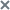Searching events in source code mode
April 2, 2024
ID 247637
To define event search conditions in source code mode:
- In the application web interface window, select the Threat Hunting section, Source code tab.
This opens a form containing the field for entering event search conditions in source code mode.
- Enter the event search conditions using criteria, operators, logical operators
ORandAND, and parentheses to group conditions.A search condition must conform to the following syntax:
<criterion> <operator> <criterion value>.Example:
EventType = "filechange"AND (FileName CONTAINS "example"OR UserName = "example") - If you want to hide newline special characters in the editor window, click Convert special characters to line breaks
 . If you want to display newline characters, click Convert line breaks to special characters
. If you want to display newline characters, click Convert line breaks to special characters .
.When using a complex search condition consisting of multiple criterion values, in the source code editing window, each criterion value must start on a new line. To display line breaks, Kaspersky Anti Targeted Attack Platform uses line separator special characters (^r ^n). To perform an event search correctly, you must make sure the line separator special characters are correctly arranged.
- If you want to search events that occurred during a specific period, click the Any time button and select one of the following event search periods:
- Any time if you want the table to display events found as far back as the records go.
- Last hour if you want the table to display events that were found during the last hour.
- Last day if you want the table to display events found during the last day.
- Custom range if you want the table to display events found during the period you specify.
- If you selected Custom range:
- In the calendar that opens, specify the start and end dates of the event display range.
- Click Apply.
The calendar closes.
- Click Search.
The table of events that satisfy the search criteria is displayed.
If you are using the distributed solution and multitenancy mode, found events are grouped in tiers: Server – Tenant names – Server names.
- Click the name of the server for which you want to view events.
The host table of the selected server is displayed. Event grouping levels are displayed above the table.