General workflow
Kaspersky Threat Feed App for MISP works as follows:
- User runs the converter (
main.py) with the parameters specified in the "Command-line parameters" section. - The converter (
main.py) generates a configuration file for Feed Utility based on thetemplate.conffile. - Feed Utility is used to download feeds.
Feed Utility is a tool designed to simplify the process of downloading and filtering data feeds. Able to compare feed versions and apply rules from a configuration file, this tool is a core component of integration with the Kaspersky Data Feeds API. For more information, see the Feed Utility guide,
For information about filtering data feeds, see the "Filtering rules" section. The filtering rules can be configured in the
FEEDSparameter of thesettings.pyfile. - Once the converter has been initialized, the user uses the MISP UI to specify the path to the feed storage folder (see the "Loading converted feeds to MISP" section).
- To run the converter on a regular basis, the user can set up cron jobs via the command-line (see the "Scheduling feeds conversion" section).
- The feed's new records are converted to MISP-format files and saved to the "
workdir/%feed_name%" directory inside the converter's parent folder. - For each subsequent import, the difference between the versions is determined.
- During the update, revoked records are removed from the MISP instance via the REST API. Kaspersky Threat Feed App for MISP can perform two types of updates:
- Full diff
This is used for records with changed context fields. Depending on the feed type, the update may take a significant amount of time. The converter performs a full diff update only at intervals (in hours) defined by the full_update_interval_h parameter (see the "Command-line parameters" section).
- Partial diff
This update only adds records with new indicators of compromise (IOC) and deletes records with obsolete IOCs (the context is not updated). The converter performs this update at intervals defined by the schedule specified for the cron utility.
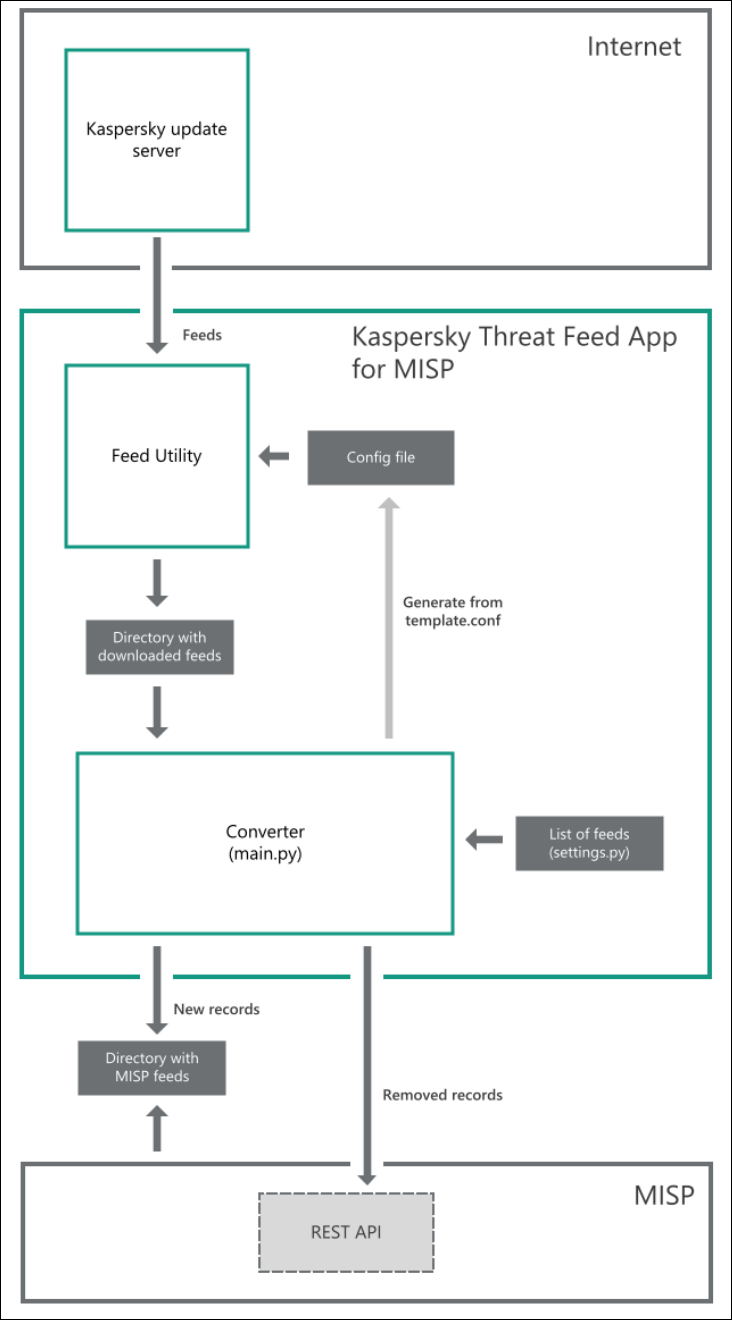
Kaspersky Threat Feed App for MISP workflow