Contents
- Standard integration (RSA NetWitness)
- About the standard integration scheme (RSA NetWitness)
- Step 1. Forwarding events from RSA NetWitness
- Step 2. Sending events from Feed Service to RSA NetWitness
- Step 3 (optional). Importing a meta group for browsing fields filled by Feed Service
- Step 4 (optional). Importing Feed Service rules to RSA NetWitness
- Step 5 (optional). Importing a preconfigured report to RSA NetWitness
- Step 6 (optional). Importing preconfigured charts and a dashboard to RSA NetWitness
- Step 7. Performing the verification test (RSA NetWitness)
Standard integration (RSA NetWitness)
This section contains instructions for integrating Kaspersky CyberTrace and RSA NetWitness in the standard integration scheme.
About the standard integration scheme (RSA NetWitness)
This section describes the standard integration scheme for RSA NetWitness and Kaspersky CyberTrace.
About the components of the standard integration scheme
The following components are used in the standard integration scheme for RSA NetWitness:
- Feed Service
This service matches RSA NetWitness events against Kaspersky Threat Data Feeds.
- RSA NetWitness
The SIEM solution used in this integration.
- Security controls
These are sources of events for RSA NetWitness such as firewalls, proxies, intrusion detection systems, and other networking devices.
Security controls can send events to RSA NetWitness by any method supported by RSA NetWitness.
Standard integration scheme
In the standard integration scheme, Feed Service by default is configured to listen for incoming events from RSA NetWitness on 127.0.0.1:9999.
Feed Service sends detection events to IP address 127.0.0.1 and port 514 of the interface defined in RSA configuration. The address of this interface is specified when you install Kaspersky CyberTrace. Security controls also send events to port 514 of the interface defined in the RSA NetWitness configuration.
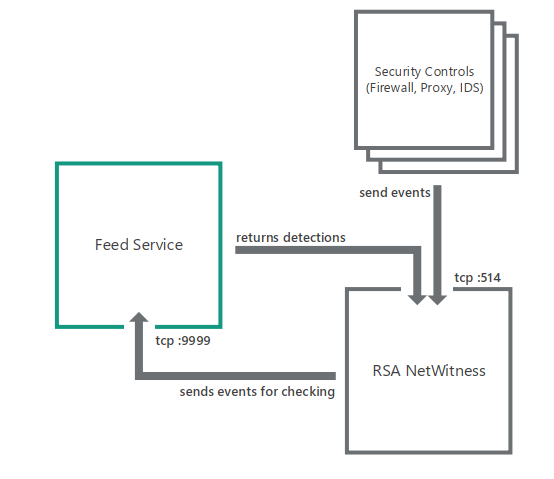
Standard integration scheme for RSA NetWitness
Page topStep 1. Forwarding events from RSA NetWitness
This section describes how to configure RSA NetWitness so that it will forward the received events to Feed Service.
To forward events from RSA NetWitness to Feed Service:
- In the RSA NetWitness main window, select Administration > Services.
- In the Services table, below, select the relevant Log Decoder (the Log Decoder that receives events containing a URL, hash, or IP address).
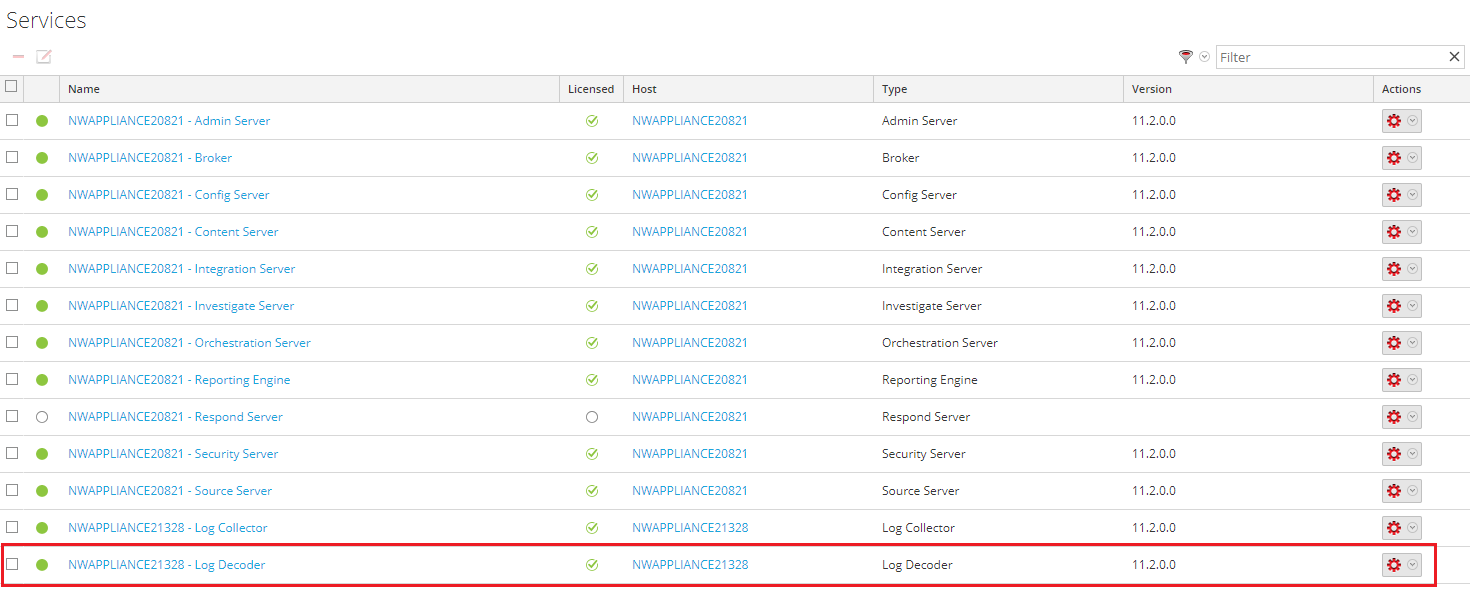
Selecting a Log Decoder
If more than one Log Decoder is used for receiving events, repeat the following steps for each Log Decoder.
- For the selected Log Decoder, in the Actions column, select the Settings split button (
 ) and in the drop-down list select View > Config.
) and in the drop-down list select View > Config. - Select the App Rules tab and click the Add button (
 ).
).The Rule Editor window opens.
- Specify the following data:
- Rule Name:
cybertrace - Condition:
device.type='%DEVICE_NAME_1%'This is an example of a condition, in which the
%DEVICE_NAME_1%string represents the name of the device whose events must be sent to Feed Service. Following is another example of a condition, according to which events from Cisco ASA and Check Point Firewall must be sent to Feed Service:device.type='ciscoasa' || device.type='checkpointfw1'If an event meets the condition specified here, it will be sent to Feed Service.
- Alert: Selected
- Forward: Selected
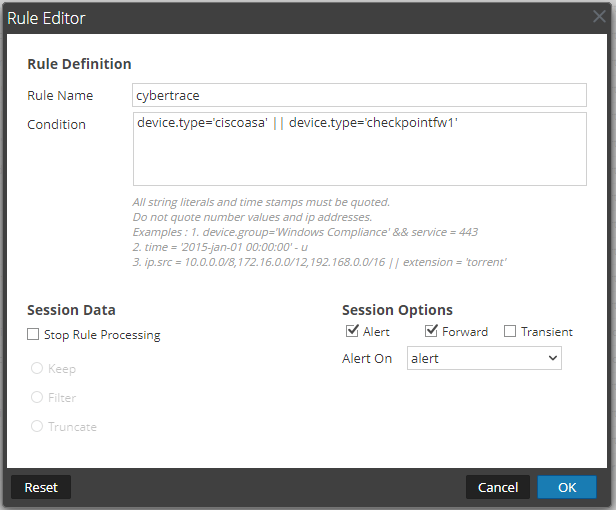
Rule Editor window
For information on how to create rules, refer to https://community.rsa.com/t5/rsa-netwitness-platform-online/configure-application-rules/ta-p/592148.
- Rule Name:
- Click OK.
- Click Apply.
- Next to the Log Decoder name, select Config > Explore.
- Specify the destination:
- For RSA NetWitness versions 11.2 and above:
For the /decoder/config/logs.forwarding.destination parameter, specify the following destination:
cybertrace=tcp:[IP]:[port]:rfc3164Here,
[IP]is the IP address of the computer on which Feed Service is installed, and[port]is the port that Feed Service listens on for events (by default, the port9999is used). The IP address and port are the same as specified on the Settings > Service tab of Kaspersky CyberTrace Web. - For RSA NetWitness versions below 11.2:
- For the /decoder/config/logs.forwarding.destination parameter, specify the following destination:
cybertrace=tcp:[IP]:[port]Here,
[IP]is the IP address of the computer on which Feed Service is installed, and[port]is the port that Feed Service listens on for events (by default, the port9999is used). The IP address and port are the same as specified on the Settings > Service tab of Kaspersky CyberTrace Web. - In the EventDelimeter parameter, in the Feed Service configuration file, specify the
(\<\d+\>)value.
- For the /decoder/config/logs.forwarding.destination parameter, specify the following destination:
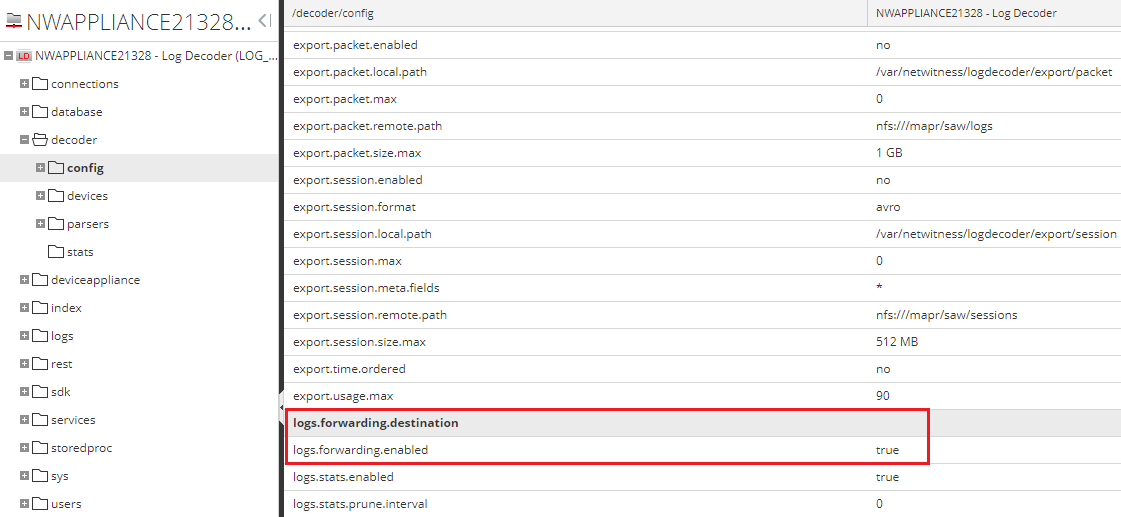
Log events forwarding settings
- For RSA NetWitness versions 11.2 and above:
- In the /decoder/config/logs.forwarding.enabled parameter, specify
true.
After these actions are performed, RSA NetWitness will forward the events that satisfy the cybertrace rule to the address that you specified in the logs.forwarding.destination parameter.
For more information on event forwarding, refer to https://community.rsa.com/t5/rsa-netwitness-platform-online/decoder-configure-syslog-forwarding-to-destination/ta-p/572084.
Page topStep 2. Sending events from Feed Service to RSA NetWitness
This section describes the actions to take so that Feed Service will send events to RSA NetWitness.
Note that Feed Service sends events to a Log Decoder service.
To send events from Feed Service to RSA NetWitness:
- In Kaspersky CyberTrace Web, on the Settings > Service tab, specify the following value for the Service sends events to text box:
[IP]:514Here
[IP]is the IP address of the Log Decoder service to which Feed Service will send events.If there are several Log Decoder services, perform the integration with only one of the Log Decoders.
- In
/etc/netwitness/ng/envision/etc/devicesdirectory of the computer on which Log Decoder runs, create acybertracesubdirectory and copy to the subdirectory the following files from the%service_dir%/integration/rsa/cybertracedirectory:- cybertrace.ini
This is a configuration file that contains declaration of Feed Service for RSA NetWitness.
- v20_cybertracemsg.xml
This is a configuration file that contains parsing rules for events that are sent from Feed Service to RSA NetWitness. See below in this section for a description of the contents.
You can find these files in the
integration/cybertracedirectory of the distribution kit. - cybertrace.ini
- Restart Log Decoder.
For this purpose, in the Services view, for the selected Log Decoder click the Settings split button (
 ) and from the drop-down list select Restart.
) and from the drop-down list select Restart. - Make sure that the
cybertraceservice parser is turned on in RSA NetWitness.You can do this as follows:
- In the RSA NetWitness menu, select Administration > Services.
- In the Services grid, select the Log Decoder, and from the Actions menu, choose View > Config.
- In the Service Parsers Configuration panel, search for cybertrace, and ensure that the Config Value field in this row is selected.
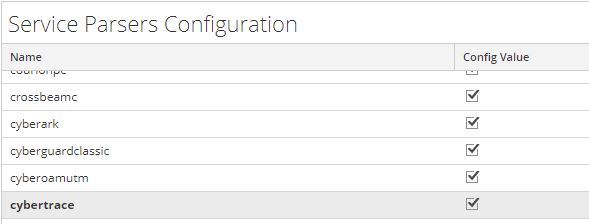
Service Parsers Configuration grid
- Restart Feed Service.
You can restart Feed Service by running the kl_feed_service script as follows:
systemctl restart cybertrace.serviceYou can do this by using Kaspersky CyberTrace Web too.
Contents of integration files
The v20_cybertracemsg.xml file contains the following rule for parsing service events from Feed Service:
alert=<action>,context=<msg> |
The v20_cybertracemsg.xml file contains several rules for parsing detection events from Feed Service:
- MATCH_EVENT:01—For parsing detection events when Botnet CnC URL Data Feed is involved in the detection process.
- MATCH_EVENT:02—For parsing detection events when Malicious URL Data Feed is involved in the detection process.
- MATCH_EVENT:03—For parsing detection events when Mobile Botnet CnC URL Data Feed is involved in the detection process.
- MATCH_EVENT:04—For parsing detection events when Malicious Hash Data Feed is involved in the detection process.
- MATCH_EVENT:05—For parsing detection events when Phishing URL Data Feed is involved in the detection process.
- MATCH_EVENT:06—For parsing detection events when Ransomware URL Data Feed or IoT URL Data Feed are involved in the detection process.
- MATCH_EVENT:07—For parsing detection events when IP Reputation Data Feed is involved in the detection process.
- MATCH_EVENT:08—For parsing detection events when Vulnerability Data Feed is involved in the detection process.
- MATCH_EVENT:09—For parsing detection events when Mobile Malicious Hash Data Feed is involved in the detection process.
- MATCH_EVENT:10—For parsing detection events when APT IP and URL feeds are involved in the detection process.
- MATCH_EVENT:11—For parsing detection events when Industrial Control Systems Data Feed is involved in the detection process.
- MATCH_EVENT:12—For parsing detection events when APT Hash feeds are involved in the detection process.
- MATCH_EVENT—For parsing detection events when other feeds are involved in the detection process.
The fields of the cybertrace.ini file and the v20_cybertracemsg.xml file correspond to the following format of service events and detection events from Feed Service:
<AlertFormat><![CDATA[<232>%CyberTrace:ALERT_EVENT alert=%Alert%,context=%RecordContext%]]></AlertFormat> <EventFormat><![CDATA[<232>%CyberTrace:MATCH_EVENT category=%Category%,detected=%MatchedIndicator%,url=%RE_URL%,hash=%RE_HASH%,dst=%DST_IP%,src=%SRC_IP%,dvc=%DeviceIp%,dev_name=%Device%,dev_action=%DeviceAction%,user=%UserName%,cnf=%Confidence%,actF:%ActionableFields%,context=%RecordContext%]]> </EventFormat> |
In the v20_cybertracemsg.xml file, the format of events from Feed Service is provided in the HEADER/content element and in the MESSAGE/content element. Make sure that the following fields are present in the index files of Log Decoder and Concentrator: virusname, url, checksum, and ip.src, ip.dst. As for the fields other than virusname, url, checksum, and ip.src, ip.dst in the MESSAGE/content element, you may or may not use them in the index files of Log Decoder and Concentrator. Also, make sure that the value of the flags attribute is None for each of these fields in the table-map-custom.xml file. If any of these conditions are not met, refer to the section about RSA NetWitness troubleshooting.
The following tables describe the fields used in the v20_cybertracemsg.xml and kl_feed_service.conf files, and describe how fields in one file correspond to fields in the other. If you want to constantly use some new field in detection events, contant your technical account manager (TAM).
- Fields of service events
Field in kl_feed_service.conf
Field in v20_cybertracemsg.xml
Description
<232>
-
Service string for RSA NetWitness.
%CyberTrace:
%CyberTrace:
Informs RSA NetWitness that an event is sent from Feed Service.
ALERT_EVENT
<messageid>
The event type.
-
<!payload>
Notifies RSA NetWitness that the event has additional information, the format of which is provided in the
MESSAGE/contentelement.%Alert%
<action>
The service event (for example, KL_ALERT_ServiceStarted).
%RecordContext%
<msg>
Context information about the service event.
- Fields of detection events
Field in kl_feed_service.conf
Field in v20_cybertracemsg.xml
Description
<232>
-
Service string for RSA NetWitness.
%CyberTrace:
%CyberTrace:
Informs RSA NetWitness that an event is sent from Feed Service.
MATCH_EVENT
<messageid>
The event type.
-
<!payload>
Notifies RSA NetWitness that the event has additional information, the format of which is provided in the
MESSAGE/contentelement.%Category%
<virusname>
Category of the detected object.
%MatchedIndicator%
<kl_detected_indicator%gt;
The detected indicator.
%RE_URL%
<url>
The URL specified in the event from RSA NetWitness.
%RE_HASH%
<checksum>
The hash specified in the event from RSA NetWitness.
%DST_IP%
<daddr>
The IP address to which the request is sent.
%SRC_IP%
<saddr>
The IP address from which the request is sent.
%DeviceIp%
<hostip>
The IP address from which the event is sent.
%Device%
<event_source>
The name of the device that has sent the event.
%DeviceAction%
<action>
The action that the device has performed.
%UserName%
<c_username>
The name of the user on whose account the action described in the event is performed.
%ActionableFields%
The fields' names are discussed below in this section.
Fields of the feed record involved in the detection process that are displayed apart from the context.
%RecordContext%
<fld1>
Context of the feed record that was involved in the detection process.
To view the contents of this field, open the event in RSA NetWitness and select the View Log tab.
%Confidence%
<kl_confidence>
The level of confidence in the indicators of the feed, in percent.
The following tables describe the actionable fields used in the feeds and in the v20_cybertracemsg.xml file, and describe how fields in a feed correspond to fields in the file:
- Botnet CnC URL Data Feed and Demo Botnet CnC URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat
kl_threat
- Malicious Hash Data Feed and Demo Malicious Hash Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
MD5
kl_md5
SHA1
kl_sha1
SHA256
kl_sha256
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
file_type
kl_file_type
file_size
kl_file_size
threat
kl_threat
- IP Reputation Data Feed and Demo IP Reputation Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
ip
kl_ip
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat_score
kl_threat_score
category
kl_category
threat
kl_threat
- Malicious URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
files/threat
kl_threat
category
kl_category
- Mobile Malicious Hash Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
MD5
kl_md5
SHA1
kl_sha1
SHA256
kl_sha256
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
threat
kl_threat
file_size
kl_file_size
- Phishing URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
industry
kl_industry
- Vulnerability Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
Date
kl_first_seen
AV Verdict
kl_verdict
When Vulnerability Data Feed is involved in a detection process, the
AV Verdictfield contains one of the following values:warninghighcritical
- Mobile Botnet CnC URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
threat
kl_threat
- Ransomware URL Data Feed or IoT URL Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
mask
kl_mask
first_seen
kl_first_seen
last_seen
kl_last_seen
popularity
kl_popularity
- APT IP and URL feeds
Field in the feed
Field in v20_cybertracemsg.xml
detection_date
kl_detect_date
publication_name
kl_pub_name
- APT Hash feeds
Field in the feed
Field in v20_cybertracemsg.xml
detection_date
kl_detect_date
publication_name
kl_pub_name
SHA1
kl_sha1
SHA256
kl_sha256
- Industrial Control Systems Data Feed
Field in the feed
Field in v20_cybertracemsg.xml
first_seen
kl_first_seen
popularity
kl_popularity
Step 3 (optional). Importing a meta group for browsing fields filled by Feed Service
This section describes how you can import the MetaGroups.jsn file. This file contains a meta group that you can use to browse only those fields in RSA NetWitness that are filled by Feed Service.
The Kaspersky CyberTrace distribution kit contains the integration/rsa/additional_elements/MetaGroups.jsn file. This file contains fields named kl.%field_name%. If you have not added the CyberTrace fields to RSA NetWitness (namely, to the table-map-custom.xml and index-concentrator-custom.xml files), we recommend that you import the MetaGroups_without_kl_fields.jsn file instead of MetaGroups.jsn.
To import the MetaGroups.jsn file:
- On the RSA NetWitness menu, select Investigation > Navigate.
- Select Meta > Manage Meta Groups.
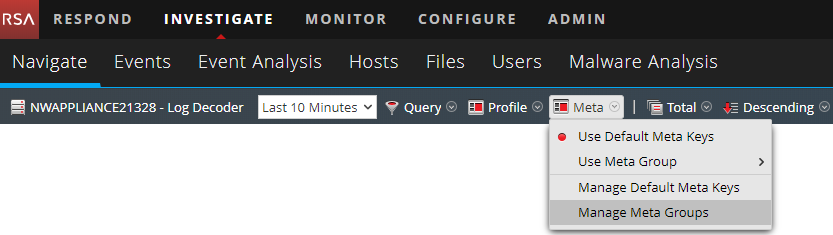
Manage Meta Groups command
- In the Manage Meta Groups window, click the Import button (
 ).
).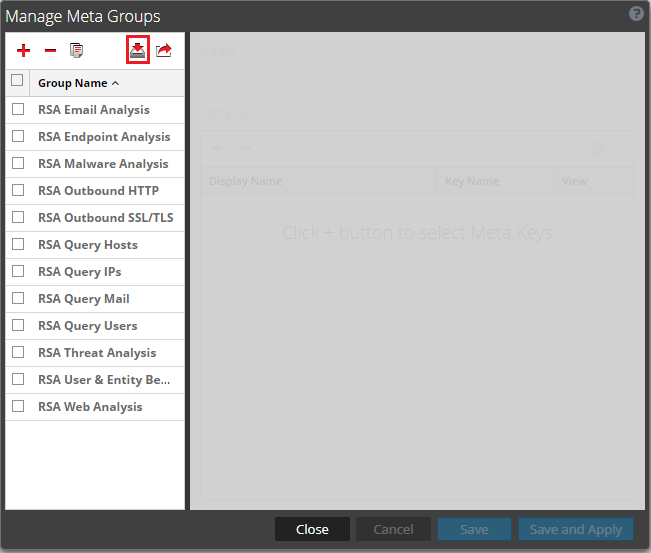
Manage Meta Groups window
- Select the MetaGroups.jsn file and click the Upload button (
 ).
). - Select the
CyberTrace_META_GROUPmeta group and click Save and Apply.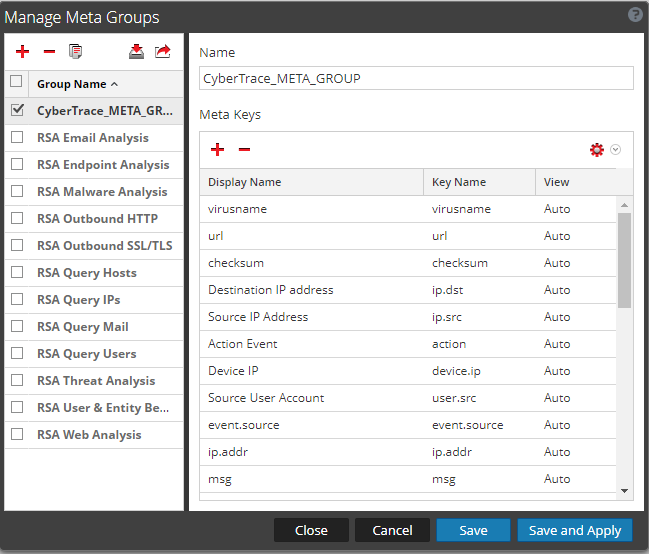
Adding a meta group
Step 4 (optional). Importing Feed Service rules to RSA NetWitness
The Kaspersky CyberTrace distribution kit contains the CyberTrace_Rules.zip file in the integration/rsa/additional_elements directory. This file contains a set of rules, which you can use to create reports, alerts, and dashboards.
To import the Feed Service rules to RSA NetWitness:
- On the RSA NetWitness menu, select Dashboard > Reports.
In RSA NetWitness 11, you select Monitor > Reports instead.
- Click the Settings split button (
 ) and select Import.
) and select Import.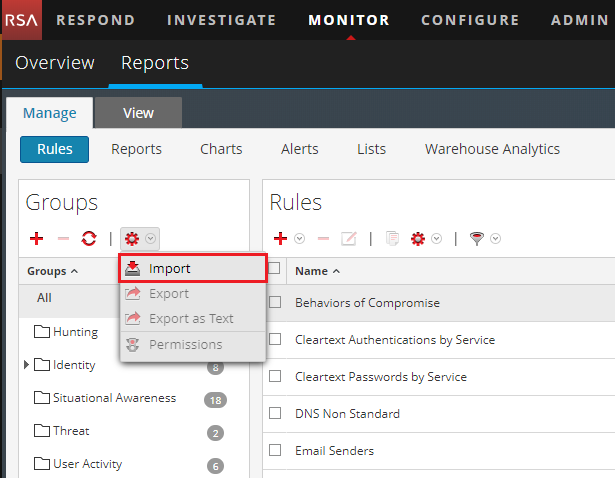
Importing rules
- Choose the CyberTrace_Rules.zip file.
- In the Import Rule window, select the Rule check box and the List check box.
If you import the CyberTrace_Rules.zip file for the first time, you may leave these check boxes cleared.
- Click the Import button.
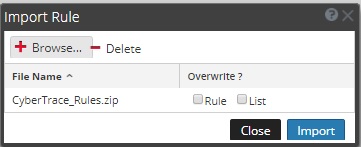
Importing Feed Service rules
The rules imported to RSA NetWitness are listed in the table below.
Rule |
Description |
CyberTrace Detect Botnet |
Selects those detection events from Feed Service that have the Botnet category. The following fields are selected:
|
CyberTrace Detect Malware Hash |
Selects hash detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Malware IP |
Selects IP address detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Malware URL |
Selects URL detection events from Feed Service. The following fields are selected:
|
CyberTrace Detect Stat |
Selects all the categories involved in the detection process. The following fields are selected:
|
CyberTrace Service events |
Selects service events from Feed Service. The following fields are selected:
|
CyberTrace Top 10 IP |
Selects Top 10 detected IP addresses. The following fields are selected:
|
CyberTrace Top 10 URL |
Selects Top 10 detected URLs. The following fields are selected:
|
CyberTrace Top 10 Hash |
Selects Top 10 detected hashes. The following fields are selected:
|
CyberTrace Detected users |
Calculates the number of detection events per user. |
Step 5 (optional). Importing a preconfigured report to RSA NetWitness
This section explains how to import a preconfigured report to RSA NetWitness. To learn how to create a report manually, see the section about creating and viewing reports in RSA NetWitness.
This step requires the importing Feed Service rules step to be completed.
The distribution kit contains the CyberTrace_Reports.zip file. This file contains a preconfigured report, CyberTrace Report.
The CyberTrace Report report contains the following data:
- Detection statistics during the last 24 hours
- Statistics on users who issued detection events during the last 24 hours
- Top 10 URLs, Top 10 IP addresses, and Top 10 Hashes during the last 24 hours
You can import this file in the same way that you import the CyberTrace_Rules.zip file (which contains rules). After the report is imported, you must specify the data source.
To specify the data source for the "CyberTrace Report" report:
- On the RSA NetWitness menu, select Dashboard > Reports. (In RSA NetWitness 11, select Monitor > Reports.)
The Manage tab is displayed.
- Click Reports.
The Reports view is displayed.
- In the Reports view, in the Actions column, click the Settings split button (
 ) for the
) for the CyberTrace Reportreport, and then select Schedule Report.The Schedule Report form appears.
- In the Schedule Report form, specify the following data:
- Schedule name
- Data source (database from the NetWitness DB drop-down list)
Select either the Concentrator that receives events from Feed Service or the Log Decoder that stores events from Feed Service.
- Click the Schedule button.
Step 6 (optional). Importing preconfigured charts and a dashboard to RSA NetWitness
This section describes how you can import preconfigured charts and a dashboard to RSA NetWitness.
This step requires importing Feed Service rules step to be completed.
Importing preconfigured charts
The distribution kit contains the CyberTrace_Charts.zip file. The CyberTrace_Charts.zip file contains preconfigured charts. These charts are used in a preconfigured dashboard.
You can import the CyberTrace_Charts.zip file in the same way as CyberTrace_Rules.zip, which contains rules.
After the CyberTrace_Charts.zip file is imported, specify the data source for each chart (specify either the Concentrator that receives events from Feed Service or the Log Decoder that stores events from Feed Service). To do this, for each chart click the Actions split button ( ) and select Edit. Then in the Data Source field specify the data source and click Save.
) and select Edit. Then in the Data Source field specify the data source and click Save.
Also, enable each chart: select the check boxes next to the chart names (or you can select the check box next to the Enabled column heading) and then click the Enable button ( ).
).
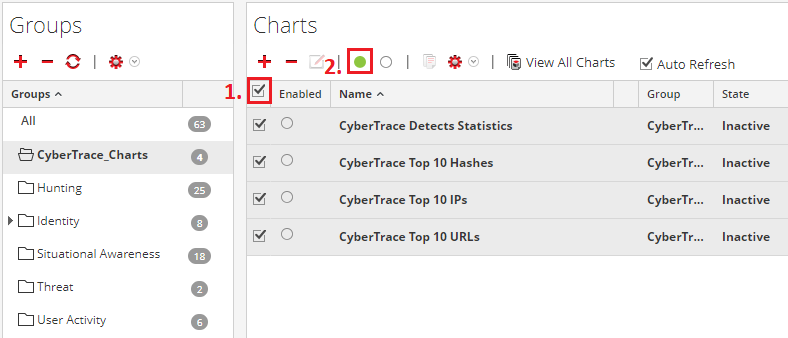
Enabling charts
Importing the Kaspersky CyberTrace dashboard
The distribution kit also contains the Kaspersky+CyberTrace.cfg file. This file contains a preconfigured dashboard, Kaspersky CyberTrace.
You can import the Kaspersky+CyberTrace.cfg file by clicking the Settings split button ( ) in the Dashboard form and selecting Import. A dashlet form appears in the Dashboard form. After the CFG file is imported, configure the following dashlets:
) in the Dashboard form and selecting Import. A dashlet form appears in the Dashboard form. After the CFG file is imported, configure the following dashlets: CyberTrace Detects Statistic, CyberTrace Top 10 URL, CyberTrace Top 10 Hash, and CyberTrace Top 10 IP.
The import instructions above are relevant for RSA NetWitness version 10.6. To import the Kaspersky CyberTrace.zip file in RSA NetWitness version 11.0, click the Import dashboard button ( ).
).
Step 7. Performing the verification test (RSA NetWitness)
After you configure Kaspersky CyberTrace and RSA NetWitness, you can test their performance.
Please make sure you perform the verification test before editing any filtering rules in the Feed Utility configuration file.
To check whether Kaspersky CyberTrace is correctly integrated with RSA NetWitness:
- Configure Log Scanner to send events to the IP address and port that Feed Service listens on.
For this purpose, in the
Connectionelement of the Log Scanner configuration file, specify the IP address and port that are set for outbound events on the Settings > Service tab of Kaspersky CyberTrace Web. - Send the
kl_verification_test_cef.txtfile from the verification directory to Feed Service by using Log Scanner.For this purpose, run the following command:
In Linux:
./log_scanner -p ../verification/kl_verification_test_cef.txtIn Windows:
log_scanner.exe -p ..\verification\kl_verification_test_cef.txtDo not specify the
-rflag in this command: send the test results to the SIEM solution by using the parameters for outbound events specified on the Settings > Service tab of Kaspersky CyberTrace. - Make sure that you obtain the test results according to the table below.
You can view the test results in the same way as when browsing Feed Service events in RSA NetWitness.
Verification test results
The verification test results depends on the feeds you use. The verification test results are listed in the following table.
Verification test results
Feed used |
Detected objects |
Malicious URL Data Feed |
http://fakess123.nu http://badb86360457963b90faac9ae17578ed.com |
Phishing URL Data Feed |
http://fakess123ap.nu http://e77716a952f640b42e4371759a661663.com |
Botnet CnC URL Data Feed |
http://fakess123bn.nu http://a7396d61caffe18a4cffbb3b428c9b60.com |
IP Reputation Data Feed |
192.0.2.0 192.0.2.3 |
Malicious Hash Data Feed |
FEAF2058298C1E174C2B79AFFC7CF4DF 44D88612FEA8A8F36DE82E1278ABB02F (stands for EICAR Standard Anti-Virus Test File) C912705B4BBB14EC7E78FA8B370532C9 |
Mobile Malicious Hash Data Feed |
60300A92E1D0A55C7FDD360EE40A9DC1 |
Mobile Botnet CnC URL Data Feed |
001F6251169E6916C455495050A3FB8D (MD5 hash) sdfed7233dsfg93acvbhl.su/steallallsms.php (URL mask) |
Ransomware URL Data Feed |
http://fakess123r.nu http://fa7830b4811fbef1b187913665e6733c.com |
Vulnerability Data Feed |
D8C1F5B4AD32296649FF46027177C594 |
APT URL Data Feed |
http://b046f5b25458638f6705d53539c79f62.com |
APT Hash Data Feed |
7A2E65A0F70EE0615EC0CA34240CF082 |
APT IP Data Feed |
192.0.2.4 |
IoT URL Data Feed |
http://e593461621ee0f9134c632d00bf108fd.com/.i |
Demo Botnet CnC URL Data Feed |
http://5a015004f9fc05290d87e86d69c4b237.com http://fakess123bn.nu |
Demo IP Reputation Data Feed |
192.0.2.1 192.0.2.3 |
Demo Malicious Hash Data Feed |
776735A8CA96DB15B422879DA599F474 FEAF2058298C1E174C2B79AFFC7CF4DF 44D88612FEA8A8F36DE82E1278ABB02F |
ICS Hash Data Feed |
7A8F30B40C6564EFF95E678F7C43346C |