Secure Logger example
The Secure Logger example demonstrates use of the Distrustful Decomposition pattern for separating event log read/write functionality.
Example architecture
The security goal of the Secure Logger example is to prevent any possibility of distortion or deletion of information from the event log. This example utilizes the capabilities provided by KasperskyOS to achieve this security goal.
A logging system can be examined by distinguishing the following functional steps:
- Generate information to be written to the log.
- Save information to the log.
- Read entries from the log.
- Provide entries in a convenient format for the consumer.
Accordingly, the logging subsystem can be divided into four processes depending on the required functional capabilities of each process.
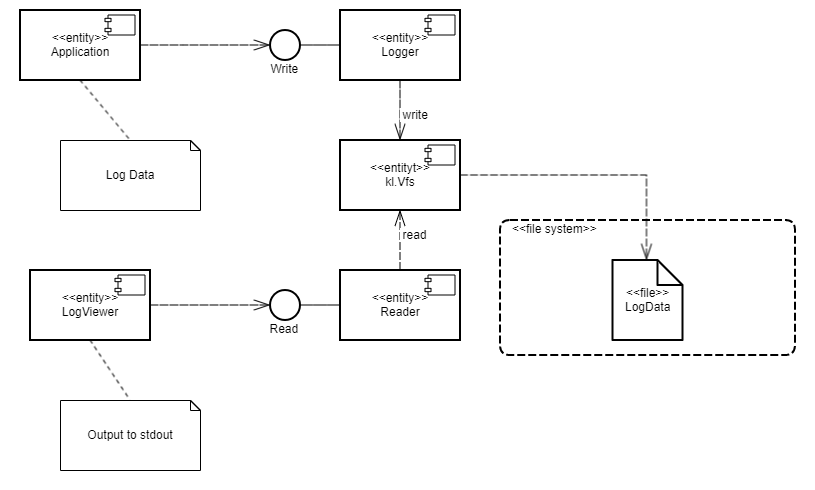
For this purpose, the Secure Logger example contains the following four programs: Application, Logger, Reader and LogViewer.
- The
Applicationprogram initiates the creation of entries in the event log maintained by theLoggerprogram. - The
Loggerprogram creates entries in the log and writes them to the disk. - The
Readerprogram reads entries from the disk to send them to theLogViewerprogram. - The
LogViewerprogram sends entries to the user.
The IPC interface provided by the Logger program is intended only for writing to storage. The IPC interface of the Reader program is intended only for reading from storage. The example architecture looks as follows:
- The
Applicationprogram uses the interface of theLoggerprogram to save log entries. - The
LogViewerprogram uses the interface of theReaderprogram to read the log entries and present them to a user.
The LogViewer program normally has external channels for interacting with a user (for example, to receive data write commands and to provide data to a user). Naturally, this program is an untrusted component of the system, and therefore could potentially be used to conduct an attack. However, even if a successful attack results in the infiltration of unauthorized executable code into the LogViewer program, information in the log cannot be distorted through this program. This is because the program can only utilize the data read interface, which cannot actually be used to distort or delete data. Moreover, the LogViewer program does not have the capability to gain access to other interfaces because this access is controlled by the security module.
A security policy in the Secure Logger example has the following characteristics:
- The
Applicationprogram has the capability to query theLoggerprogram to create a new entry in the event log. - The
LogViewerprogram has the capability to query theReaderprogram to read entries from the event log. - The
Applicationprogram does not have the capability to query theReaderprogram to read entries from the event log. - The
LogViewerprogram does not have the capability to query theLoggerprogram to create a new entry in the event log.
Example files
The code of the example and build scripts are available at the following path:
/opt/KasperskyOS-Community-Edition-<version>/examples/secure_logger
Building and running example
See Building and running examples section.