Creating an On-Demand Scan task
To start creating a new custom On-Demand Scan task:
- Open the Settings window in the New Task Wizard.
- Select the required Task creation method.
- Click the Next button.
- Create a scan scope in the Scan scope window:
By default, the scan scope includes critical areas of the protected device. Scan scopes are marked in the table with the icon
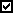 . Excluded scan scopes are marked with the
. Excluded scan scopes are marked with the  icon in the table.
icon in the table.You can change the scan scope: add specific preset scan scopes, disks, folders, network objects and files and assign specific security settings for each scope added.
- To exclude all critical areas from the scan, open the context menu on each of the lines and select the Remove scope option.
- To include a predefined scan scope, disk, folder, network object, or file in the scan scope:
- Right-click the Scan scope table and select Add scope or click the Add button.
- In the Add objects to the scan scope window, select a predefined scope in the Predefined scope list, specify the protected device drive, folder, network object, or file on the protected device or on another protected device in the network, and click the OK button.
- To exclude subfolders or files from the scan, select the added folder (disk) in the Scan scope window of the wizard:
- Open the context menu and select the Configure option.
- Click the Settings button in the Security level window.
- On the General tab in the On-demand scan settings window clear the Subfolders and Subfiles check boxes.
- To change scan scope security settings:
- Open the context menu on the scope whose settings you wish to configure, and select Configure.
- In the On-demand scan settings window, select one of the predefined security levels, or click the Settings button to configure security settings manually.
Security settings are configured the same way as for the Real-Time File Protection task.
- To skip embedded objects in the added scan scope:
- Open the context menu on the Scan scope table, select Add exclusion.
- Specify the objects to exclude: select a predefined scope in the Predefined scope list, and specify the protected device disk, folder, network object, or file on the protected device or on another protected device in the network.
- Click the OK button.
- In the Options window, configure the heuristic analyzer and integration with other components:
- Configure use of the heuristic analyzer.
- Select the Apply Trusted Zone check box, if you want to exclude objects added to the Trusted Zone list from the scan scope of the task.
- Select the Use KSN for scanning check box, if you want to use Kaspersky Security Network cloud services for the task.
- To assign Low priority to the working process in which the task will be executed, select the Perform task in background mode check box in the Options window.
By default, the working processes in which Kaspersky Embedded Systems Security for Windows tasks are run have Medium (Normal) priority.
- To use the created task as a Critical Areas Scan task, select the Consider task as critical areas scan check box in the Options window.
- Click the Next button.
- In the Schedule window, specify the task start schedule settings.
- Click the Next button.
- In the Selecting an account to run the task window, specify the account you want to use.
- Click the Next button.
- Specify a task name.
- Click the Next button.
The task name should be no longer than 100 characters and cannot contain the following symbols: " * < > & \ : |
The Finish creating the task window opens.
- You can optionally run the task after the Wizard finishes by selecting the Run task after Wizard finishes check box.
- Click the Finish button to finish creating the task.
The new On-Demand Scan task will be created for the selected protected device or a group of protected devices.