Editing the list of trusted applications
The list of trusted applications is a list of applications whose file and network activity (including malicious activity) and access to the system registry are not monitored by Kaspersky Endpoint Security. By default, Kaspersky Endpoint Security monitors objects that are opened, executed, or saved by any application process and controls the activity of all applications and network traffic that is generated by them. After an application is added to the list of trusted applications, Kaspersky Endpoint Security stops monitoring the application's activity.
The difference between scan exclusions and trusted applications is that for exclusions Kaspersky Endpoint Security does not scan files, while for trusted applications it does not control the initiated processes. If a trusted application creates a malicious file in a folder which is not included in scan exclusions, Kaspersky Endpoint Security will detect the file and eliminate the threat. If the folder is added to exclusions, Kaspersky Endpoint Security will skip this file.
For example, if you consider objects that are used by the standard Microsoft Windows Notepad application to be safe, meaning that you trust this application, you can add Microsoft Windows Notepad to the list of trusted applications so that the objects used by this application are not monitored. This will increase computer performance, which is especially important when using server applications.
In addition, certain actions that are classified by Kaspersky Endpoint Security as suspicious may be safe within the context of the functionality of a number of applications. For example, the interception of text that is typed from the keyboard is a routine process for automatic keyboard layout switchers (such as Punto Switcher). To take account of the specifics of such applications and exclude their activity from monitoring, we recommend that you add such applications to the trusted applications list.
Trusted applications help to avoid compatibility issues between Kaspersky Endpoint Security and other applications (for example, the problem of double-scanning of the network traffic of a third-party computer by Kaspersky Endpoint Security and by another anti-virus application).
At the same time, the executable file and process of the trusted application are still scanned for viruses and other malware. An application can be fully excluded from Kaspersky Endpoint Security scanning by means of scan exclusions.
How to add an application to the trusted list in the Administration Console (MMC)
- Open the Kaspersky Security Center Administration Console.
- In the console tree, select Policies.
- Select the necessary policy and double-click to open the policy properties.
- In the policy window, select General settings → Exclusions.
- In the Scan exclusions and trusted applications block, click the Settings button.
- In the window that opens, select the Trusted applications tab.
This opens a window containing a list of trusted applications.
- Select the Merge values when inheriting check box if you want to create a consolidated list of trusted applications for all computers in the company. The lists of trusted applications in the parent and child policies will be merged. The lists will be merged provided that merging values when inheriting is enabled. Trusted applications from the parent policy are displayed in child policies in a read-only view. Changing or deleting trusted applications of the parent policy is not possible.
- Select the Allow use of local trusted applications check box if you want to enable the user to create a local list of trusted applications. This way, a user can create their own local list of trusted applications in addition to the general list of trusted applications generated in the policy. An administrator can use Kaspersky Security Center to view, add, edit, or delete list items in the computer properties.
If the check box is cleared, the user can access only the general list of trusted applications generated in the policy.
- Click Add.
- In the window that opens, enter the path to the executable file of the trusted application (see the figure below).
Kaspersky Endpoint Security supports environment variables and the * and ? characters when entering a mask.
Kaspersky Endpoint Security does not support the %userprofile% environment variable when generating a list of trusted applications on the Kaspersky Security Center console. To apply the entry to all user accounts, you can use the * character (for example, C:\Users\*\Documents\File.exe). Whenever you add a new environment variable, you need to restart the application.
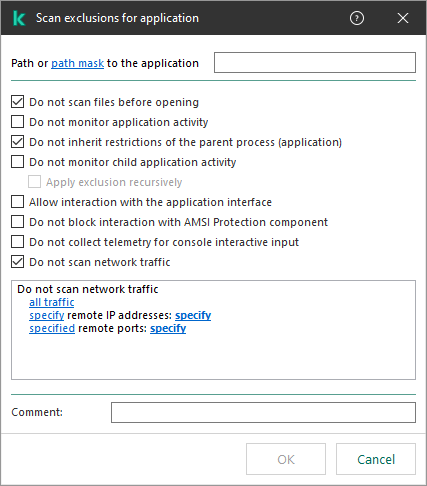
Trusted application settings
- Configure the advanced settings for the trusted application (see the table below).
- You can use the check box to exclude an application from the trusted zone at any time (see the figure below).
- Save your changes.
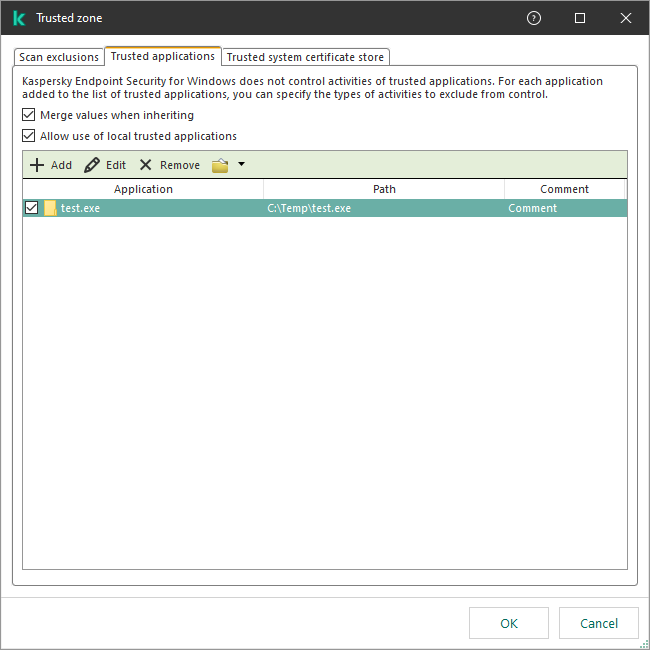
List of trusted applications
How to add an application to the trusted list in the Web Console and Cloud Console
- In the main window of the Web Console, select Devices → Policies & Profiles.
- Click the name of the Kaspersky Endpoint Security policy.
The policy properties window opens.
- Select the Application settings tab.
- Go to General settings → Exclusions and types of detected objects.
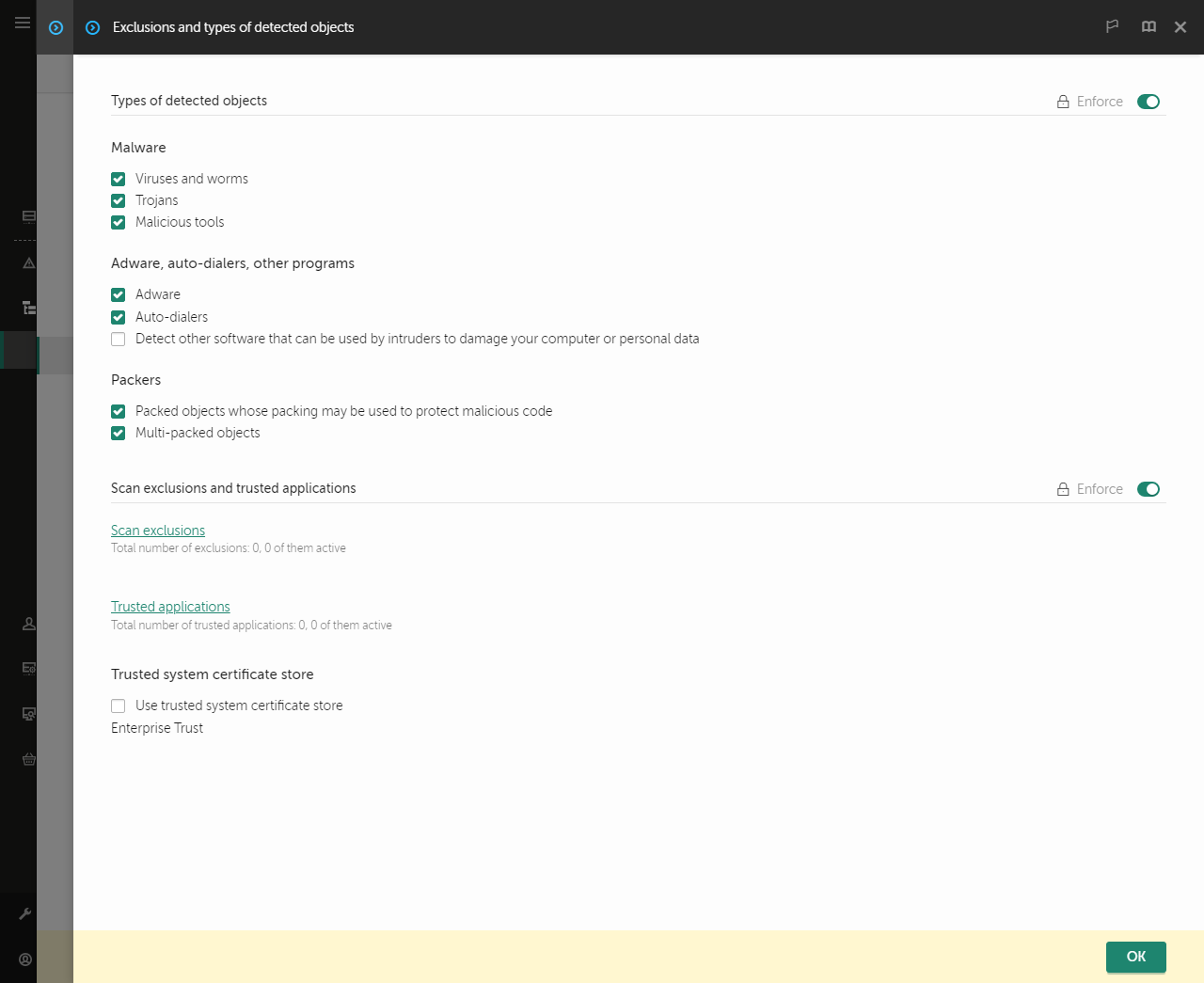
Settings of exclusions
- In the Scan exclusions and trusted applications block, click the Trusted applications link.
This opens a window containing a list of trusted applications.
- Select the Merge values when inheriting check box if you want to create a consolidated list of trusted applications for all computers in the company. The lists of trusted applications in the parent and child policies will be merged. The lists will be merged provided that merging values when inheriting is enabled. Trusted applications from the parent policy are displayed in child policies in a read-only view. Changing or deleting trusted applications of the parent policy is not possible.
- Select the Allow use of local trusted applications check box if you want to enable the user to create a local list of trusted applications. This way, a user can create their own local list of trusted applications in addition to the general list of trusted applications generated in the policy. An administrator can use Kaspersky Security Center to view, add, edit, or delete list items in the computer properties.
If the check box is cleared, the user can access only the general list of trusted applications generated in the policy.
- Click the Add button.
- In the window that opens, enter the path to the executable file of the trusted application (see the figure below).
Kaspersky Endpoint Security supports environment variables and the * and ? characters when entering a mask.
Kaspersky Endpoint Security does not support the %userprofile% environment variable when generating a list of trusted applications on the Kaspersky Security Center console. To apply the entry to all user accounts, you can use the * character (for example, C:\Users\*\Documents\File.exe). Whenever you add a new environment variable, you need to restart the application.
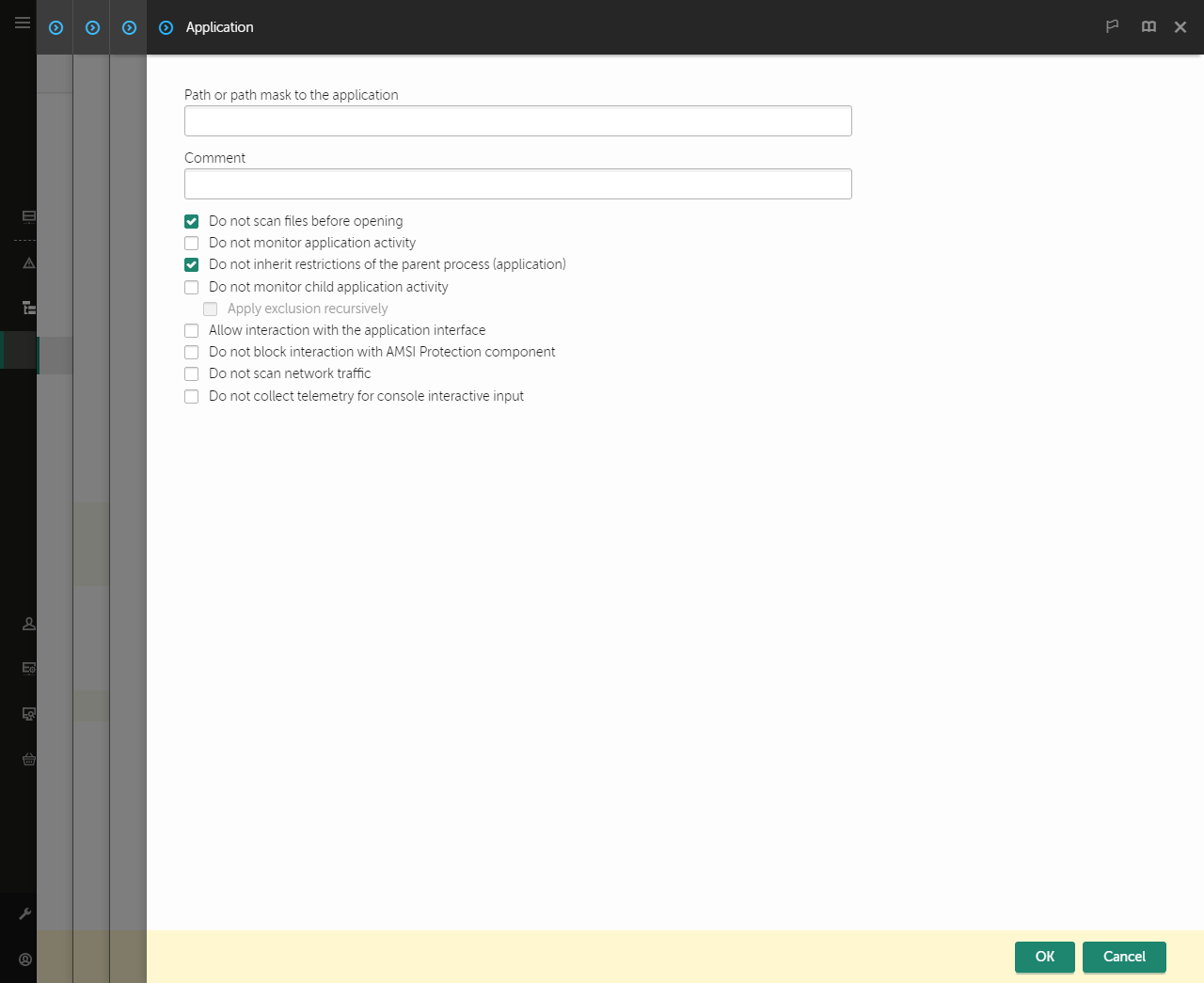
Trusted application settings
- Configure the advanced settings for the trusted application (see the table below).
- You can use the check box to exclude an application from the trusted zone at any time (see the figure below).
- Save your changes.
How to add an application to the trusted list in the application interface
- In the main application window, click the
 button.
button. - In the application settings window, select General settings → Exclusions and types of detected objects.
- In the Exclusions block, click the Specify trusted applications link.
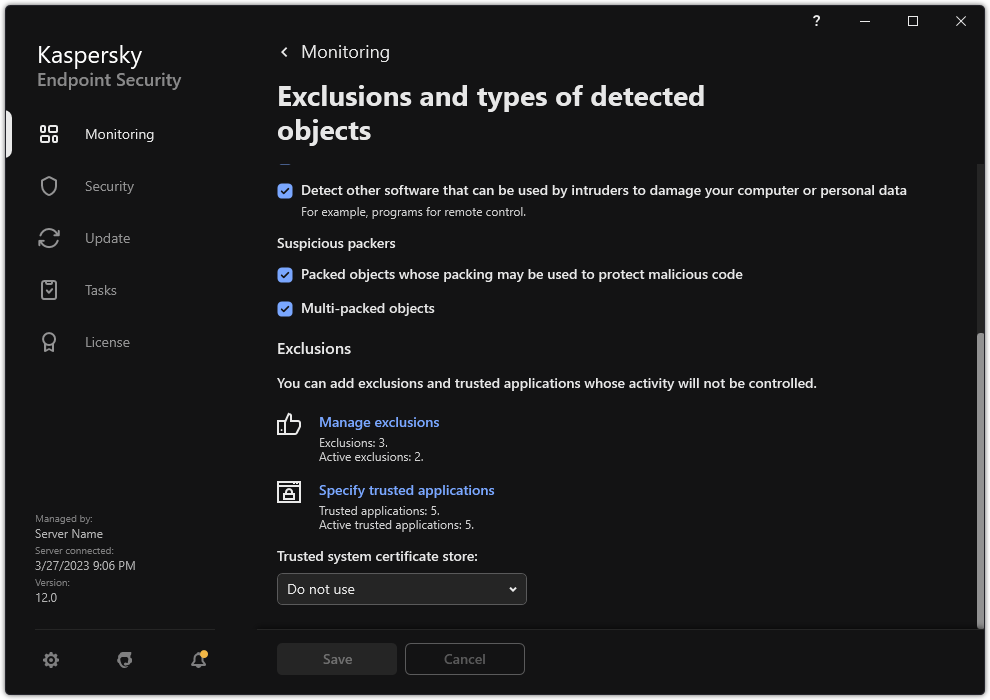
Settings of exclusions
- In the window that opens, click the Add button.
- Select the executable file of the trusted application.
You can also enter the path manually. Kaspersky Endpoint Security supports environment variables and the * and ? characters when entering a mask.
Kaspersky Endpoint Security supports environment variables and converts the path in the local interface of the application. In other words, if you enter the file path %userprofile%\Documents\File.exe, a C:\Users\Fred123\Documents\File.exe record is added in local interface of the application for user Fred123. Accordingly, Kaspersky Endpoint Security ignores the File.exe trusted program for other users. To apply the entry to all user accounts, you can use the * character (for example, C:\Users\*\Documents\File.exe).
Whenever you add a new environment variable, you need to restart the application.
- In the trusted application properties window, configure the advanced settings (see the table below).
- You can use the toggle to exclude an application from the trusted zone at any time (see the figure below).
- Save your changes.
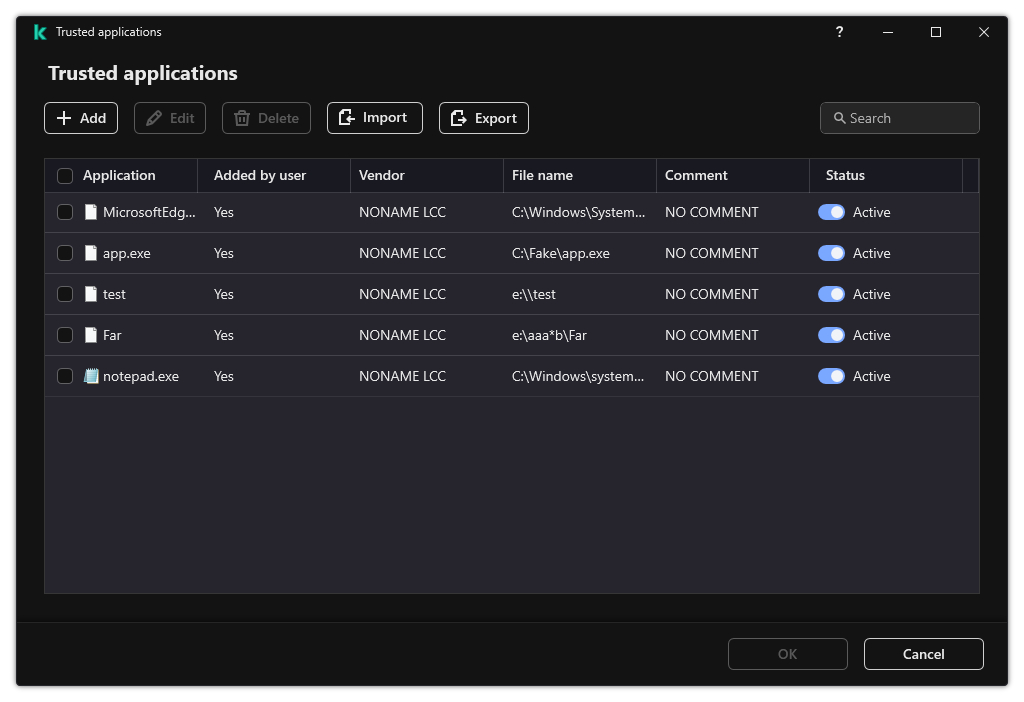
List of trusted applications
Trusted application settings
Parameter
|
Description
|
Do not scan files before opening
|
All files that are opened by the application are excluded from scans by Kaspersky Endpoint Security. For example, if you are using applications to back up files, this feature helps reduce the consumption of resources by Kaspersky Endpoint Security.
|
Do not monitor application activity
|
Kaspersky Endpoint Security will not monitor the application's file- and network activity in the operating system. Application activity is monitored by the following components: Behavior Detection, Exploit Prevention, Host Intrusion Prevention, Remediation Engine and Firewall.
|
Do not inherit restrictions from the parent process (application)
|
The restrictions configured for the parent process will not be applied by Kaspersky Endpoint Security to a child process. The parent process is started by an application for which application rights (Host Intrusion Prevention) and application network rules (Firewall) are configured.
|
Do not monitor child application activity
|
Kaspersky Endpoint Security will not monitor the file activity or network activity of applications that are started by this application.
|
Allow interaction with the application interface
|
Kaspersky Endpoint Security Self-Defense blocks all attempts to manage application services from a remote computer. If the check box is selected, the remote access application is allowed to manage Kaspersky Endpoint Security settings through the Kaspersky Endpoint Security interface.
|
Do not block interaction with AMSI Protection component
|
Kaspersky Endpoint Security will not monitor the trusted application's requests for objects to be scanned by the AMSI Protection component.
|
Do not collect telemetry for console interactive input
|
Kaspersky Endpoint Security does not send telemetry data about managing the application on the console. Telemetry data is used by Kaspersky Anti Targeted Attack Platform (EDR).
|
Do not scan network traffic
|
Network traffic initiated by the application will be excluded from scans by Kaspersky Endpoint Security. You can exclude either all traffic or only encrypted traffic from scans. You can also exclude individual IP addresses and port numbers from scans.
|
Comment
|
If necessary, you can provide a brief comment for the trusted application. Comments help simplify searches and sorting of trusted applications.
|
Status
|
Status of the trusted application:
- Active status means that the application is in the trusted zone.
- Inactive status means that the application is excluded from the trusted zone.
|
Page top





