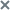Configuring the Driver Interceptor mode
To configure the Driver Interceptor mode:
- Open the Task settings window.
- On the General tab, select the Driver Interceptor mode.
- In the Task mode settings block, configure the following settings:
- Check safe connections through the HTTPS protocol.
Scanning is available only if the HTTPS port is open.
- Select the versions of the cryptographic protocol that you want to use:
- TLS 1.0
- TLS 1.1
- TLS 1.2
All versions are selected by default. Moreover, the TLS 1.0 option cannot be disabled.
Note, that you can use the TLS protocol in the Traffic Security task configuration only on protected devices running Microsoft Windows 7 or later, Microsoft Windows Server 2008 R2 or later.
- Do not trust web-servers with invalid certificate.
If the Do not trust web-servers with invalid certificate check box is selected, Kaspersky Security for Windows Server blocks all connections with invalid certificates and also all connections with self signed certificate.
- Security port.
- Check safe connections through the HTTPS protocol.
- To add or exclude ports from the interception area, click the Configure interception area button.
The Interception area window opens.
- Select one of the following options on the Intercept ports tab:
- Intercept all
- Intercept specified ports:
- Enter the port number in the text field. You can add several ports by using a semicolon delimiter between port numbers.
- Click Add.
Port is included in the interception area.
By default, Kaspersky Security for Windows Server intercepts traffic that is transferred via the following ports: 80, 8080, 3128, 443.
If you run Traffic Security task in Driver Interceptor mode with the Intercept all option enabled, make sure to configure the Kaspersky Security Center Administration Server to use the default port (13299) for connection with the Kaspersky Security Center Web Console (for more information, refer to Kaspersky Security Center Online Help), or, if you use a custom port, make sure to add this port to the Traffic Security task's list of excluded ports. Otherwise, Traffic Security blocks the connection from the Kaspersky Security Center Web Console to the Kaspersky Security Center Administration Server.
- To specify ports you want to exclude from the interception area on the Exclude ports tab:
- Enter the port number in the text field. You can add several ports by using a semicolon delimiter between port numbers.
- Click Add.
Port is excluded from the area.
By default, Kaspersky Security for Windows Server excludes ports which are used by other applications and might cause issues when attempting to read data transferred via encrypted connection: 3389, 1723, 13291, 13299.
- To exclude IP addresses from the interception area on the Exclude IP addresses tab:
- Enter IP addresses in IPv4 format (in a short form or specifying an address with a subnet mask).
- Click Add.
- Click OK to save the changes.
- To exclude process or executable file which requires traffic exchange on the Exclude processes tab:
- Select the Apply exclusions for processes check box.
- To exclude a file:
- Click the Executable files button.
The standard Open windows is displayed.
- Select the executable file you want to exclude and click Open.
- Click the Executable files button.
- In the Interception area window click the OK button.
- In the Task settings window click the OK button.
The task mode configuration is saved.
Page top