Step 8 (optional). Creating notifications about incoming service events
You can create notifications about issues with Kaspersky CyberTrace by configuring alert rules.
To create notifications about service events from Kaspersky CyberTrace in QRadar:
- Run QRadar Console.
- Select any of the Offenses, Log Activity or Network Activity tabs, and then select Rules.
- In the Actions drop-down list, select New Event Rule.
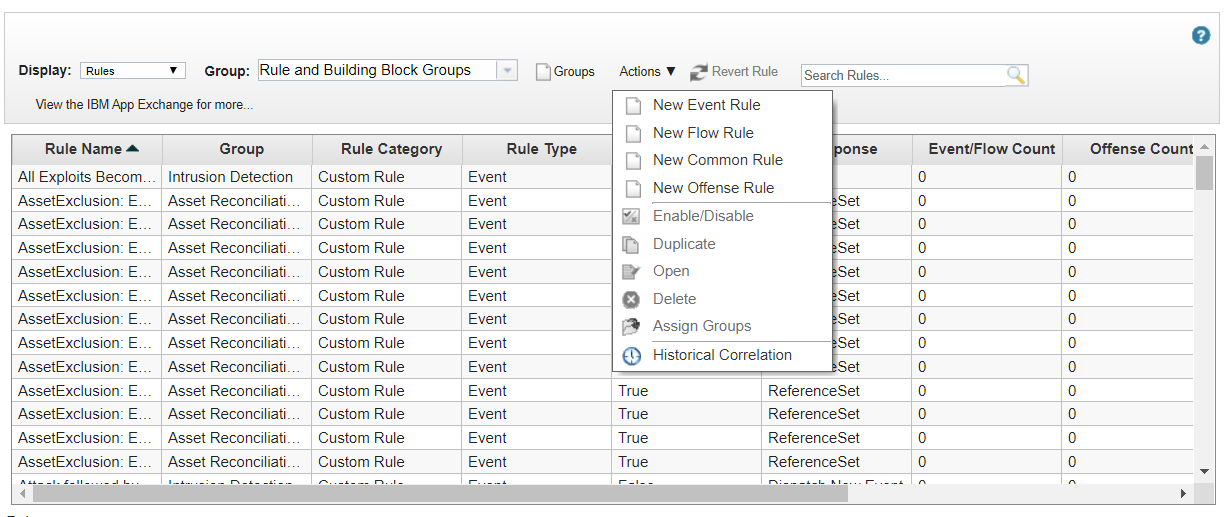
The Rules page
The Rule Wizard page opens.
- On the Rule Wizard page, click Next to select the source from which you want the rule to be generated.
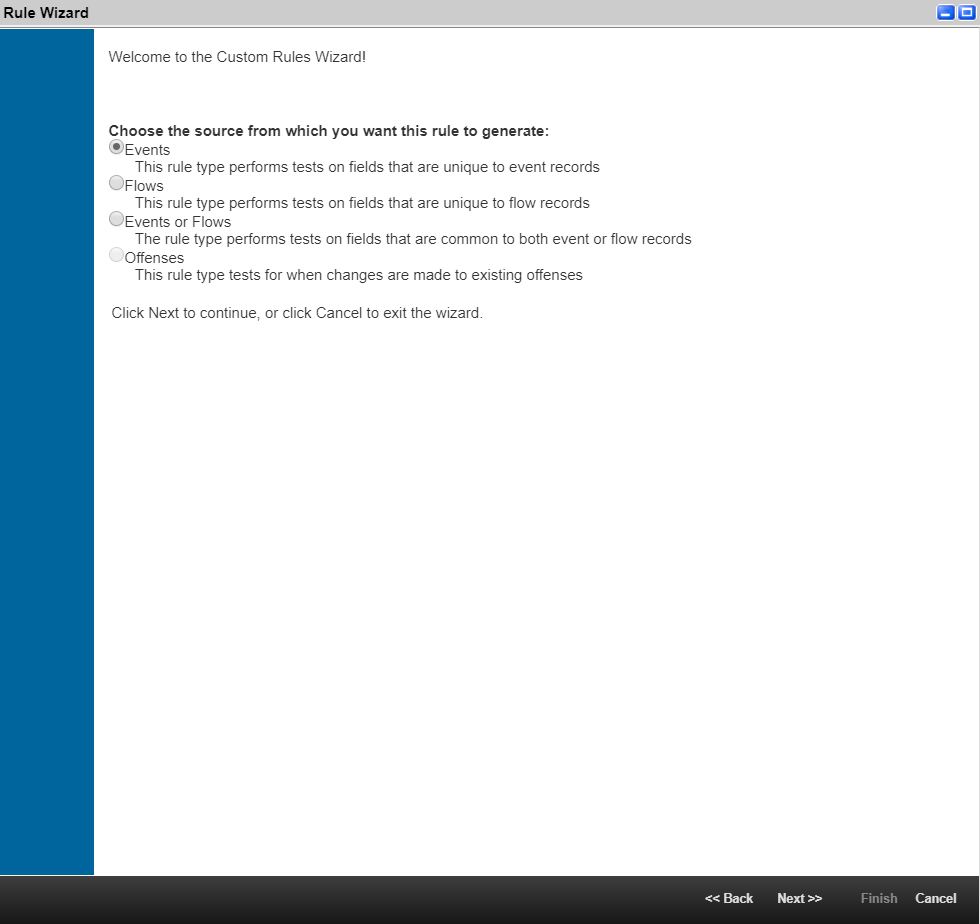
The Rules Wizard window
- Select Events, and then click Next.
- On the Rule Test Stack Editor page, perform the following actions:
- Add the following test conditions for a new rule:
when the event(s) were detected by one or more of these log sourceswhen the event matches this search filter
- For each specified condition, set a logical
andoperator. - For the
when the event(s) were detected by one or more of these log sourcescondition, specify Log Source that is equal toKL_Threat_Feed_Service_v2. If this event source is absent, add it as described in the "Adding Feed Service as a log source" section. - For the
when the event matches this search filtercondition, specify a filter for comparing Event Name with the value of the event source name by performing the following actions:- In the list of the event fields, select Event Name.
- In the list of conditions, select Equals.
- Click Browse to choose the name of the service event for which the rule is created.
To get more information about all Kaspersky CyberTrace service events, see subsection "Types of alert events" of the "About output format settings" section.
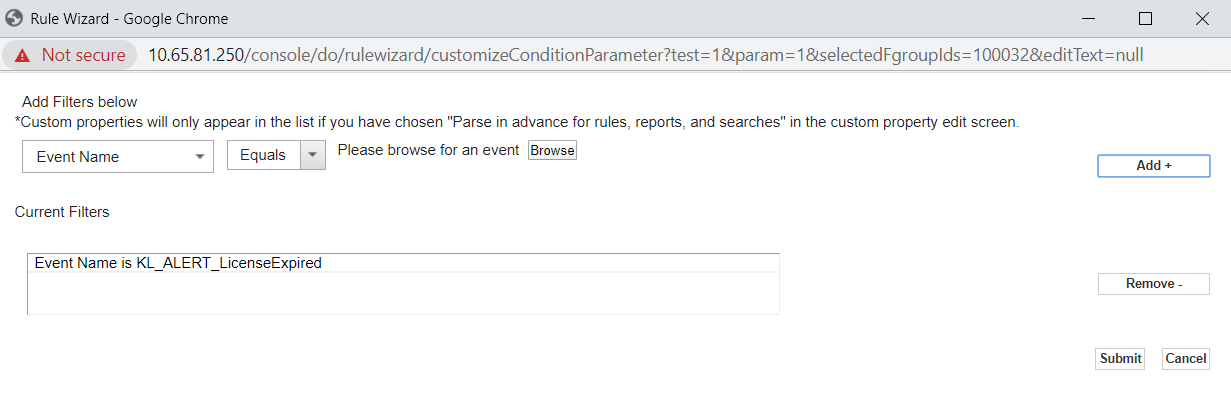
- Click Add+, and then Submit.
If the necessary event is absent, add it to the QRadar Identifiers (QID) list as described in the "Importing QIDs to QRadar" section.
- Enter the name of the rule and select the way in which this rule will be applied to the incoming events (Local or Global). For more information about the Local and Global rules, see IBM documentation.
- Select the group that you need for the rule.
- Add a description for the rule.
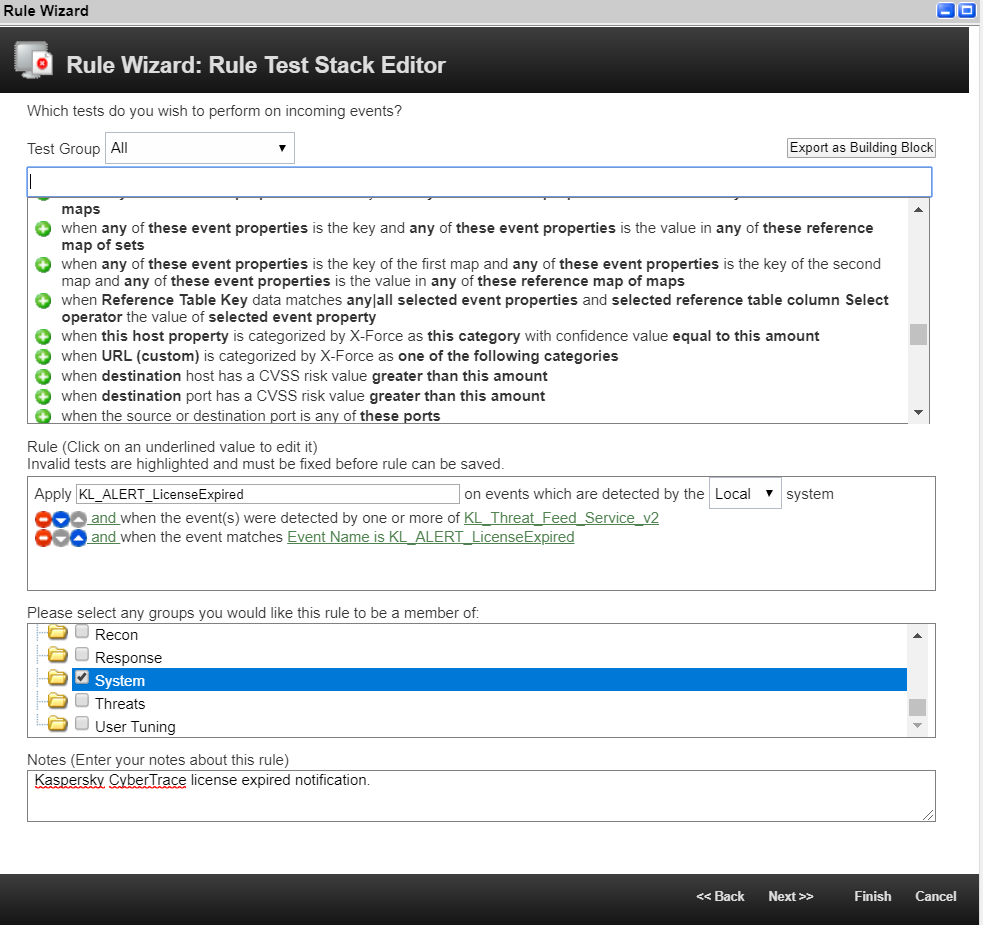
The Rule Editor window
- Click Next.
- Add the following test conditions for a new rule:
- On the Rule Response page, perform the following actions:
- Select Notify.
- If necessary, specify a limit on a rule triggering in the Response Limiter section.
- Check the Enable Rule section.
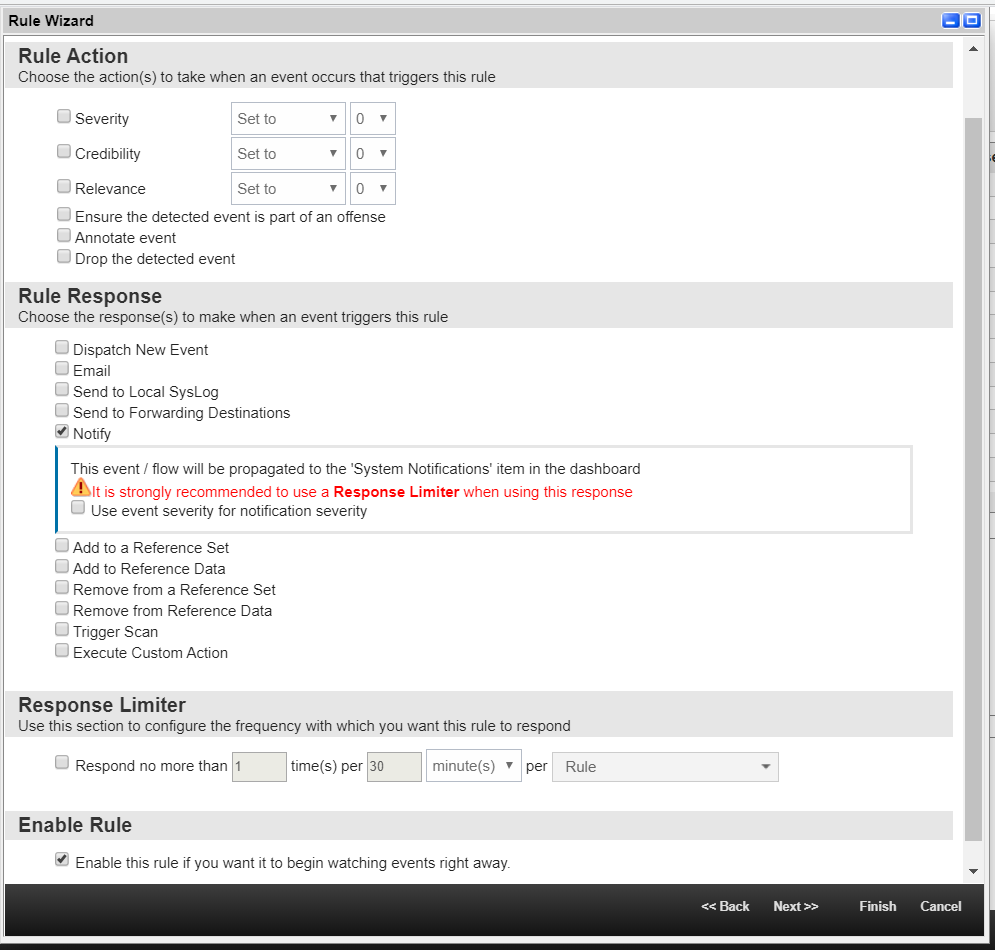
The Rule Editor page
- Click Next
- On the Rule Summary page, make sure that all settings are specified correctly, and click Finish.
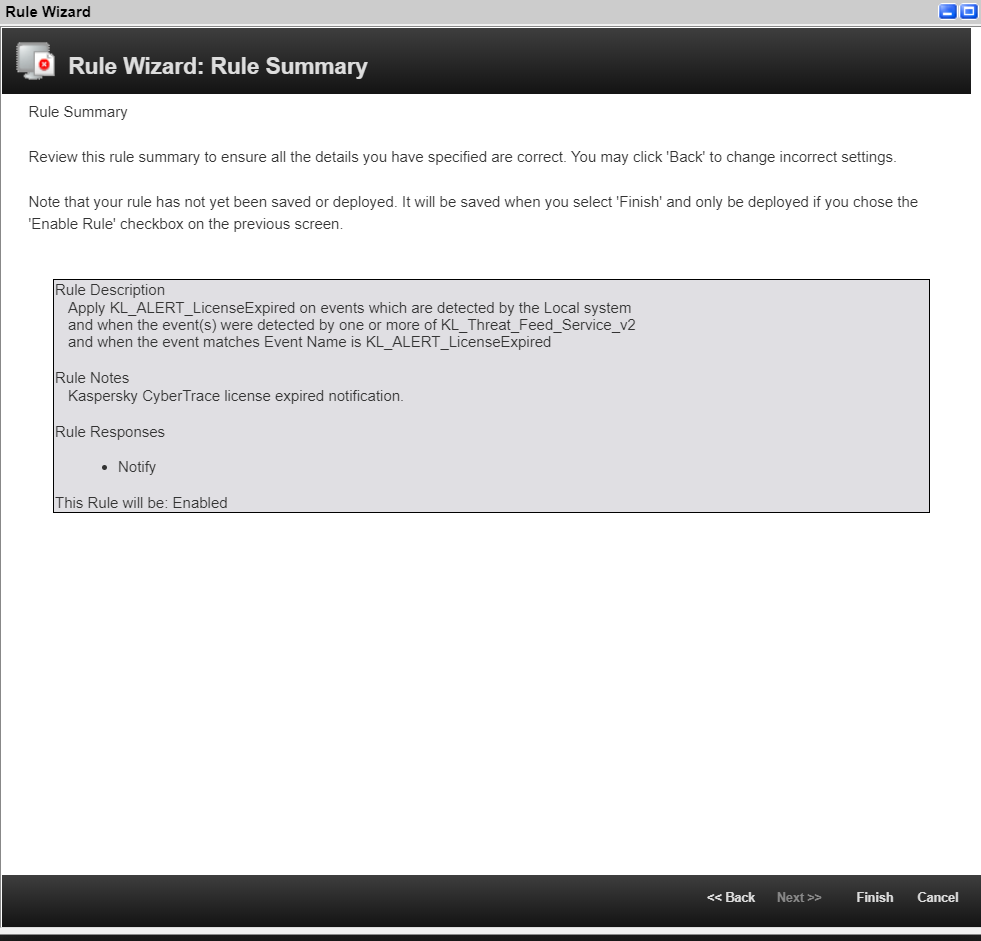
The Rule Summary page
The rule will now be added to the Rules list.
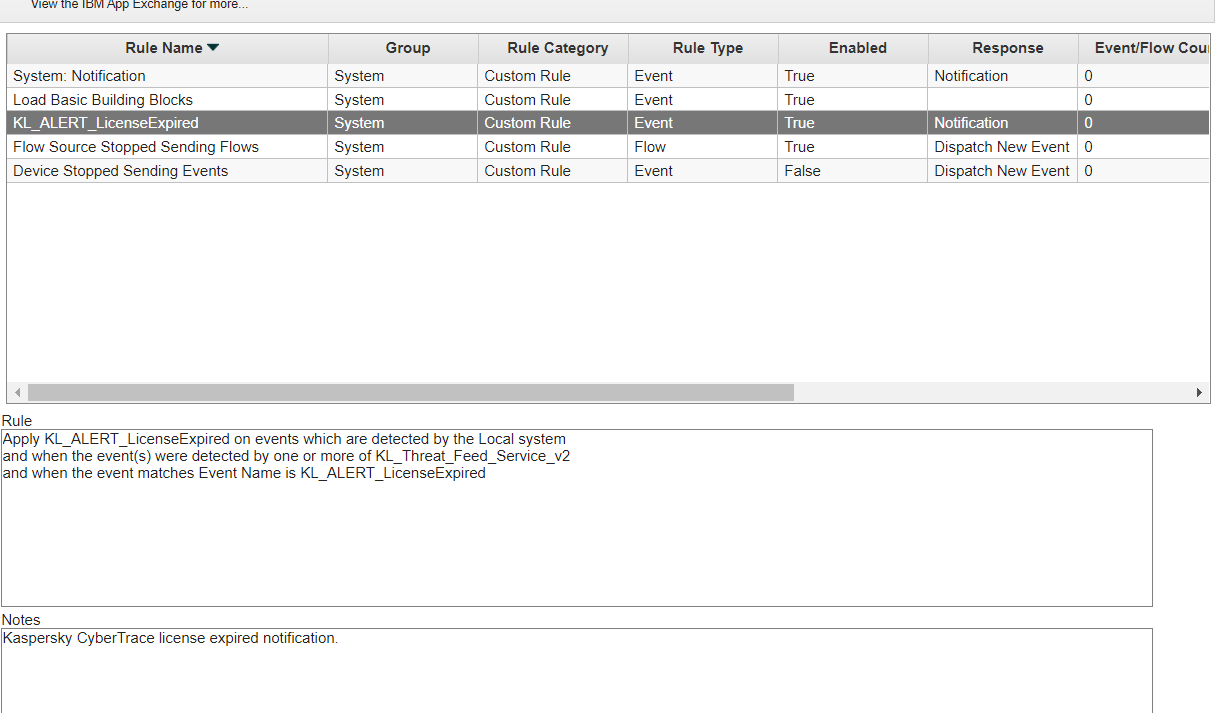
The Rules list
The added rule generates a notification about an incoming service event. You can browse these notifications by clicking the Messages drop-down list. Also, notifications are displayed in QRadar Console as a pop-up message.
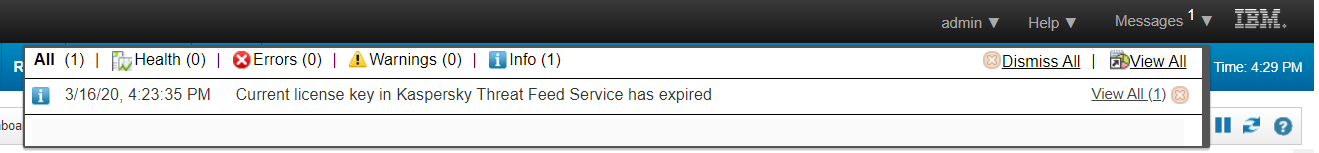
The Messages drop-down list
You can configure displaying of notifications on the Dashboard tab.
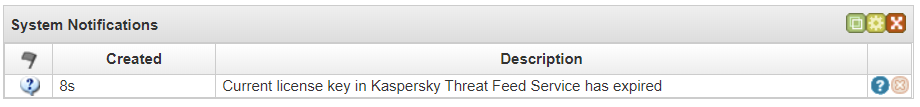
System notifications on the Dashboard tab
To configure displaying of notifications on the Dashboard tab:
- Select the Dashboard tab.
- In the Add Item drop-down list, select System Notifications.
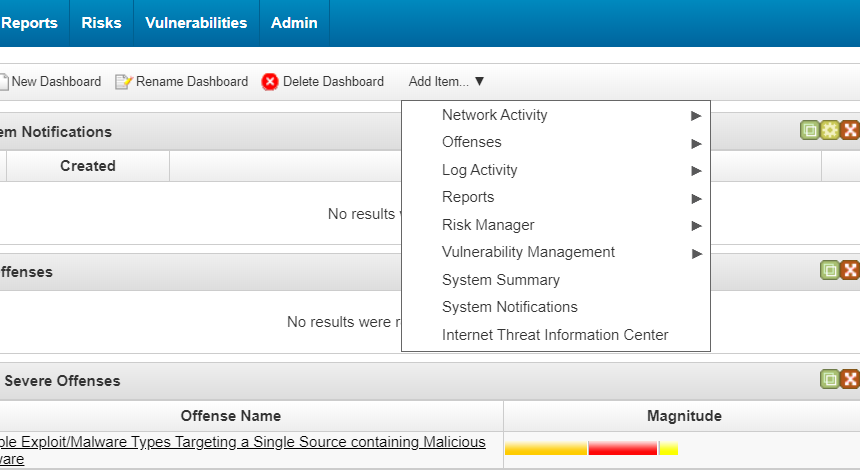
Adding system notifications on the Dashboard tab