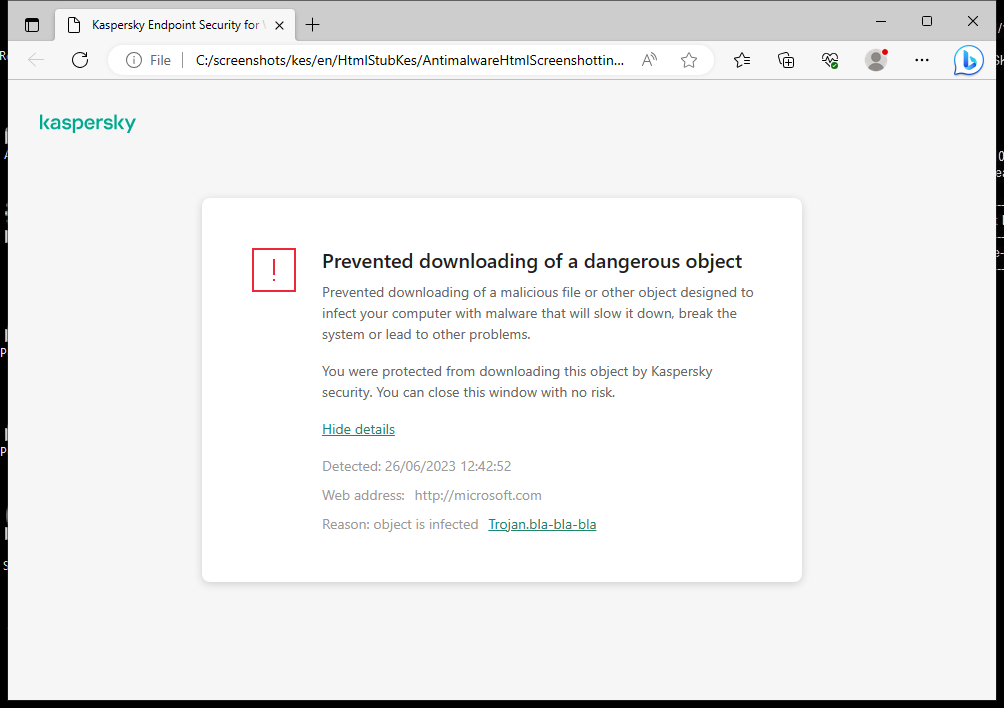
Website access denied message
Web Threat Protection component settings
Parameter |
Description |
|---|---|
Security level (available only in the Administration Console (MMC) and in the Kaspersky Endpoint Security interface) |
For Web Threat Protection, the application can apply different groups of settings. These groups of settings that are stored in the application are called security levels:
|
Action on threat detection |
Block. If this option is selected and an infected object is detected in web traffic, the Web Threat Protection component blocks access to the object and displays a message in the browser. Inform. If this option is selected and an infected object is detected in web traffic, Kaspersky Endpoint Security allows this object to be downloaded to the computer but adds information about the infected object to the list of active threats. |
Check the web address against the database of malicious web addresses (available only in the Administration Console (MMC) and in the Kaspersky Endpoint Security interface) |
Scanning the links to determine whether they are included in the database of malicious web addresses allows you to track websites that have been added to denylist. The database of malicious web addresses is maintained by Kaspersky, included in the application installation package, and updated during Kaspersky Endpoint Security database updates. |
Use Heuristic Analysis (available only in the Administration Console (MMC) and in the Kaspersky Endpoint Security interface) |
The technology was developed for detecting threats that cannot be detected by using the current version of Kaspersky application databases. It detects files that may be infected with an unknown virus or a new variety of a known virus. When web traffic is scanned for viruses and other applications that present a threat, the heuristic analyzer performs instructions in the executable files. The number of instructions that are executed by the heuristic analyzer depends on the level that is specified for the heuristic analyzer. The heuristic analysis level ensures a balance between the thoroughness of searching for new threats, the load on the resources of the operating system, and the duration of heuristic analysis. |
Check the web address against the database of phishing web addresses (available only in the Administration Console (MMC) and in the Kaspersky Endpoint Security interface) |
The database of phishing web addresses includes the web addresses of currently known websites that are used to launch phishing attacks. Kaspersky supplements this database of phishing links with addresses obtained from the international organization known as the Anti-Phishing Working Group. The database of phishing addresses is included in the application installation package and supplemented with Kaspersky Endpoint Security database updates. |
Do not scan web traffic from trusted web addresses |
If the check box is selected, the Web Threat Protection component does not scan the content of web pages or websites whose addresses are included in the list of trusted web addresses. You can add both the specific address and the address mask of a web page/website to the list of trusted web addresses. You can also create a general list of exclusions for encrypted connections. In this case, Kaspersky Endpoint Security does not scan HTTPS traffic of trusted web addresses when Web Threat Protection, Mail Threat Protection, Web Control components are doing their work. |