Device Access example
The Device Access example demonstrates use of the Privilege Separation pattern.
Example architecture
The example contains the following three programs: Device, LoginManager and Storage.
In this example, the Device program queries the Storage program to receive information and queries the LoginManager program for authorization.
The Device program obtains access to the Storage program after successful authorization.
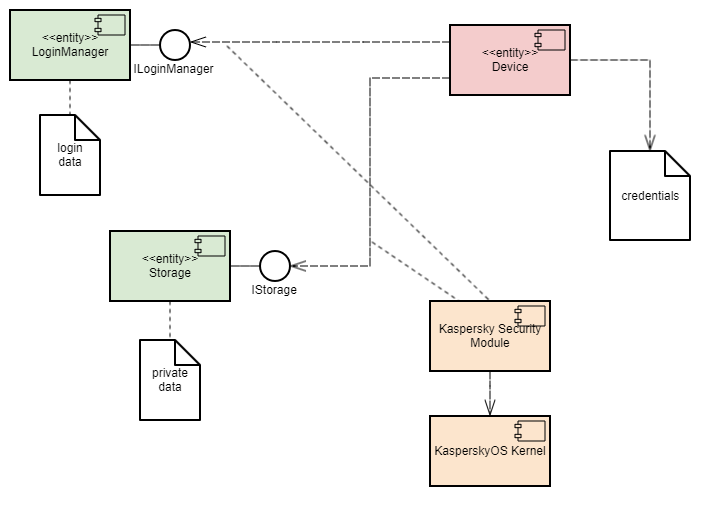
This example demonstrates the capability to separate the authorization logic and the data access logic into independent components. This separation guarantees that data access can be opened only after successful authorization. The security module monitors whether authorization was successfully completed. This architecture also enables independent development and testing of the authorization logic and the data access provision logic.
A security policy in the Device Access example has the following characteristics:
- The
Deviceprogram has the capability to query theLoginManagerprogram for authorization. - Calls of the
GetInfo()method of theStorageprogram are managed by methods of the Flow security model:- The finite-state machine described in the
sessionobject configuration has two states:unauthenticatedandauthenticated. - The initial state is
unauthenticated. - Only transitions from
unauthenticatedtoauthenticatedand vice versa are allowed. - The
sessionobject is created when theDeviceprogram is started. - When the
Deviceprogram successfully calls theLogin()method of theLoginManagerprogram, the state of thesessionobject changes toauthenticated. - When the
Deviceprogram successfully calls theLogout()method of theLoginManagerprogram, the state of thesessionobject changes tounauthenticated. - When the
Deviceprogram calls theGetInfo()method of theStorageprogram, the current state of thesessionobject is verified. The call is allowed only if the current state of the object isauthenticated.
- The finite-state machine described in the
Example files
The code of the example and build scripts are available at the following path:
/opt/KasperskyOS-Community-Edition-<version>/examples/device_access
Building and running example
See Building and running examples section.