Web Control
Web Control manages users' access to web resources. This helps reduce traffic and inappropriate use of work time. When a user tries to open a website that is restricted by Web Control, Kaspersky Endpoint Security will block access or show a warning (see the figure below).
To use Web Control, you must configure the application as follows:
- For HTTPS traffic monitoring, enable encrypted connections scan (enabled by default).
- Select HTTP and HTTPS ports that you want Kaspersky Endpoint Security to monitor (by default, port monitoring is enabled).
- Select the applications whose traffic you want Kaspersky Endpoint Security to monitor. Most browsers are already present in the list of applications recommended by Kaspersky (by default, monitoring is enabled for these browsers). If your browser is missing from the list, add it manually.
- We recommend to inject a web page interaction script into web traffic (by default, script injection is disabled). This script enables registration of Web Control events for the application event log, OS event log, and reports.
Methods for managing access to websites
Web Control lets you configure access to websites by using the following methods:
- Website category. Websites are categorized according to the Kaspersky Security Network cloud service, heuristic analysis, and the database of known websites (included in application databases). For example, you can restrict user access to the Social networks category or to other categories.
- Data type. You can restrict users' access to data on a website, and hide images, for example. Kaspersky Endpoint Security determines the data type based on the file format and not based on its extension.
Kaspersky Endpoint Security does not scan files within archives. For example, if image files were placed in an archive, Kaspersky Endpoint Security identifies the Archives data type and not Graphics.
- Individual address. You can enter a web address or use masks.
You can simultaneously use multiple methods for regulating access to websites. For example, you can restrict access to the "Office files" data type just for the Web-based email website category.
Website access rules
Web Control manages users' access to websites by using access rules. You can configure the following advanced settings for a website access rule:
- Users to which the rule applies.
For example, you can restrict Internet access through a browser for all users of the company except the IT department.
- Rule schedule.
For example, you can restrict Internet access through a browser during working hours only.
Access rule priorities
Each rule has a priority. The higher a rule is on the list, the higher its priority. If a website has been added to multiple rules, Web Control regulates access to the website based on the rule with the highest priority. For example, Kaspersky Endpoint Security may identify a corporate portal as a social network. To restrict access to social networks and provide access to the corporate web portal, create two rules: one block rule for the Social networks website category and one allow rule for the corporate web portal. The access rule for the corporate web portal must have a higher priority than the access rule for social networks.
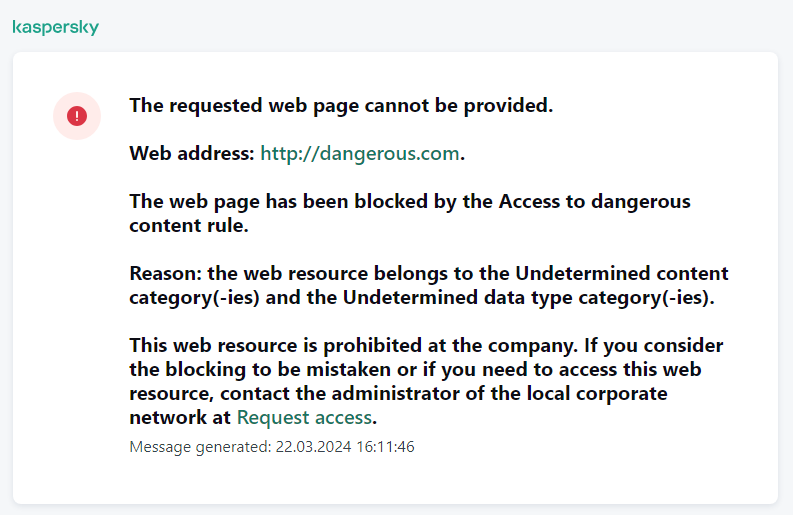
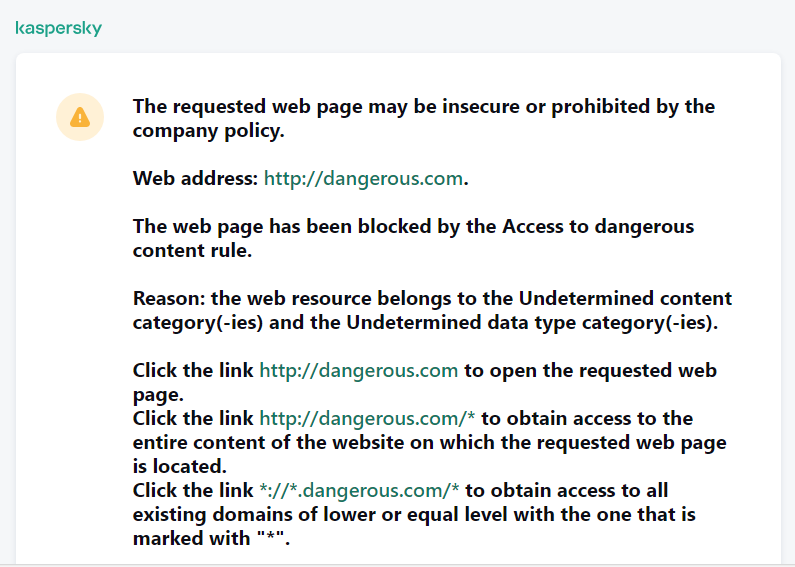
Web Control messages
Web Control component settings
Parameter |
Description |
|---|---|
Rules of access to web resources |
List containing web resource access rules. Each rule has a priority. The higher a rule is on the list, the higher its priority. If a website has been added to multiple rules, Web Control regulates access to the website based on the rule with the highest priority. |
Default rule |
The Default rule is a rule for accessing web resources that are not covered by any other rule. The following options are available:
|
Templates |
Warning. The entry field consists of a template of the message that is displayed if a rule for warning about attempts to access an unwanted web resource is triggered. Message about blocking. The entry field contains the template of the message that appears if a rule which blocks access to a web resource is triggered. Message to administrator. Template of the message to be sent to the LAN administrator if the user considers the block to be a mistake. After the user requests to provide access, Kaspersky Endpoint Security sends an event to Kaspersky Security Center: Web page access blockage message to administrator. The event description contains a message to administrator with substituted variables. You can view these events in the Kaspersky Security Center console using the predefined event selection User requests. If your organization does not have Kaspersky Security Center deployed or there is no connection to the Administration Server, the application will send a message to administrator to the specified email address. |
Log the opening of allowed pages |
Kaspersky Endpoint Security logs data on visits to all websites, including allowed websites. Kaspersky Endpoint Security sends events to Kaspersky Security Center, to the local log of Kaspersky Endpoint Security, and to the Windows Event log. To monitor user Internet activity, you need to configure the settings for saving events. Browsers that support the monitoring function: Microsoft Edge, Microsoft Internet Explorer, Google Chrome, Yandex Browser, Mozilla Firefox. User activity monitoring does not work in other browsers. Monitoring user Internet activity may require more computer resources when decrypting HTTPS traffic. |