Creating notifications about incoming service events
You can create notifications about incoming Kaspersky CyberTrace service events by configuring alert rules.
To create notifications about service events from Kaspersky CyberTrace in Splunk:
- On the Search and Reporting app for Splunk menu, select the Search tab.
- In the search box, specify a condition for creating alerts. For example:
sourcetype="kl_cybertrace_events" alert="KL_ALERT_ServiceStopped"This condition defines the request for searching events that are generated when Feed Service is stopped.
To get more information about all Kaspersky CyberTrace service events, see subsection "Types of alert events" of the "About output format settings" section.
- Click the Search button (
 ) to make sure that the specified request is performed correctly.
) to make sure that the specified request is performed correctly.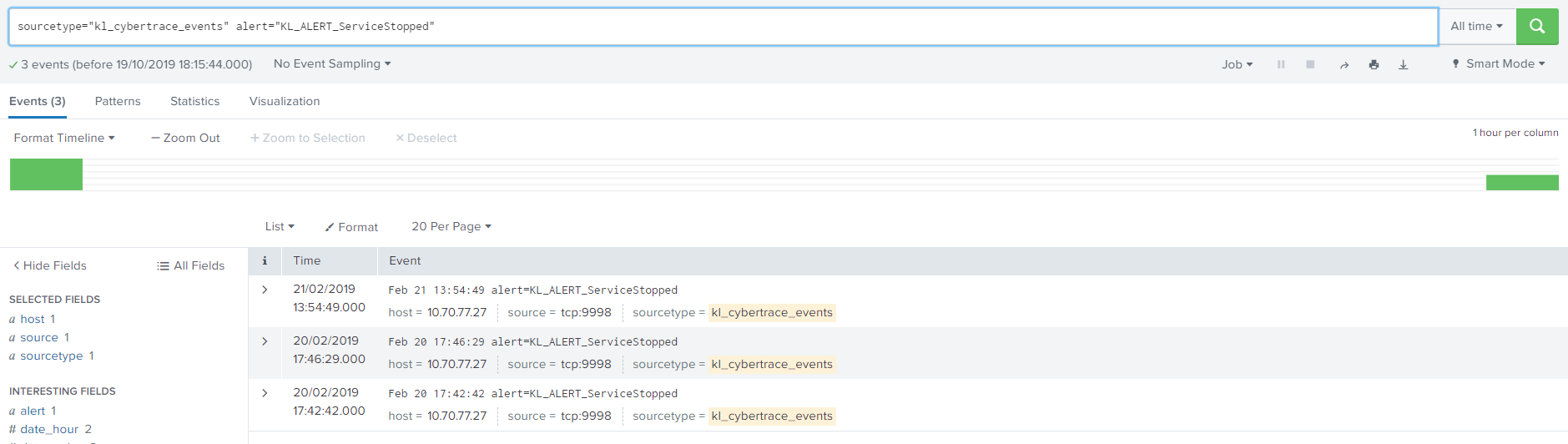
KL_ALERT_ServiceStopped events
- Click Save as and select Alert.
Saving alert
The Save As Alert window opens.
- In the Save As Alert window, specify the following settings:
- In the Title field, specify the name of the alert.
You can specify any title.
- In the Description field, specify the alert description.
You can specify any description.
- In the Alert type field select the one of the following:
- Scheduled—If you want to check events for matching the specified conditions regularly.
- Real-time—If you want to check events for matching the specified conditions in real time.
- In the Trigger field, specify For each results.
- Select the Throttle check box and then, if necessary, specify the amount of time during which Splunk will not send new alerts if the rule is triggered.
- In the Trigger Actions field, specify the way in which Splunk notifies when an alert is triggered.
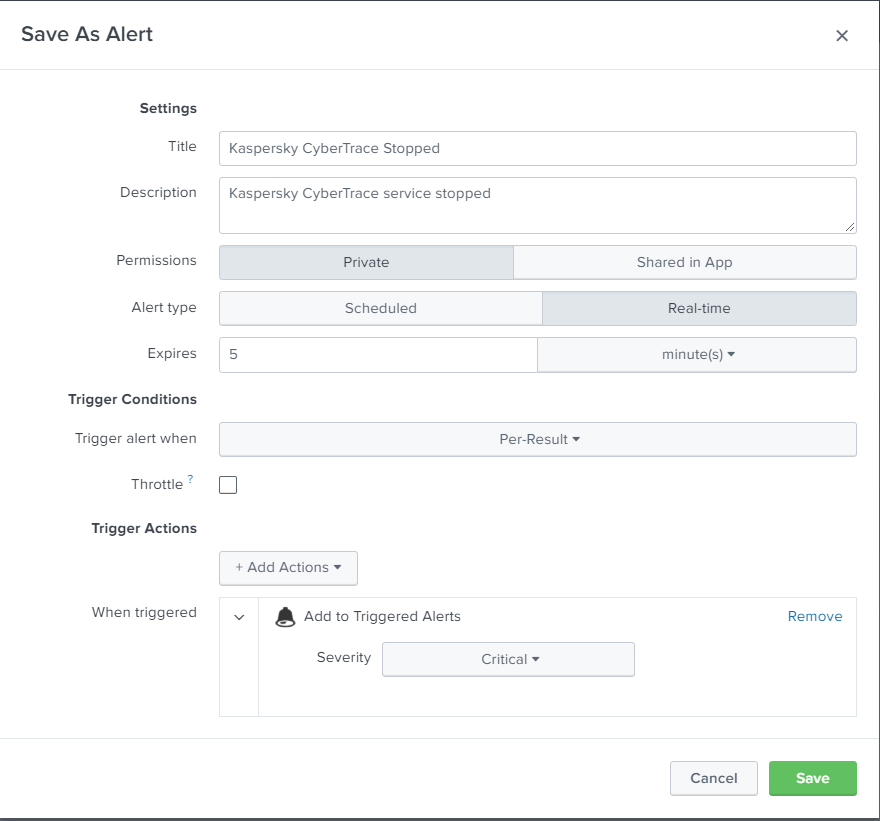
The Save As Alert window
- In the Title field, specify the name of the alert.
- Click Save.
The rule will now appear in Splunk.