Example of analyzing a threat development chain graph
August 2, 2024
ID 213463
This section contains an example of a threat development chain graph and how you can use it for analyzing an attack on your users' devices.
Let's consider an attack using a phishing email message that contains an attachment. The attachment is an executable file.
The user saves and runs the file on his or her device. Kaspersky Endpoint Security for Windows makes a detection of the Malicious object detected type.
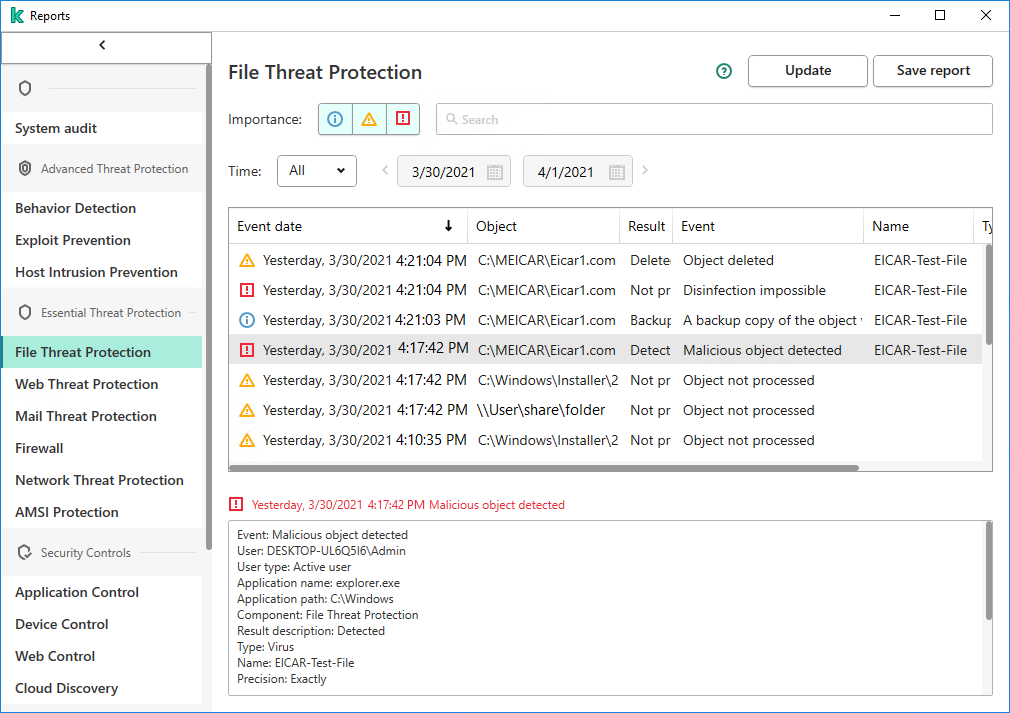
A detection in Kaspersky Endpoint Security for Windows
The Root-Cause Analysis widget shows up to 10 detections.
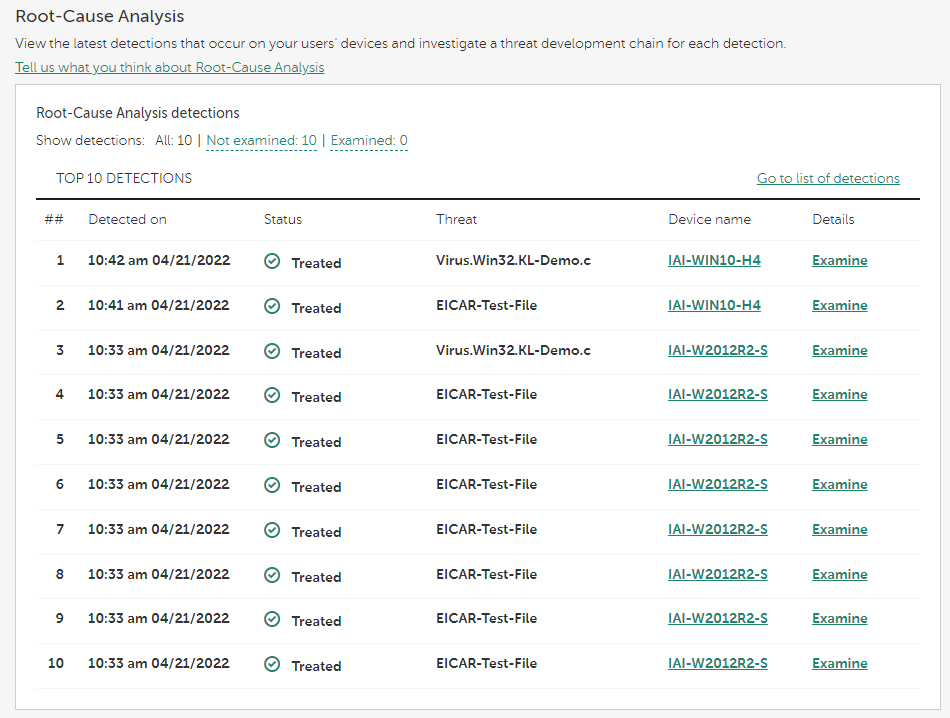
Root-Cause Analysis widget
By clicking the Examine link in the required line of the widget, you can proceed to a threat development chain graph.
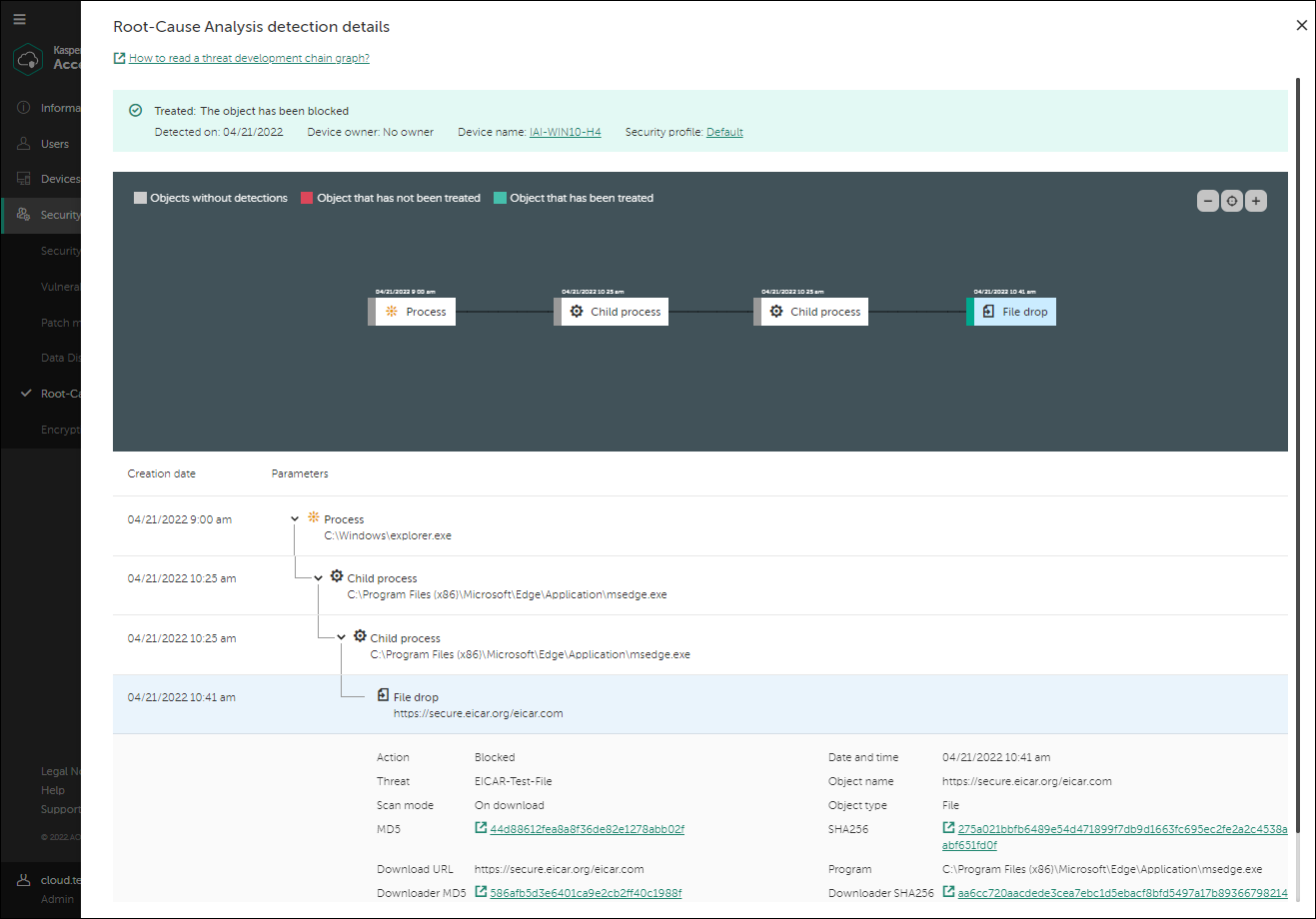
A threat development chain graph
The threat development chain graph provides you with information about the detection, for example: actions that occurred on the device during the detection, category of the detected threat, the file origin (in this example, an email), the user who downloaded the file (in this example, an administrator). Also, the chain graph shows that additional files were created on the device, that several network connections were established, and that some registry keys were changed.
Based on this information, you can do the following:
- Verify the settings of the mail server.
- Add the email message sender to the denylist (if the sender is external), or address him or her directly (if the sender is internal).
- Check whether other devices have connected to the same IP addresses.
- Add these IP addresses to the denylist.
When you click a link in the SHA256, MD5, IP address, or URL fields in the detailed information about a file, you are taken to the Kaspersky Threat Intelligence Portal https://opentip.kaspersky.com/. The Portal shows that the detected file is neither a threat nor a known file.
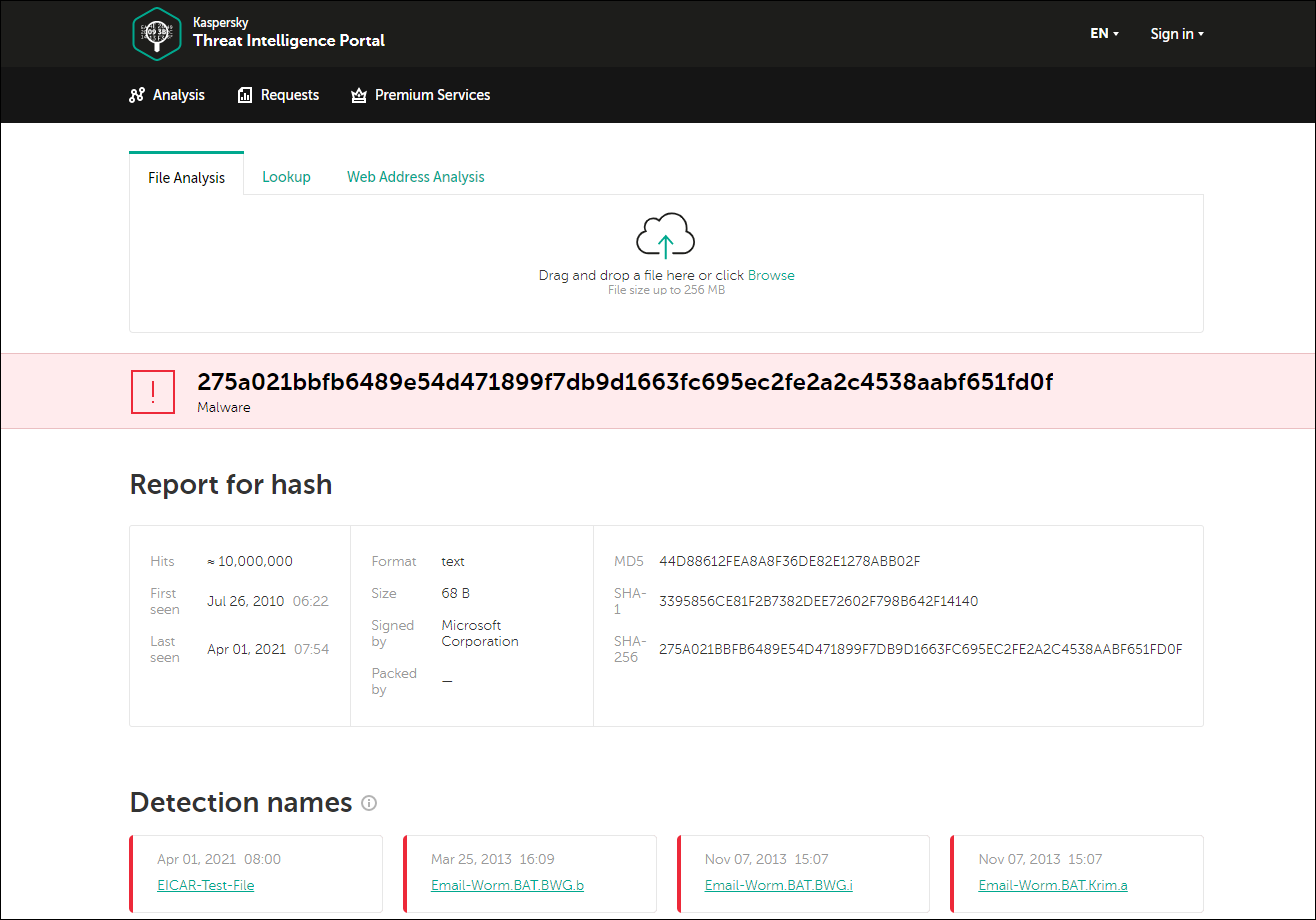
Kaspersky Threat Intelligence Portal
This example shows the importance of the Root-Cause Analysis feature. The parent file of the detected file is untrusted, but it is not a malicious one. It means that it has not been detected by Kaspersky Endpoint Security for Windows. This file is still present on the device and within the organization. If the organization has devices on which some protection components are disabled (for example, Behavior Detection) or on which anti-malware databases are not up-to-date, the malicious activity of the parent file will not be detected and the criminals may have a chance to penetrate your organization's infrastructure.
