Step 6. Creating a search filter for CyberTrace events
This section describes how to create an event search.
To create an event search:
- In QRadar Console, select the Log Activity tab.
- Select Search > New Search.
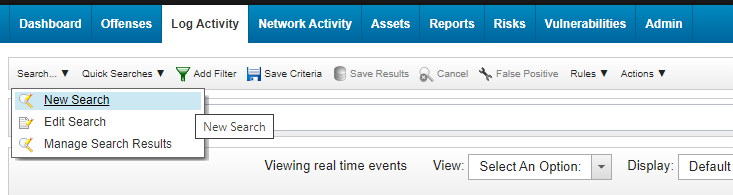
New search
- In the Column Definition form, add
MD5 (custom),SHA1 (custom),SHA256 (custom),URL (custom),IP (custom)from the Available Columns to the Columns list.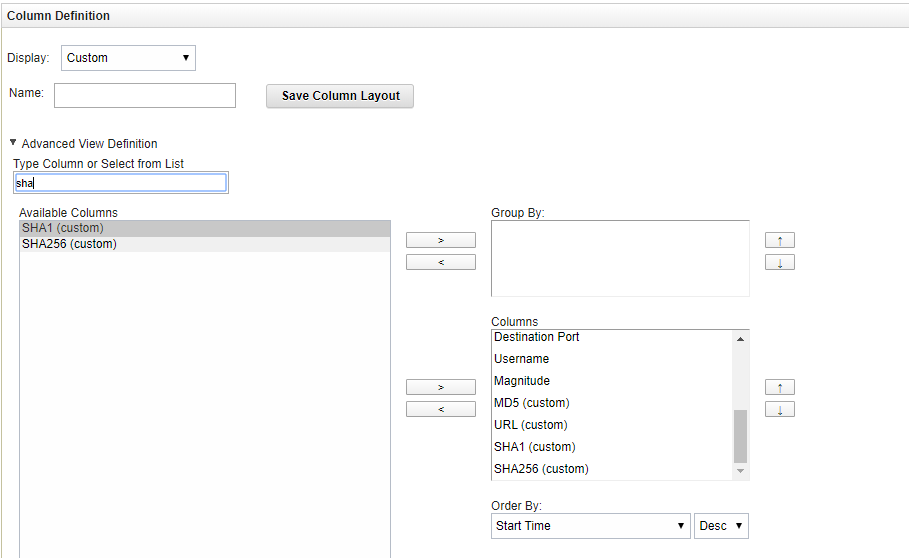
Defining columns
- Scroll down the page and in the Search Parameters form, set
KL_Threat_Feed_Service_v2as the log source:- In the Parameter drop-down list, select
Log Source [Indexed]. - In the Operator drop-down list, select
Equals. - In the Log Source list, select
KL_Threat_Feed_Service_v2.The selection
KL_Threat_Feed_Service_v2is the log source name that is set in theOutputSettings > EventFormatelement and theOutputSettings > AlertFormatelement of the Feed Service configuration file (you can also set them by using Kaspersky CyberTrace Web). - Click the Add Filter button.
The
Log Source is KL_Threat_Feed_Service_v2string will be added to the Current Filters list.
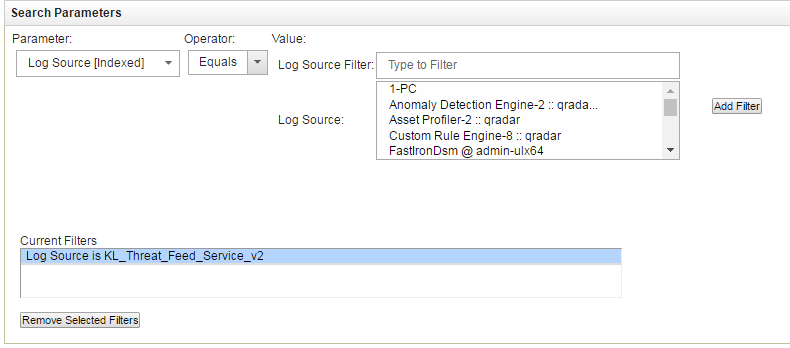
Setting the log source
- In the Parameter drop-down list, select
- Click either the Filter button or the Save button to display the search result.
- Click the Save Criteria button.
Save Criteria button
- In the Save Criteria form, type the name of the search in the Search Name text box, select the Include in my Quick Searches checkbox and then specify the analyzed interval for created search (for example, Real Time).
- Click OK.
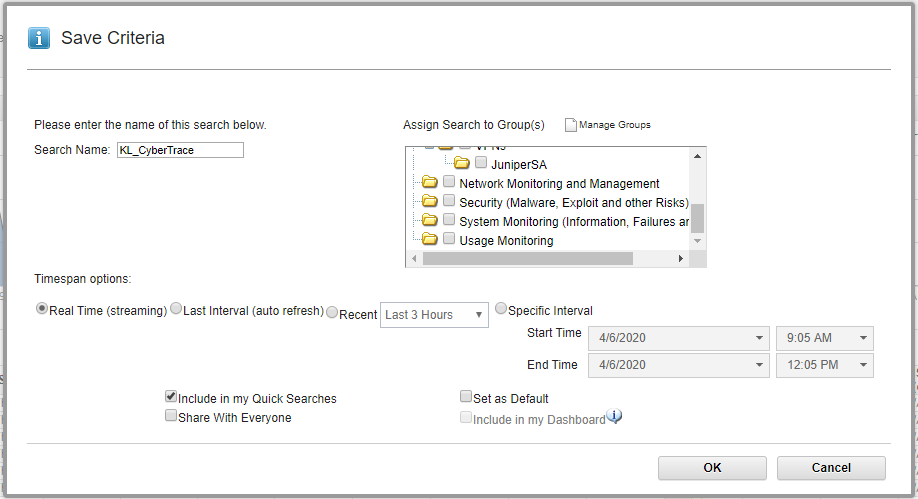
Saving criteria