Contents
- Kaspersky Managed Detection and Response Help
- What's new
- About Kaspersky Managed Detection and Response
- Hardware and software requirements
- Architecture of Kaspersky Managed Detection and Response
- Interfaces of Kaspersky Managed Detection and Response
- MDR section in Kaspersky Security Center
- Setting up MDR Plug-in in Kaspersky Security Center
- Configuring MDR Plug-in
- Setting access rights in Kaspersky Security Center
- Viewing and editing the MDR settings in Kaspersky Security Center
- Using MDR Plug-in functions on a virtual Administration Server
- Using MDR functions in Kaspersky Security Center through a proxy server
- Changing the certificates to use MDR functions in Kaspersky Security Center with a proxy server or anti-virus software
- Hiding and showing the MDR features in Kaspersky Security Center
- Setting up MDR Plug-in in Kaspersky Security Center
- MDR Web Console
- Switching the interface language in Kaspersky Security Center
- Switching the language for notifications and reports in Kaspersky Security Center
- Switching the interface language in MDR Web Console
- MDR section in Kaspersky Security Center
- Activating Kaspersky Managed Detection and Response
- Deactivating Kaspersky Managed Detection and Response
- Deployment of Kaspersky Managed Detection and Response
- About the MDR configuration file
- Licensing
- Data provision
- About Kaspersky Security Network
- Monitoring dashboards in MDR Web Console
- Receiving summary information
- Receiving notifications
- Managing users
- Managing assets
- Managing incidents
- About the incidents
- Viewing and searching incidents in MDR Web Console
- Filtering incidents in MDR Web Console
- Creating custom incidents in MDR Web Console
- Viewing detailed information about incidents in MDR Web Console
- Response types
- Processing responses to incidents in MDR Web Console
- Auto-accepting responses in MDR Web Console
- Auto-accepting responses in Kaspersky Security Center
- Closing incidents in MDR Web Console
- Using Kaspersky Endpoint Detection and Response Optimum features
- Multitenancy
- Managing the solution through the REST API
- Scenario: performing token-based authorization
- Creating an API connection in Kaspersky Security Center
- Creating an API connection in MDR Web Console
- Editing an API connection in Kaspersky Security Center
- Editing an API connection in MDR Web Console
- Creating an access token in Kaspersky Security Center
- Creating an access token in MDR Web Console
- Working with the REST API
- Revoking a refresh token in Kaspersky Security Center
- Deleting an API connection in Kaspersky Security Center
- Deleting an API connection in MDR Web Console
- Known issues
- Contact Technical Support
- Sources of information about the solution
- Glossary
- Information about third-party code
- Trademark notices
Kaspersky Managed Detection and Response Help
 New features
New features
 Hardware and software requirements
Hardware and software requirements
 Feature comparison
Feature comparison
 How to start
How to start
 Monitoring and reporting
Monitoring and reporting
- Receiving notifications
- Receiving extended notifications
- Receiving summary information
- Monitoring dashboards
 Data provision / Personal data protection
Data provision / Personal data protection
What's new
Kaspersky Managed Detection and Response presents several new features and enhancements.
02/24/2025
- MDR Web Console now features the Licenses section. The following functionality is available:
- Displaying current, unused and expired MDR licenses.
- Displaying the total number of assets and their limit for each license.
- Downloading the MDR configuration file for the root tenant.
Use the Tenants section to create and download MDR configuration files for other tenants.
- Entering a new activation code.
If your organization has multiple licenses, you can only manage them in MDR Plug-in for Kaspersky Security Center. The Licenses section in MDR Web Console becomes read-only.
- MDR Plug-in for Kaspersky Security Center now supports applying multiple licenses in your organization. The following functionality is available:
12/31/2024
- Simplified activation of Kaspersky Managed Detection and Response on Kaspersky Endpoint Security for Windows devices (starting from version 12.4). All you need is a standard license for Kaspersky MDR solution.
Note that you will still need to use the MDR configuration file (BLOB) in any of the following scenarios:
- You have more than one tenant.
- You are using the MDR solution together with Kaspersky Endpoint Detection and Response Optimum.
- Added support for managing the MDR solution in the Kaspersky Security Center Linux Web Console (starting from version 15.1).
- Added detailed information about communication channel requirements in the Help.
10/29/2024
MDR Plug-in for Kaspersky Security Center version 2.4.1 is released. It contains the following enhancements:
- The ability to configure automatic acceptance of response actions for selected tenants was added in the MDR Plug-in for Kaspersky Security Center.
- Enhanced functionality and user interface of the section that provides the list of inactive assets. Such assets have been added to Kaspersky Security Center, have the MDR component installed, but never sent telemetry to Kaspersky Managed Detection and Response. You can filter the assets by MDR status, view the detailed information about each asset, and export the asset list to a CSV file.
This feature is working properly in Kaspersky Security Center 15.1 Windows and later versions, Kaspersky Security Center 15.1 Linux and later versions, and Kaspersky Security Center Cloud Console.
- A task for regular delivery of a report on open incidents can now be created only in MDR Web Console. This feature has been removed from the MDR section in Kaspersky Security Center.
07/19/2024
MDR Web Console now allows you to configure automatic acceptance of response actions for the selected tenants.
06/24/2024
- New response actions are now available:
- Put file in quarantine
- Restore file from quarantine
- Run a script on an asset
- Updated REST API documentation, including new script examples.
- Significantly redesigned reports:
- MITRE ATT&CK mapping for in-depth threat analysis.
- List of the most frequently attacked computers to help clients focus on critical risks.
- Multi-tenant support:
- Generate reports and configure summary report schedule for specific tenants.
- Seamlessly switch widgets to tenant-specific statistics in the monitoring dashboard.
- Configure automatic confirmation of response task execution for specific tenants.
- Enhanced MDR API for tenant management.
12/18/2023
- MDR Web Console now contains the Telemetry statistics dashboard, which shows the number of telemetry events, security events, and incidents.
- Kaspersky Managed Detection and Response now supports Kaspersky Endpoint Security for Windows in Endpoint Detection and Response Agent (EDR Agent) configuration (with the limitations).
11/29/2023
- Improved display of asset statuses in MDR Web Console and in MDR Plug-in for Kaspersky Security Center: the asset status now shows the operability of the asset's EPP application components, the asset's anti-virus database update status, and telemetry transmission status.
- Asset status now shows the presence of asset's telemetry losses, allowing you to identify assets with telemetry delivery issues. This feature is enabled by default for new customers and will be gradually enabled for existing customers.
10/26/2023
The client residency region Saudi Arabia is added, for clients who store telemetry data in the Kingdom of Saudi Arabia.
9/11/2023
MDR Plug-in for Kaspersky Security Center version 2.3.1 is released. In this version, the incident management functions have been removed from the MDR section in Kaspersky Security Center. You can manage incidents in MDR Web Console.
7/20/2023
MDR Plug-in for Kaspersky Security Center version 2.3.0 is released. It contains the following enhancements:
- You can now set up extended notifications in MDR Plug-in.
- You can now use MDR functions in Kaspersky Security Center with MDR Plug-in through a proxy server.
- You can now change the certificates to use MDR functions in Kaspersky Security Center with a proxy server or anti-virus software.
7/27/2022
MDR Plug-in version 2.1.17 is released. This plug-in version is compatible with Kaspersky Security Center version 14 and later.
5/31/2022
General enhancements:
- The client residency region USA/Canada is added, for clients who store their telemetry data in Northern Europe.
- Changed the MDR deployment process description in the help.
Enhancements in MDR Plug-in:
- In the Settings section, you can now change the language for notifications in Telegram and email, and for communication in the chat about incidents.
- Improved interface for working with pictures and tables in the incident cards.
- MDR Expert. In the Service Usage section you can check how many incidents can be created according to the SLA.
Bug fixes and other improvements:
- Search in the incident and asset lists is now performed by a full occurrence of the searched substring anywhere in the string.
- In Kaspersky Endpoint Security for Mac version 11.2 and later after adding MDR activation code and KPSN configuration file, you no longer need to restart your Mac in order to start a telemetry transfer.
- When calculating licenses for virtual machines with Kaspersky Security for Virtualization 5.2 Light Agent version 5.2 and later, assets that have not transferred telemetry for more than 24 hours are not included.
5/20/2022
MDR Optimum users now can chat with Kaspersky SOC analysts about an incident (with the following limitation: requests are processed only in relation to a particular incident and no SLA is applied).
10/18/2021
- Kaspersky Managed Detection and Response Plug-in for Kaspersky Security Center Web Console and Cloud Console was updated with the enhanced MDR Health functionality:
- Improved interface of MDR Health.
- The list of assets displays all the assets of all the statuses, which were previously available only in MDR Web Console.
- Filtering and sorting options added to work with the list of assets.
7/21/2021
- Support of Kaspersky Managed Detection and Response in Kaspersky Security Center Cloud Console, which allows managing the solution in the Kaspersky Security Center single administration console. The following features are available with the Kaspersky Managed Detection and Response solution:
- Working with incidents:
- Viewing, creating, and commenting incidents
- Contacting Kaspersky Security Operation Center about an incident, accepting or rejecting responses suggested by SOC analysts
- Responding to an incident by using Kaspersky Endpoint Detection and Response
The following responses are available:
- Applying network isolation of devices
- Creating blocking rules by hash
- Creating tasks for deletion, moving to quarantine, ending the process, and searching by indicators of compromise (IoC) related to an incident
- Monitoring Kaspersky Managed Detection and Response events on dashboards in the monitoring console of Kaspersky Security Center Web Console
- Configuring notifications about Kaspersky Managed Detection and Response events by email and Telegram
- Configuring the schedule of the MDR performance summary sent by email
- Viewing the devices on which there are problems in MDR performance
- New activation wizard, which allows connecting MDR in the Kaspersky Security Center single console
- Automatic configuration of Private KSN, which no longer requires the manual downloading and uploading of a configuration file in the Kaspersky Security Center settings
- Managing connections to the public MDR API: viewing, creating, editing, and deleting tokens
- Managing the organization tenants, including their creation
- Getting information about the number of incidents available for registration on the user's side, and which are eligible for processing according to the terms of the service level agreement (SLA)
These features are also available in Kaspersky Security Center Web Console.
- Working with incidents:
- Managing several MDR Administrator accounts was added in the MDR Web Console: creating accounts and managing account privileges
- New versions of compatible applications no longer require the additional installation of Kaspersky Endpoint Agent. The built-in Kaspersky Managed Detection and Response functionality is compatible with the following EPP applications:
- Kaspersky Endpoint Security for Windows 11.6 and later
- Kaspersky Endpoint Security for Mac 11.2
- Kaspersky Endpoint Security for Linux 11.2
- Kaspersky Security for Virtualization 5.2 Light Agent
For details on different deployment scenarios, refer to Deployment of Kaspersky Managed Detection and Response.
- Filtering by event type was added for Kaspersky Endpoint Security for Windows and for Linux with the built-in Kaspersky Managed Detection and Response functionality, which allows decreasing the load on channels and reducing traffic consumption when sending data by telemetry.
- Support of the following response types: getting file from device, isolating the device, disabling the isolation of the device, deleting registry key, terminating process.
Performing these actions is possible with confirmation from the user who has the MDR Administrator role.
- Support of the following new localizations in the web plug-in for Kaspersky Security Center Web Console and Cloud Console: French, German, Italian, and Spanish.
3/31/2021
A new web plug-in for Kaspersky Security Center Web Console allows using the following Kaspersky Managed Detection and Response functionality:
- Viewing incidents
- Creating incidents
- Adding comments to the incidents
- Contacting Kaspersky Security Operation Center about an incident
- Accepting or rejecting the responses, suggested by SOC analysts
- Possibility of independent response to an incident:
- Isolate assets from the network
- Create blocking rules by hash
- Create tasks for deleting, moving to quarantine, ending the process, and searching by indicators of compromise (IoC) related to an incident
- Monitoring Kaspersky Managed Detection and Response events on dashboards in the monitoring console of Kaspersky Security Center Web Console
- Configuring email and Telegram notifications about Kaspersky Managed Detection and Response events
- Configuring the schedule of incidents summary sent by email
About Kaspersky Managed Detection and Response
Kaspersky Managed Detection and Response is a solution that automatically detects and analyzes security incidents in your infrastructure by using telemetry and advanced machine learning technologies, and then transfers information about the incident to Kaspersky experts. The experts can then either process the incident themselves or give recommendations on how to process it.
Kaspersky Managed Detection and Response (also referred to as MDR) delivers round-the-clock protection from the growing volume of threats that circumvent automated security barriers to organizations that struggle to find the expertise and staff, or for those with limited in-house resources. Unlike similar offerings on the market, this solution leverages a proven track record of effective targeted attack research to ensure continuous defense against even the most complex threats. The solution helps improve your corporate resilience to cyberthreats, while freeing up your existing resources to focus their attention on other tasks.
Kaspersky Managed Detection and Response (MDR) solution is not available in the United States or to U.S. persons. The use of MDR solution on the specified territory or by U.S. persons is a violation of terms of using the MDR solution. To avoid violation of terms of using the MDR solution, it is required to terminate the use of MDR permanently on all assets located on the specified territory or used by U.S. persons. When non-U.S. persons are temporarily in the United States, it is required to suspend the use of MDR on their assets.
Operating principle of Kaspersky Managed Detection and Response
Kaspersky Managed Detection and Response analyzes telemetry data from the EPP applications and generates security events that can be classified as incidents by the detection technology.
MDR Web Console is used to process incidents. Alternatively, you can integrate Kaspersky Managed Detection and Response with a third-party solution, as described in the Managing the solution through the REST API article.
The Kaspersky Managed Detection and Response solution may resolve an incident automatically or request a user response to a potential security threat. Refer to the Response types article for details. To ensure prompt response to potential security threats, the Kaspersky Managed Detection and Response solution may request a clarification from you for a suspicious event. You should process such requests in time.
Detailed incident investigation (such as establishing preceding events, circumstances, and detailed mechanism of the attack) is handled by the Kaspersky Incident Response component that is not included in the Kaspersky Managed Detection and Response and must be purchased separately.
Kaspersky Managed Detection and Response usage involves you processing incidents with support of Kaspersky experts. Refer to the following topic for details: Areas of responsibility.
Page top
About data sources
Kaspersky Managed Detection and Response receives data from the EPP applications that support MDR, process data, and then send it via Kaspersky Security Network streams to Kaspersky Managed Detection and Response. For the list of processed data, refer to Data provision. EPP applications are installed on the assets within the IT infrastructure of your organization (for example, mobile devices, computers, or laptops). An example of an EPP application is Kaspersky Endpoint Security for Windows.
You can also integrate Kaspersky Managed Detection and Response with other Kaspersky solutions: Kaspersky Managed Detection and Response allows you to analyze and monitor the data from Kaspersky Anti-Targeted Attack (KATA) Platform. To configure integration between Kaspersky Managed Detection and Response and Kaspersky Anti-Targeted Attack Platform, you need to receive an MDR configuration file, first. For details on how to configure the integration, refer to Kaspersky Anti-Targeted Attack Platform online help.
Kaspersky Anti-Targeted Attack Platform is not part of Kaspersky Managed Detection and Response. If you want to use Kaspersky Anti-Targeted Attack Platform, you must purchase it separately. Integration with Kaspersky Anti-Targeted Attack Platform is not available when using an activation code for the Saudi Arabia region.
If you encounter any issues when installing EPP applications or configuring MDR integration with other Kaspersky solutions, contact technical support.
Page top
Areas of responsibility
Kaspersky Managed Detection and Response usage involves users processing incidents with support of Kaspersky experts. Additionally, Kaspersky Technical Support handles solution-related issues.
The table below shows areas of responsibility for users, Kaspersky experts and Kaspersky Technical Support.
Task |
Kaspersky experts |
Kaspersky Technical Support |
MDR users |
Activating MDR, deploying MDR, managing assets, setting up notifications, managing users, terminating the use of MDR. |
- |
Consult |
Perform the task |
- |
Consult |
Perform the task |
|
Detecting, investigating, issuing response recommendations for incidents based on telemetry data |
Perform the task |
- |
Receive information |
Clarifying details during investigation, answering questions from Kaspersky experts for better response recommendations |
Receive information |
- |
Perform the task |
Creating requests to use tools and capabilities of MDR to handle incidents |
Perform the task |
- |
Receive information |
Coordinating requests to use tools and capabilities of MDR to handle incidents |
Receive information |
- |
Perform the task |
Performing tasks outside functional capabilities of MDR |
Consult |
- |
Perform the task |
Manually creating an incident (it is important to choose an MDR asset and describe the incident in detail) |
Receive information |
- |
Perform the task |
Handling issues with Kaspersky infrastructure components that affect MDR |
Receive information |
Consult |
Perform the task |
Managing detection rules |
Perform the task |
- |
- |
Hardware and software requirements
Required EPP applications and supported configurations
In order to use Kaspersky Managed Detection and Response, at least one of the following EPP applications must be deployed in your infrastructure:
- Kaspersky Endpoint Security for Windows
- Kaspersky Endpoint Security for Linux
- Kaspersky Endpoint Security for Mac
- Kaspersky Security for Windows Server with Kaspersky Endpoint Agent for Windows
To use the MDR functionality on your servers running OS Windows, we recommend using Kaspersky Endpoint Security for Windows on these servers, instead of Kaspersky Security for Windows Server with Kaspersky Endpoint Agent.
- Kaspersky Security for Virtualization 5.2 Light Agent
Operating systems
Kaspersky Managed Detection and Response is compatible with the same operating systems as the EPP applications listed below. For details, please refer to the Hardware and software requirements section in the documentation of compatible EPP applications listed in the table below.
Compatible Kaspersky applications and solutions
Kaspersky Managed Detection and Response is compatible with the versions of Kaspersky applications and solutions listed in the table below.
Kaspersky application |
Recommended versions |
Compatible versions |
Notes |
|---|---|---|---|
Kaspersky Endpoint Security for Windows |
|
||
|
|||
Kaspersky Endpoint Security for Linux |
If you use Kaspersky Endpoint Security for Linux and do not have the Linux Audit Daemon (also referred to as auditd) package installed, system audit events are logged to the |
||
Kaspersky Endpoint Security for Mac |
|
||
Kaspersky Security for Virtualization Light Agent |
Kaspersky Security for Virtualization version 5.2 Light Agent is not supported if you use Kaspersky Security Center Linux. |
||
Kaspersky Endpoint Agent |
Kaspersky Endpoint Agent is only required if you use Kaspersky Security for Windows Server.
Please note that the Kaspersky Managed Detection and Response solution is compatible with the Kaspersky Endpoint Agent versions 3.9, 3.10 and 3.11, but the technical support period for these versions is over. If you use Kaspersky Endpoint Agent versions 3.9, 3.10, and 3.11 as an agent for the Kaspersky Managed Detection and Response solution, Kaspersky recommends updating Kaspersky Endpoint Agent to version 3.15. Working with Kaspersky Security Center Cloud Console is only available for Kaspersky Endpoint Agent for Windows 3.12 or later. |
||
Kaspersky Security for Windows Server |
We recommend to use Kaspersky Endpoint Security for Windows 12 or later |
To use the MDR functionality on your servers running Windows, we recommend using Kaspersky Endpoint Security for Windows on these servers, instead of Kaspersky Security for Windows Server with Kaspersky Endpoint Agent:
|
|
Kaspersky Security Center Windows |
|||
Kaspersky Security Center Linux |
|||
Kaspersky Security Center Cloud Console |
n/a |
n/a |
The latest version is always used in the cloud. |
MDR Plug-in for Kaspersky Security Center |
Latest version |
Latest version |
MDR Plug-in 2.1.15 and later is available only in Kaspersky Security Center 15.1 Windows or later and Kaspersky Security Center 15.1 Linux or later.
|
Kaspersky Security Center Network Agent |
The version provided with Kaspersky Security Center Windows installed |
When you update Kaspersky Security Center, you must also update Kaspersky Security Center Network Agent to the corresponding version. |
|
Kaspersky Anti Targeted Attack Platform + Kaspersky Endpoint Detection and Response |
Please note that the cloud solution Kaspersky Endpoint Detection and Response Expert is not supported. |
||
Kaspersky Endpoint Detection and Response Optimum |
If you use Kaspersky Endpoint Security for Windows 11.7 or later, EDR Optimum must be used without Kaspersky Endpoint Agent.
To activate Kaspersky Endpoint Detection and Response Optimum functions, you must add one of the following activation codes on your assets via Kaspersky Security Center:
|
To learn more about the supported versions of Kaspersky applications and solutions, refer to the Product Support Lifecycle webpage.
MDR Web Console
MDR Web Console has the following hardware and software requirements:
- Monitor that supports a display resolution of 1024x768 or higher
- Any of the following browsers:
- Apple Safari—15 on macOS
- Google Chrome—100.0.4896.88 or later (official build)
- Microsoft Edge—100 or later
- Mozilla Firefox—91.8.0 or later
Network channel
The following table shows network channel throughput calculated from our statistical data.
Operating system |
Estimated bandwidth for 1000 assets |
Windows |
4.3 Mbit/s |
Windows server |
5.2 Mbit/s |
Linux (average for hosts and servers) |
14.7 Mbit/s |
macOS |
8.5 Mbit/s |
These bandwidth values are approximate, as the necessary bandwidth greatly depends on the type of asset load generating telemetry events. Peak throughput can be significantly higher. You will need to provide an accordingly higher network bandwidth if your infrastructure regularly operates at peak throughput. Various conditions may presume the load to be higher. For example:
- program code compilation by developers
- full system scan
- high-load servers (for example, DNS and domain controllers)
- multiple network connections
Architecture of Kaspersky Managed Detection and Response
The figure below shows the components of Kaspersky Managed Detection and Response, and their interaction.

Architecture of Kaspersky Managed Detection and Response
Description of Kaspersky Managed Detection and Response components:
- is an organization's device that is protected by Kaspersky solutions.
- Endpoint Protection Platform (EPP) application is a Kaspersky application that protects assets, and the data stored on them, from malware and other threats.
- The Kaspersky Endpoint Agent is a program component that is installed on workstations and servers of the corporate IT infrastructure. Kaspersky Endpoint Agent continuously monitors processes running on those computers, active network connections, and the files that are modified. In recent versions of EPP applications it was replaced by the built-in functionality.
- Kaspersky Network Agent is a Kaspersky Security Center component that enables interaction between the Administration Server and the Kaspersky applications that are installed on a specific network node (workstation or server). This component is common to all of the company's applications for Microsoft Windows. Separate versions of Network Agent exist for Kaspersky applications developed for Unix-like operation systems and for macOS.
- Kaspersky Security Center is an application aimed at corporate network administrators and employees responsible for the protection of assets in a wide range of organizations.
- Kaspersky Security Network is an infrastructure of cloud services that provides access to the Kaspersky online knowledge base, which contains information about the reputation of files, web resources, and software. The use of data from Kaspersky Security Network ensures faster responses by Kaspersky applications to threats, improves the performance of some protection components, and reduces the likelihood of false alarms.
- Kaspersky Managed Detection and Response (also referred to as MDR) is a solution that delivers continuous managed protection, enabling organizations to hunt down evasive threats automatically, while freeing up IT security teams to focus on critical tasks that require their involvement.
- MDR Web Console provides a web interface for managing and maintaining the protection system of a client organization's network that is managed by Kaspersky Managed Detection and Response. In addition to MDR Web Console, the Kaspersky Security Center web plug-in was added to allow the management of Kaspersky Managed Detection and Response within a single administration console.
- The MDR API is the Application Programming Interface for managing and supporting the network protection system of a client organization managed by Kaspersky Managed Detection and Response.
Interfaces of Kaspersky Managed Detection and Response
This section provides information about the Kaspersky Managed Detection and Response user interfaces.
You can work with Kaspersky Managed Detection and Response by using the following interfaces:
- Kaspersky Managed Detection and Response portal (hereinafter also referred to as MDR Web Console).
MDR Web Console is available at https://mdr.kaspersky.com/ after logging in. To log in, use the email address and password of the Kaspersky website account created during the activation of Kaspersky Managed Detection and Response.
- The MDR section in Kaspersky Security Center Web Console or in Kaspersky Security Center Cloud Console.
In order to use Kaspersky Security Center Web Console with Kaspersky Managed Detection and Response, you must download and configure MDR Plug-in in Kaspersky Security Center Web Console. In Kaspersky Security Center Cloud Console, MDR Plug-in is pre-installed.
To access Kaspersky Managed Detection and Response functions, in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, click Monitoring & reporting → MDR.
The capabilities and available functions in these interfaces are basically the same, but we recommend performing some tasks in one of the interfaces, since there is a wider set of functions or data available. The recommended interface is specified in the description of the tasks and usage scenarios.
The Kaspersky Security Center interface is intended mainly to accomplish the following tasks:
- Activating the Kaspersky Managed Detection and Response solution
- Checking the status of assets
The MDR Web Console interface is intended mainly to accomplish the following tasks:
- Security officer tasks: managing incidents
- Administrator tasks: managing MDR users
- Viewing and managing assets
MDR section in Kaspersky Security Center
You can work with Kaspersky Managed Detection and Response by using the MDR section in Kaspersky Security Center Web Console or in Kaspersky Security Center Cloud Console. To access Kaspersky Managed Detection and Response functions, in Kaspersky Security Center, click Monitoring & reporting → MDR.
The MDR section in the Kaspersky Security Center web interface contains the following tabs:
- Incidents. Contains the link to MDR Web Console, where you can manage your incidents.
- Reports. Contains the report delivery tasks list and the functions to edit, delete or create a task.
- Settings. Allows enabling extended notifications and switching the language for incident data, notifications, and reports.
- Notifications. Allows enabling notifications via email and Telegram.
- API. Contains the list of API connections and the functions to manage them.
- Tenants. Contains the list of tenants and the functions to manage them.
- MDR Health. Contains the lists of malfunctioning assets and all assets ever seen.
- Getting Started. Contains instructions for setting up the MDR solution.
- MDR Usage. Contains information about the solution activation status, license, telemetry storage region, KSN configuration file, and Terms of Use acceptance status.
You can also add the MDR assets by status widget on the Monitoring & reporting → Dashboard pane in Kaspersky Security Center.
Page top
Setting up MDR Plug-in in Kaspersky Security Center
This section contains information about the initial configuration of MDR Plug-in in Kaspersky Security Center, for work with Kaspersky Managed Detection and Response.
Configuring MDR Plug-in
To use Kaspersky Managed Detection and Response via MDR Plug-in, you need to configure MDR Plug-in in one of the following applications:
- Kaspersky Security Center Web Console of Kaspersky Security Center Windows
- Kaspersky Security Center Web Console of Kaspersky Security Center Linux
- Kaspersky Security Center Cloud Console
Prerequisites
Make sure you have access to Kaspersky Security Center Web Console or to Kaspersky Security Center Cloud Console, with the following minimum access rights:
- Read access right for the General features: Application integration functional area of Kaspersky Security Center
- Allow access right for the Incident access functional area of Kaspersky Managed Detection and Response
Stages
The configuration proceeds in stages:
- Downloading MDR Plug-in
Skip this stage if you are using Kaspersky Security Center Cloud Console, because MDR Plug-in is pre-installed in Kaspersky Security Center Cloud Console.
In Kaspersky Security Center Web Console, download MDR Plug-in by selecting Kaspersky Managed Detection and Response in the list of available plug-ins. For details on how to get web plug-ins, refer to Kaspersky Security Center Windows Help or Kaspersky Security Center Linux Help.
- Setting access rights
Set access rights manually for every user that you want to use MDR Plug-in, or create MDR roles with predefined access rights automatically by clicking the link in the first step on the Getting Started tab of MDR Plug-in.
Results
Upon completion of this scenario, MDR Plug-in is set up to work with Kaspersky Managed Detection and Response.
Page top
Setting access rights in Kaspersky Security Center
You must set access rights for every user of Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console who will use MDR functions in Kaspersky Security Center. Access rights depend on the actions that you want users to be able to perform.
You can create MDR roles with predefined access rights automatically by clicking the link in the first step on the Getting Started tab of MDR section in Kaspersky Security Center.
To set access rights:
- In Kaspersky Security Center, go to the Users & roles → Roles section, and then create a new role. For details on how to create roles, refer to Kaspersky Security Center Windows Help, Kaspersky Security Center Linux Help, or Kaspersky Security Center Cloud Console Help.
- On the Access rights tab of a new role, set the Allow right for the following functional areas:
- Application Integration
Permits users to configure interaction between Kaspersky Security Center and another Kaspersky application or solution.
It is required to set the Allow access right for the Application Integration functional area for users who manage MDR Plug-in. This access right grants users rights to activate, configure, use, and terminate the use of Kaspersky Managed Detection and Response.
- Incident access
It is required to set the Allow access right for the Incident access functional area for users to have access to the MDR section in Kaspersky Security Center. If the Incident access functional area has the Deny access right set, users can see only the Getting started tab of the MDR section in Kaspersky Security Center.
- Tenant management
Permits users to create, view, and edit tenants.
- REST API access
Permits users to manage Kaspersky Managed Detection and Response through the REST API.
The following table shows the minimum set of access rights.
Minimum set of access rights
Functional area
Allow
Deny
Application Integration


Incident access


Auto-accept settings


Response management


Tenant management


Incident summary scheduling


REST API access


- Application Integration
- Assign the created role to all users who will use MDR functions in Kaspersky Security Center.
The access rights are set.
Page top
Viewing and editing the MDR settings in Kaspersky Security Center
You can view and edit settings of MDR Plug-in installed in Kaspersky Security Center.
To view and edit settings:
- In the MDR section of Kaspersky Security Center, click the Settings tab.
- If you want to enable extended notifications via email, turn on the Enable extended notifications via email option, and then select the check box to confirm that you have read and understand the terms of sending extended notifications.
- You can use the Language setting to select English or Russian for displaying reports and notifications.
- Click the Save button in the lower part of the window to save the settings.
The Save button becomes active only if you changed the settings.
Using MDR Plug-in functions on a virtual Administration Server
To use MDR functions in Kaspersky Security Center on a virtual Administration Server:
- If you use Kaspersky Security Center Windows:
- Download the MDR configuration file in Kaspersky Security Center Web Console or in MDR Web Console.
- In Kaspersky Security Center Web Console, select the main (physical) Administration Server where your virtual Administration Server is located.
- Enable the Kaspersky Private Security Network switch in the main (physical) Administration Server properties.
- Click the Select file with KSN Proxy settings button, and select the MDR configuration file you have downloaded.
- If you use Kaspersky Security Center Cloud Console:
- Activate Kaspersky Managed Detection and Response on the main (physical) Administration Server.
- On the main (physical) Administration Server, click Monitoring & reporting → MDR, open the MDR Usage tab, and make sure that the KPSN section contains the correct status and version of the KPSN configuration file. Example of correct status and version:
To send telemetry data to the Kaspersky MDR infrastructure, the KPSN configuration file with version {{version}} is usedIf the file status or version is incorrect, please contact Technical Support.
Using MDR functions in Kaspersky Security Center through a proxy server
If a proxy server is used on the network where Kaspersky Security Center is running, you must set two environment variables with proxy server settings for the HTTP and the HTTPS protocols, for the MDR functions in Kaspersky Security Center to work properly. These environment variables must be set on the host where Kaspersky Security Center Web Console is installed.
The environment variables have the following format:
HTTP_PROXY=<protocol>://<proxy_user_name>:<proxy_user_password>@<host>:<port>
where:
<protocol>is http or https.<proxy_user_name>is the user name for authorization on the proxy server.<proxy_user_password>is the password for authorization on the proxy server.<host>:<port>are the name or IP address of the proxy server, and its port number.Example of environment variables:
HTTP_PROXY=http://proxy_user_name:proxy_user_password@proxy.domain.com:8080HTTPS_PROXY=https://proxy_user_name:proxy_user_password@proxy.domain.com:443
You can set the environment variables in two ways:
- If you want to apply the proxy settings to all applications on the host where Kaspersky Security Center Web Console is installed, add these environment variables by using the Edit the system environment variables component of the Windows operating system. For information on using this component, refer to the documentation for the version of the operating system that you are using.
- If you want to apply these proxy settings only to Kaspersky Security Center Web Console, add these environment variables in the .env file located in the Kaspersky Security Center Web Console installation folder (by default, C:\Program Files\Kaspersky Lab\Kaspersky Security Center Web Console\). If the .env file is missing in the installation folder, create it.
After setting the environment variables, you need to restart the host where Kaspersky Security Center Web Console is installed for the changes to be applied.
Page top
Changing the certificates to use MDR functions in Kaspersky Security Center with a proxy server or anti-virus software
You need to redefine the certificate chain for connection between Kaspersky Security Center Web Console with MDR Plug-in and the MDR solution infrastructure in the following cases:
- A proxy server with a TLS connection is used on the network where Kaspersky Security Center is running.
- Anti-virus software with TLS traffic encryption is running on a host where Kaspersky Security Center Web Console is installed.
To redefine the certificate chain:
- Save the necessary certificates as files on your computer.
- To save the certificate file of the software encrypting traffic, on the host with Kaspersky Security Center Web Console open https://mdr-ksc.kaspersky.com/ in the Chrome browser, click the lock icon in the address bar next to the site address, click Connection is secure, click Certificate is valid, go to the Details tab, and then click the Export button. For instructions for other browsers, refer to the documentation for these browsers.
- To get the certificate used to connect to the proxy server, contact your network administrator.
- Add the saved certificates to the file with the .PEM extension (for example, KL_Root.pem).
- Place the created .PEM file in the Kaspersky Security Center Web Console installation folder (by default, C:\Program Files\Kaspersky Lab\Kaspersky Security Center Web Console\).
- Add the NODE_EXTRA_CA_CERTS environment variable to the .env file located in the Kaspersky Security Center Web Console installation folder. If the .env file is missing in the installation folder, create it.
Example of the variable:
NODE_EXTRA_CA_CERTS="C:\Program Files\Kaspersky Lab\Kaspersky Security Center Web Console\KL_Root.pem"
To apply the changes after you set the environment variable, restart the host where Kaspersky Security Center Web Console is installed.
Page top
Hiding and showing the MDR features in Kaspersky Security Center
By default, the interface elements related to Kaspersky Managed Detection and Response are displayed in the interface of Kaspersky Security Center. If you do not use Kaspersky Managed Detection and Response, you can hide its features from the interface. Later, you can change the interface settings to show the hidden elements again.
To hide the MDR features in Kaspersky Security Center Cloud Console:
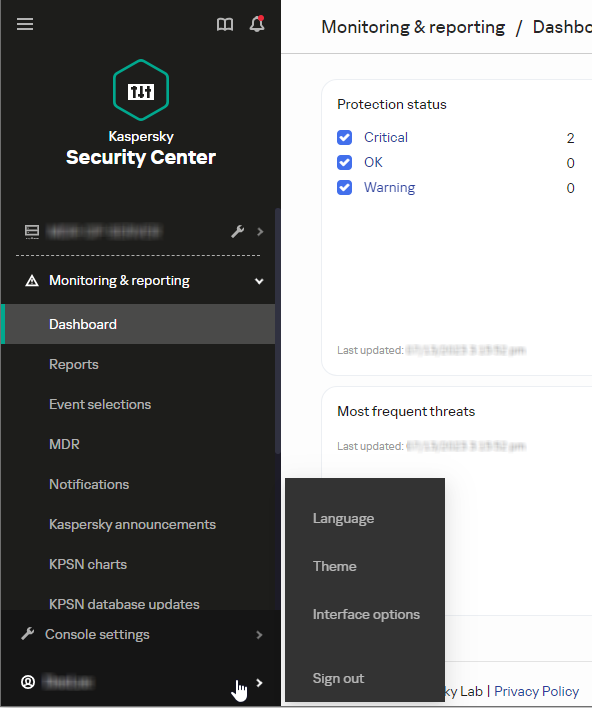
- In Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, hover the mouse pointer over your username, which is located on the left panel at the bottom. The interface settings menu appears.
- Click Interface options.
- Turn off or turn on the Show MDR features.
- Click the Save button.
Kaspersky Security Center saves the value of this option only for your user account. Other users can set a different value.
The MDR section is hidden or shown.
MDR Web Console
You can work with Kaspersky Managed Detection and Response in the web interface named MDR Web Console.
The MDR Web Console window contains the following items:
- Main menu in the left pane of the window
- Work area in the right pane of the window
Main menu
The main menu contains the following sections:
- Monitoring. Contains the widgets that provide summary information about active incidents, assets, and responses.
- Incidents. Contains detailed information about your incidents, and the tools to work with them.
- Assets. Contains detailed information about assets, and the tools to work with them.
- Settings. Contains the tabs to work with the user accounts, notifications, incident settings, summary reports, API, tenants, and general settings.
- About. Contains the information about the solution, links to the MDR Agreement, Data Processing Agreement, this online help, and the Technical Support website.
In the lower part of the left pane there is an Account settings control that allows you to access the Getting started guide, change the interface language, access your user profile page, and sign out of MDR Web Console.
Work area
The work area displays the information you choose to view in the MDR Web Console. The work area also contains control elements that you can use to configure how the information is displayed.
Page top
Switching the interface language in Kaspersky Security Center
The MDR interface in Kaspersky Security Center is available in the following languages:
- English
- Russian
- German
- Spanish
- French
- Italian
To switch the interface language in Kaspersky Security Center:
- In Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, hover the mouse pointer over your username, which is located on the left panel at the bottom.
The interface settings menu appears.
Switching the interface language in Kaspersky Security Center
- Click Language.
The User settings block appears.
- On the Language tab, select the language that you want to apply to MDR interface in Kaspersky Security Center.
The language is switched.
You can switch to another language at any time in the future.
Page top
Switching the language for notifications and reports in Kaspersky Security Center
In Kaspersky Security Center you can select English or Russian for displaying incident data, notifications, and reports.
To switch the language for notifications and reports in Kaspersky Security Center:
- In Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, click MDR → Settings.
- In the Language area, select Russian or English.
- Click the Save button.
The language is switched.
You can switch to another language at any time in the future.
Switching the interface language in MDR Web Console
The MDR Web Console interface is available in the following languages:
- English
- Russian
To change the MDR Web Console interface language:
- In MDR Web Console, navigate to the Account settings section located on the left panel at the bottom. This section contains the Language area.
- In the Language area, click the language that you want to apply to the MDR Console interface.
The language is changed. You can change it to another language at any time in the future.
Activating Kaspersky Managed Detection and Response
We recommend activating Kaspersky Managed Detection and Response in Kaspersky Security Center with MDR Plug-in installed, as described in this section.
Activating Kaspersky Managed Detection and Response in Kaspersky Security Center
Activation of Kaspersky Managed Detection and Response is not available in a Kaspersky Security Center Cloud Console trial workspace.
To activate Kaspersky Managed Detection and Response:
- Make sure that MDR Plug-in is installed and configured in Kaspersky Security Center.
- In Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, click Monitoring & reporting → MDR.
- Click the Activate the solution button.
- Kaspersky Managed Detection and Response checks whether the background connection between Kaspersky Security Center Web Console and the Administration Server is enabled and prompts to enable it, if necessary.
- If you have not previously created Kaspersky Account, create it and make sure to confirm it by using the confirmation link sent to your email.
If your previously created Kaspersky Account (i.e. your email) has previously been used to access Kaspersky Managed Detection and Response, it may be associated with another organization's MDR data and can be unavailable to apply a new activation code. To use your existing Kaspersky Account for the new activation, contact Technical Support.
Please note: when Technical Support staff remove the association of your existing Kaspersky Account with another organization's data in MDR, your existing Kaspersky Account can no longer be used to access the other organization's data for which it was previously used. - When your Kaspersky Account is activated, in the MDR section of Kaspersky Security Center, sign in with your Kaspersky Account.
- Kaspersky Managed Detection and Response checks whether the account has a current license for Kaspersky Managed Detection and Response:
- If no current license is found, enter the activation code received from Kaspersky, select your region, and then click the Activate button.
The region that you select affects the choice of language that will be used to provide you the service (Russian or English), and your telemetry data storage location. If you select the Europe or Canada region, your telemetry data is stored in Northern Europe. If you select Saudi Arabia, your telemetry data is stored in the Kingdom of Saudi Arabia. If you select Russia or other regions, your telemetry data is stored in Russia.
- If a current license is found and you already have tenants, then select the tenants to which the users of this Administration Server will have access.
An enabled background connection is required for Kaspersky Managed Detection and Response performance.
- If no current license is found, enter the activation code received from Kaspersky, select your region, and then click the Activate button.
- Read and accept the agreements applicable to the region you select by clicking the Accept button.
If you do not agree to the terms of the applicable agreements, you will not be able to use Kaspersky Managed Detection and Response.
- Read and accept the KSN Statement, enable KSN usage, and then apply the KSN configuration file for your organization.
If you do not agree to the terms of the KSN Statement, you will not be able to use Kaspersky Managed Detection and Response.
The activation is complete.
To stop using Kaspersky Managed Detection and Response, refer to the Terminating the use of Kaspersky Managed Detection and Response section or contact Technical Support.
Page top
Activating Kaspersky Managed Detection and Response in MDR Web Console
To activate Kaspersky Managed Detection and Response:
- If you have not previously created Kaspersky Account, create it and make sure to confirm it by using the confirmation link sent to your email.
If your previously created Kaspersky Account (i.e. your email) has previously been used to access Kaspersky Managed Detection and Response, it may be associated with another organization's MDR data and can be unavailable to apply a new activation code. To use your existing Kaspersky Account for the new activation, contact Technical Support.
Please note: when Technical Support staff remove the association of your existing Kaspersky Account with another organization's data in MDR, your existing Kaspersky Account can no longer be used to access the other organization's data for which it was previously used. - When your Kaspersky Account is activated, in MDR Web Console sign in with your Kaspersky Account.
- To use MDR Web Console, enter the activation code received from Kaspersky, in the corresponding field on the page.
- Read and accept the agreements applicable to your region by clicking the Confirm button.
If you do not agree to the applicable agreements, you will not be able to use Kaspersky Managed Detection and Response.
The activation is complete.
To stop using Kaspersky Managed Detection and Response, refer to this article or contact Technical Support.
Page top
Deactivating Kaspersky Managed Detection and Response
If you want to stop using Kaspersky Managed Detection and Response, you can either permanently terminate its usage or temporarily suspend it on particular assets.
Terminating the use of Kaspersky Managed Detection and Response
You can manually terminate the use of Kaspersky Managed Detection and Response if you want to stop using it.
When you terminate the use of Kaspersky Managed Detection and Response, Kaspersky Managed Detection and Response stops sending telemetry from your assets. To delete the data about your organization from the infrastructure of Kaspersky Managed Detection and Response, please contact technical support.
To terminate the use of Kaspersky Managed Detection and Response:
- In Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, go to the Devices → Policies and profiles section, if you are using the EPP applications that support policies.
If you are using an EPP application that does not support policies, go to the Devices → Tasks section.
The list of policies (or the list of tasks) opens.
- Click a policy or task that you created during the deployment of Kaspersky Managed Detection and Response to set up integration between an EPP application and Kaspersky Managed Detection and Response.
The policy settings window (or the task settings window) opens.
- On the Application settings tab, in the left pane, select Detection and Response, and then in the right pane, select Managed Detection and Response.
The Managed Detection and Response settings pane opens.
- Disable the Managed Detection and Response enabled option.
The name of the option changes to Managed Detection and Response disabled.
- Save the changes to the policy or task.
- Revoke your consent with the terms of using the MDR solution.
- If you are using the on-premises Kaspersky Security Center Web Console to work with Kaspersky MDR, it is additionally recommended to remove the Kaspersky Security Network configuration file from Kaspersky Security Center Administration Server.
The use of Kaspersky Managed Detection and Response is terminated.
Page top
Suspending the use of Kaspersky Managed Detection and Response temporarily
In order to comply with the terms of using the MDR solution it is required to suspend the use of the solution on the assets if they are temporarily located on the United States territory (for example, during a business trip).
To suspend the use of the MDR solution temporarily on particular assets:
- In Kaspersky Security Center, create a new administration group to manage assets on which you want to suspend the use of the MDR solution. You will be able to modify the list of assets in this group later.
- For this administration group, create new policies of the EPP applications used to provide the MDR telemetry from the assets, and then disable the use of the MDR solution and Kaspersky Security Network in the policy settings.
For details about configuring the policies, refer to the help articles for a particular EPP application. For example, Kaspersky Endpoint Security for Windows help contains instructions on managing policies and configuring integration with the MDR solution.
- Move the assets on which you want to suspend the use of the MDR solution to the created administration group.
The new policy where the use of MDR solution and Kaspersky Security Network are disabled will be applied to the assets after synchronization. You can also manually force the synchronization.
To resume the use of Kaspersky Managed Detection and Response after suspension:
- Exclude the asset from the administration group used for suspension.
- Apply a regular policy where the use of MDR solution is enabled and configured to this asset.
The assets will not be monitored by the MDR solution until a policy where the use of MDR solution is enabled and configured is applied to them.
Deployment of Kaspersky Managed Detection and Response
This section contains information about the deployment of Kaspersky Managed Detection and Response. Deployment scenarios differ depending on which Kaspersky applications are used in your infrastructure.
First, you need to perform the prerequisites, which differ depending on the application you are using for centralized management of your network security:
- On-premises applications are Kaspersky Security Center (Microsoft Management Console-based Administration Console) and Kaspersky Security Center Web Console.
- Cloud-based solution is the Kaspersky Security Center Cloud Console.
Further steps for deploying Kaspersky Managed Detection and Response depend on the specific
that are installed on your assets.Until the Kaspersky Security Network Statement is accepted, KSN is disabled. In addition, asset statuses can be Critical in Kaspersky Security Center, and you will receive the event KSN servers are unavailable. The use of KSN is enabled after applying the policy in which the administrator accepts the KSN terms of use.
On-premises deployment
This section contains Kaspersky Managed Detection and Response deployment scenarios that use the on-premises applications Kaspersky Security Center (Microsoft Management Console-based Administration Console) and Kaspersky Security Center Web Console.
Deployment using Kaspersky Security Center
Prerequisites
- Your IT infrastructure must meet the hardware and software requirements of Kaspersky Managed Detection and Response.
- For ports 443 and 1443 on each asset that you want to protect, outgoing non-SSL traffic is allowed and traffic inspection is disabled. These ports are used for transferring telemetry data from the assets to the following Kaspersky servers:
- *.ksn.kaspersky-labs.com
- ksn-*.kaspersky-labs.com
- ds.kaspersky.com
Deployment of Kaspersky Managed Detection and Response by using Kaspersky Security Center proceeds in stages:
- Activation of the solution
Activate the Kaspersky Managed Detection and Response solution with your license.
- Installing EPP applications
Ensure that you have installed the EPP applications that support Kaspersky Managed Detection and Response functionality on your assets.
- Downloading the MDR configuration file
Download the MDR configuration file for your organization or download separate archives for every tenant from the Tenants section of MDR Web Console.
Starting from Kaspersky Endpoint Security for Windows 12.6, if you have only root tenant and if you are not using the MDR solution together with Kaspersky Endpoint Detection and Response Optimum you do not need to download MDR configuration file. Please refer to the instruction provided for Kaspersky Endpoint Security for Windows at stage 5.
- Kaspersky Private Security Network (KPSN) configuration
Set up KPSN on your assets by using your KSN configuration file from the MDR configuration file.
This step ensures that telemetry is sent to dedicated servers that comply are compliant with GDPR. If you do not set up Private KSN, your telemetry is not transmitted, and the Kaspersky Managed Detection and Response service is not provided.
- Integration with EPP applications
Perform the application-specific deployment scenarios for all the Kaspersky applications installed on your assets:
- Kaspersky Endpoint Security for Windows
- Kaspersky Endpoint Security for Linux
- Kaspersky Endpoint Security for Mac
- Kaspersky Security for Windows Server
- Kaspersky Security for Virtualization 5.2 Light Agent
- Kaspersky Anti-Targeted Attack Platform
If you have more than one Kaspersky application installed in your infrastructure, you can perform the application-specific scenarios in any order.
You can check the status of your assets by using the MDR Health functionality.
Deployment by using Kaspersky Security Center Web Console
Prerequisites
- Your IT infrastructure meets the hardware and software requirements of Kaspersky Managed Detection and Response.
- For ports 443 and 1443 on each asset that you want to protect, outgoing non-SSL traffic is allowed and traffic inspection is disabled. These ports are used for transferring telemetry data from the assets to the following Kaspersky servers:
- *.ksn.kaspersky-labs.com
- ksn-*.kaspersky-labs.com
- ds.kaspersky.com
Deployment of Kaspersky Managed Detection and Response by using Kaspersky Security Center Web Console proceeds in stages:
- Installing MDR Plug-in
Download and configure MDR Plug-in for managing the solution in Kaspersky Security Center Web Console.
- Activation of the solution
Activate the Kaspersky Managed Detection and Response solution with your license.
- Downloading the MDR configuration file
Download the MDR configuration file for your organization or download separate archives for every tenant from the Tenants section of MDR Web Console or by using MDR Plug-in in Kaspersky Security Center Web Console.
Starting from Kaspersky Endpoint Security for Windows 12.6, if you have only root tenant and if you are not using the MDR solution together with Kaspersky Endpoint Detection and Response Optimum you do not need to download MDR configuration file. Please refer to the instruction provided for Kaspersky Endpoint Security for Windows at stage 5.
- Installing EPP applications
Ensure that you have installed the EPP applications that support Kaspersky Managed Detection and Response functionality on your assets.
- Integration with EPP applications
Perform the application-specific deployment scenarios for all the Kaspersky applications installed on your assets:
- Kaspersky Endpoint Security for Windows
- Kaspersky Endpoint Security for Linux
- Kaspersky Endpoint Security for Mac
- Kaspersky Security for Windows Server
- Kaspersky Security for Virtualization 5.2 Light Agent
- Kaspersky Anti-Targeted Attack Platform
If you have more than one Kaspersky application installed in your infrastructure, you can perform the application-specific scenarios in any order.
In case you do not use MDR Plug-in, manually set up Private KSN on your assets by using your KSN configuration file from the MDR configuration file. This step ensures that telemetry is sent to the dedicated servers that comply with GDPR regulations. If you do not set up Private KSN and do not use MDR Plug-in for initial deployment of Kaspersky Managed Detection and Response, your telemetry is not transmitted, and the Kaspersky Managed Detection and Response service is not provided.
You can check the status of your assets by using the MDR Health functionality.
Page top
Cloud-based deployment
Deployment of Kaspersky Managed Detection and Response by using Kaspersky Security Center Cloud Console proceeds in stages:
- Activation of the solution
Activate the Kaspersky Managed Detection and Response solution with your license.
- Installing EPP applications
Ensure that you have installed the EPP applications that support Kaspersky Managed Detection and Response functionality on your assets.
- Downloading the MDR configuration file
Download the MDR configuration file for your organization or download separate archives for every tenant from the Tenants section of MDR Web Console or by using MDR Plug-in in Kaspersky Security Center Cloud Console.
Starting from Kaspersky Endpoint Security for Windows 12.6, if you have only root tenant and if you are not using the MDR solution together with Kaspersky Endpoint Detection and Response Optimum you do not need to download MDR configuration file. Please refer to the instruction provided for Kaspersky Endpoint Security for Windows at stage 4.
- Integration with EPP applications
Perform the application-specific deployment scenarios for all the Kaspersky applications installed on your assets:
- Kaspersky Endpoint Security for Windows
- Kaspersky Endpoint Security for Linux
- Kaspersky Endpoint Security for Mac
- Kaspersky Security for Windows Server
- Kaspersky Anti-Targeted Attack Platform
If you have more than one Kaspersky application installed in your infrastructure, you can perform the application-specific scenarios in any order.
- Creation of the distribution point
Perform the following actions:
- Verify that you have at least one distribution point in your network or configure a device in your organization's network as a distribution point. The distribution point will act as a proxy server for the devices participating in the Kaspersky Security Network.
- Enable KSN Proxy on distribution point side in the KSN Proxy (distribution points) section of the distribution point settings.
- Configure the Scope of the distribution point by selecting the administration group and/or network location.
You can check the status of your assets by using the MDR Health functionality.
Page top
About the MDR configuration file
Kaspersky Managed Detection and Response uses an MDR configuration file to enable the solution on Kaspersky EPP applications for workstations (such as Kaspersky Endpoint Security for Windows) installed on assets, and to configure integration with Kaspersky Anti-Targeted Attack Platform.
You may not need MDR configuration file on the following conditions:
Note that even if you do not use the MDR configuration file, it is required to activate the solution using the MDR Web Console or MDR Plug-in in Kaspersky Security Center.
- You are using Kaspersky Endpoint Security for Windows 12.6 or later as EPP application.
- You have only root tenant.
- You are not using Kaspersky Endpoint Detection and Response Optimum solution simultaneously with Kaspersky MDR solution.
In this case Kaspersky Endpoint Security for Windows applies the license from Kaspersky Security Center. If you use tenants other than the root tenant, you need to download MDR configuration file for each tenant.
The MDR configuration file is generated automatically by Kaspersky Managed Detection and Response when you activate the solution via an activation code. The MDR configuration file is a ZIP archive containing the following files:
- Kaspersky Security Network configuration file.
- BLOB (P7) file for deployment of EPP applications that support integration with MDR via Kaspersky Security Center policies.
- BAT file for deployment of legacy configurations with older versions of EPP applications that do not support integration with MDR via Kaspersky Security Center policies.
You can download the MDR configuration file with the BLOB (P7) file or with the BAT file. For details on different deployment scenarios, refer to Deployment of Kaspersky Managed Detection and Response.
Download the MDR configuration file and use it according to the instructions for the EPP applications installed on your assets:
- Kaspersky Endpoint Security for Windows
- Kaspersky Endpoint Security for Linux
- Kaspersky Endpoint Security for Mac
Downloading the MDR configuration file in Kaspersky Security Center
To download the MDR configuration file in Kaspersky Security Center:
- In your Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, click MDR in the left panel, and then click the Licenses tab.
- Select the Archive for asset configuration column and click Download to download the MDR configuration file for a current license.
Downloading the MDR Configuration file in MDR Web Console
To download the MDR configuration file in MDR Web Console:
- Open Getting started page in MDR Web Console (https://mdr.kaspersky.com/guide). The Getting started page is available for logged-in users only.
- In step 4, click the
MDR configuration file(BLOB file included) orMDR configuration file(BAT file included) link.
A notification about whether the solution is enabled is displayed in the lower part of MDR Web Console at all times.
Page top
Licensing
This section covers the main aspects of Kaspersky Managed Detection and Response solution licensing.
Comparison of commercial license tiers
The set of features available in Kaspersky Managed Detection and Response depends on the tier of your commercial license (see the table below).
Comparison of Kaspersky Managed Detection and Response commercial license tiers
Feature |
MDR / MDR Expert |
MDR Optimum* |
MDR Basic* |
MDR Advanced* |
MDR Prime* |
|---|---|---|---|---|---|
24x7 monitoring, incident detection and management |
|
|
|
|
|
Automatic threat hunting |
|
|
|
|
|
Response playbooks and automatic incident response |
|
|
|
|
|
Security health check and asset visibility |
|
|
|
|
|
Kaspersky MDR Web Console with dashboards and reports |
|
|
|
|
|
Ability to receive advanced incident information |
|
|
|
|
|
Incident history retention period |
1 year |
1 year |
1 year |
1 year |
1 year |
Raw data retention period |
3 months |
1 month |
1 month |
3 months |
3 months |
Managed threat hunting and incident investigation |
|
|
|
|
|
Extended expert support for incident management |
|
|
|
|
|
Access to Kaspersky Threat Intelligence Portal |
|
|
|
|
|
API for exporting Kaspersky MDR data |
|
|
|
|
|
Customers can create a custom incident to be processed by the Kaspersky MDR solution** |
|
|
|
|
|
Localized data storage and workgroups |
|
|
|
|
|
Multitenancy |
|
|
|
|
|
Adding and editing comments to incidents |
|
|
|
|
|
Adding and editing attachments to incidents |
|
|
|
|
|
Advanced incident investigation: analysis to establish the background, circumstances and detailed attack mechanism |
|
|
|
Customers cannot choose the incidents for advanced investigation; there is no guaranteed incident response time |
Customers can choose the incidents for advanced investigation (within the purchased time limit); there is a guaranteed incident response time |
*This tier is available for some regions only and may be unavailable for purchase by new customers. Contact your Kaspersky Managed Detection and Response solution provider for details about the commercial license tiers available to you.
**Kaspersky Managed Detection and Response solution ensures processing of three requests per week in accordance with performance targets of the solution delivery. The number of requests processed in accordance with performance targets of the solution delivery is increased proportionally: for every 10,000 connected endpoints, the number of requests is increased by 1.
Page top
About the license
A license is a time-limited right to use the application, granted under the Terms and Conditions.
A license grants you the following kinds of services:
- Use of the application in accordance with the Terms and Conditions
- Getting technical support
The scope of services and validity period depend on the type of license under which the application was activated.
The following license types are provided:
- Trial—A free license intended for trying out the application.
A trial license usually has a short term. When the trial license expires, all Kaspersky Managed Detection and Response features become disabled. To continue using the application, you need to purchase a commercial license.
You can activate the application under the trial license only once.
- Commercial—A paid license granted upon purchase of the application.
When the commercial license expires, the application continues running with limited functionality (telemetry is not provided). To continue using all of the features of Kaspersky Managed Detection and Response, you must renew your commercial license.
We recommend renewing the license before its expiration, to ensure maximum protection against all security threats.
- Subscription—A paid license that enables the application usage for a monthly or annual billing period, with auto-renewal, until canceled or expired.
The subscription license can be of two types:
- Limited—Automatically renewed at the end of each billing period up until the defined expiration date.
- Open-ended—Auto-renewed at the end of each billing period until canceled by the customer.
You can manage the subscription license via the Kaspersky License Management Portal (LMP).
If you change your license scope, for example change the number of assets, the license details are updated in MDR Web Console within 24 hours.
When the subscription license is canceled or expired, the application continues running with limited functionality (telemetry is not provided). To continue using all of the features of Kaspersky Managed Detection and Response, you must renew your subscription license.
We recommend renewing the license before its expiration, to ensure maximum protection against all security threats.
A Kaspersky Managed Detection and Response license also grants usage of the Kaspersky Endpoint Detection and Response Optimum solution. The solution becomes available on an asset after configuring integration between Kaspersky Managed Detection and Response and Kaspersky Endpoint Agent.
Page top
About the activation code
An activation code is a unique sequence of 20 letters and numbers. You have to enter an activation code in order to add an activation code for activating Kaspersky Managed Detection and Response. You receive the activation code at the email address that you provided when you bought Kaspersky Managed Detection and Response.
To activate the solution by using the activation code, you need internet access in order to connect to Kaspersky activation servers.
If you have lost your activation code, contact the Kaspersky partner from whom you purchased the license.
Page top
Providing a new activation code
You must provide a new activation code for Kaspersky Managed Detection and Response, for example, when you want to upgrade the solution or when you need to renew your expiring license.
This feature is only available if you have the Application integration access right set in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console.
To enter a new activation code for Kaspersky Managed Detection and Response:
- In the MDR section of Kaspersky Security Center window, click the MDR Usage tab.
- In the License usage block, click the Enter a new activation code link.
- In the notification message window, click the OK button.
The start screen of Kaspersky Managed Detection and Response is displayed.
- Click the Activate the solution button.
- Kaspersky Managed Detection and Response checks whether you are signed in to your Kaspersky account:
- If you are signed in, enter the new activation code, select your region, and then click the Activate button.
- If you are not signed in, sign in with your Kaspersky account, enter the new activation code, select your region, and then click the Activate button.
- Select the tenants to which the users of this Administration Server will have access.
The new activation code is applied. Kaspersky Managed Detection and Response works under the license provided.
About the MDR Agreement
The MDR Agreement is a binding agreement between you and AO Kaspersky Lab, stipulating the terms of how you may use the solution.
Carefully read the MDR Agreement before you start using the solution.
You can view the MDR Agreement:
- During the activation of Kaspersky Managed Detection and Response.
- By clicking the Terms of using the MDR solution link in the Terms of using the MDR solution block (the MDR section of Kaspersky Security Center → MDR Usage → Terms of using the MDR solution).
You accept the terms of the MDR Agreement by confirming that you agree with the MDR Agreement when activating the solution. If you do not accept the MDR Agreement, cancel the activation of Kaspersky Managed Detection and Response, and do not use the solution.
About the Data Processing Agreement
The Data Processing Agreement (DPA) is an integral part of the Kaspersky Managed Detection and Response Agreement. The Data Processing Agreement applies to the processing of user data by AO Kaspersky Lab on behalf of a user.
The content of the Data Processing Agreement (DPA), its availability in the solution interfaces, and the list of user's data depends on the region where the solution is used.
You can view the Data Processing Agreement:
- During the activation of Kaspersky Managed Detection and Response (for some regions only).
- In the About section of MDR Web Console: https://mdr.kaspersky.com/about (for some regions only).
The About section is available only for logged-in users.
- In the set of documents you get when you buy Kaspersky Managed Detection and Response solution (for some regions only).
Carefully read the Data Processing Agreement before you start using the solution.
You confirm that you have fully read and understood the Data Processing Agreement when you activate the solution, or when you purchase the Kaspersky Managed Detection and Response solution. If you do not agree that your data will be processed as described in the Data Processing Agreement, cancel the activation of Kaspersky Managed Detection and Response, and do not use the solution.
Page top
Revoking your consent with the terms of using the MDR solution
If you decide to stop using Kaspersky Managed Detection and Response, revoke your consent with the terms of using the MDR solution, and then disable the use of Kaspersky Managed Detection and Response on the assets.
This feature is only available if you have the Application integration access right set in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console.
To revoke your consent with the terms of using the MDR solution:
- In the MDR section of Kaspersky Security Center window, click the MDR Usage tab.
- Expand the Terms of using the MDR solution block by clicking its name.
- Click the Revoke the confirmation of acceptance of the terms of using the MDR solution link.
- Confirm that you want to revoke your consent with the terms of using the MDR solution.
Your consent with the terms of using the MDR solution is revoked.
If you want to remove the information about your organization from the MDR infrastructure, please contact Technical Support.
Managing licenses in Kaspersky Security Center
If your organization has multiple current licenses, you can only manage them in Kaspersky Security Center.
The MDR Administrator role is required to manage licenses.
To view licenses,
In the MDR section of Kaspersky Security Center, click the Licenses tab.
The License keys used by your organization list appears. The top panel lists general information about licenses:
- Region
- Commercial license tier
- Total number and limit of connected assets
The Active tab only shows current licenses. Click the All tab to view all licenses in your organization.
The table shows the following information about license certificates:
- License name
- Connected assets / limit
- ID
- Activation date
- Expiration date
- Status
To download a CSV file with current licenses,
Click Export by tenants to CSV.
The CSV file includes the distribution of assets by tenant for each license.
To download the MDR configuration file for a license,
Select the Archive for asset configuration column and click Download.
To add an activation code,
Click the Add new license key button and enter the activation code in the invoked panel.
The license tier and region of the new license must match the license tier and region of other activation codes in your organization.
To remove a current license:
- Locate the Actions column and click the
 icon.
icon. - In the windows that opens, confirm deletion of a current license.
The license status changes to Removed. You can re-add the activation code to activate the license.
Data provision
In order for some components of Kaspersky Managed Detection and Response to work, it's necessary for Kaspersky to process the user's data. Components do not send data without the permission of the Kaspersky Managed Detection and Response administrator.
The list of user's data depends on the region where the solution is used. For your region, the list of user data may differ from that listed in this section.
Kaspersky protects any information received in accordance with law and applicable Kaspersky rules. Data is transmitted over a secure channel.
List of data on events occurring on User devices
In order to identify new and challenging data security threats and their sources, as well as threats of intrusion, and to take prompt measures to increase the protection of the data stored and processed with a computer by the Customer, the Customer agrees to automatically provide the following information in order to receive the Service:
- The date of software installation and activation; full name and version of the software, including information on installed updates; and the localization language of the software.
- Information about the software installed on the computer, including the operating system version and the date of its download and installed updates, and about kernel objects, drivers, services, Autostart entries, programs that are automatically launched in the event of various system events (e.g., operating system startup, user login, etc.) and their configurations, browser extensions, Microsoft Internet Explorer extensions, print system extensions, Windows Explorer extensions, operating system shell extensions, loaded object checksums (MD5), Active Setup elements, and control panel applications, browser and mail client versions.
- Information about file system permissions, the effective bit for file system permissions, file system permission versions, environment variables, and names of system calls.
- Information about inherited permissions for a system file.
- Information about the computer's name, IP addresses, default gateways, MAC addresses and hardware, including a checksum of the HDD's serial number, the last 12 bytes of the computer security ID (SID), and the security zone identifier contained in the NTFS data stream.
- Information about the software tools used to fix problems in the software installed on the User's computer, or to change its functionality, and the return codes received after the installation of each piece of software.
- Information about the state of the computer's anti-virus protection, including the versions and release dates and times of the anti-virus databases in use, statistics about updates and connections to AO Kaspersky Lab's services, job identifiers, and the identifiers and versions of the software components performing the scan, flags denoting the internal Kaspersky testing environment, the primary error codes for a specific event, the secondary error codes for a specific event, and the ordinal numbers of events.
- Current license and serial number of AO Kaspersky Lab products, and names and versions of these products. Identifiers of AO Kaspersky Lab product installations, and the client description from the license information file.
- Information about Customer user accounts: user account name, name of the user, operating system identifier, logon information, privileges, group memberships, types of logon sessions to the system, name of the authentication packet, domain names, DNS names used for authentication system logon sessions, the server name used for authentication, the user principal name (UPN) for the account, and the SID.
- Full content of operating system logs.
- Information about call systems.
- Information about detection from AO Kaspersky Lab programs that support Kaspersky Managed Detection and Response.
- Information about received emails, including: sender and recipient email addresses, subject, attachment information: attachment file name, size, hash (MD5), and file format analysis results.
- Information about the coordinates of the screen area where the screenshot was taken.
- Information about network connections, including sender and receiver IP addresses and ports, IPv6 zone indices, information about the direction of the network connection (inbound/outbound), the types and masks of DNS queries made, error codes for a DNS query operation, response to a DNS query, and information about the requested DNS server.
- HTTP connection data and methods, including visited web addresses, referrer URLs, user agents, and network authentication protocol data: MD5 hash of data for Kerberos authentication, account or computer name, the name of the Kerberos realm name to which the server name belongs, the domain to which the client name belongs, the UPN for the account, the cryptography package that was used for the issued Kerberos ticket, the flag mask for the Kerberos ticket in hexadecimal format, the Kerberos ticket issue time, the Kerberos ticket expiration time, the expiration date of the ticket (after which the ticket cannot be renewed), and the name of the domain controller used to issue the Kerberos ticket.
- Information about application layer protocols: LDAP search request size, LDAP search request filter, unique name of the LDAP search request, list of attributes for the LDAP search request.
- .NET information: full name of the downloaded .NET build, assembly flags for the downloaded .NET build, module flags for the downloaded .NET module, the domain name for the downloaded .NET build, modules for the generated MSIL stub, information about the managed method: the namespace of the managed method of interoperation, name of the managed method of interoperation, signature of the managed method of interoperation, signature of the native method, and signature of the method stub.
- Information about files processed in the operating system: file name and path, size, attributes, file and object types, results of file format analysis, checksum (MD5), web address of the file download, sender email address from which the file was received and the subject of the email, the contents of the file system of the VERSIONINFO structure in the file metadata, information about the publisher if the file is signed, the user ID of the file owner, the group ID of the file owners, the timestamp of the last file access, the timestamp that the file metadata was last modified, file creation, the digital signature verification flag masks, the timestamps and codes of operations on files and objects, the number of executable file launches, the file format identifier, the full path to the object and path to the object container, the contents of the autorun file, and the file name and path to the file on the remote network resource that is being accessed.
- Contents of the \etc\ directory.
- Command output data.
- Audit data: operation result, operation description, event type, and operation user.
- Information about the process: process identifier (PID), process call tracing, information about the process executable file and its command line, information about the parent process, MD5 hash of the executable file computation error code, primary error codes, process integrity information, session logon information, command line, command line arguments for the process, environment variables for the target process, unique identifier of the process activity log, name and/or address of the code injection site, information about access rights for the process, error codes for calculating the MD5 hash for an object from the process command line, a list of file wrappers that encapsulate the object, the initial working directory for the target process, and the array of identifiers (PIDs) for processes that are complete.
- Registry information: names, sections, and values.
- Information about remote operations: the name of the remote computer and the fully qualified (FQDN) name of the remote computer on which the remote operation was performed, the name of the user account that initiated the remote operation, the system-provided identifier of the remote process that initiated the remote operation, the start time of the remote process that initiated the remote operation, the name of the namespace for the user of the WMI events, the name of the user's WMI events filter, the name of the created user of WMI events, and the source code of the user of the WMI events.
- Error information: error code for the MD5 calculation, file access error code, primary error codes, and secondary error codes.
- Information about response event tasks created by AO Kaspersky Lab specialists and the User's specialists: event name and type, date and time when the event occurred, settings and results of the response task (information about the object [path to the object, object name and size, and MD5 and SHA256 checksums], information about quarantining the object, information about deleting the object, information about process termination, information about deleting a registry key/branch, information about process startup, information about objects requested by AO Kaspersky Lab specialists for detailed analysis upon the User's consent [name, path, size and type of the object, MD5 and SHA256 checksums, object description, date and time of file request processing, and file contents], information about the installation and removal of network isolation of the device, and information about errors resulting from the response task).
- Data about scripts running on the computer: command line arguments, contents of the script or part of the script running on the computer, and contents of the object or part of the object received by AMSI.
- Data about commands received by the console application, including the command-line interpreters, using input redirection via a pipe or file, as well as commands executed by the user in console applications, including the command-line interpreters.
List of data about events detected as a result of network traffic analysis
In order to identify new and challenging data security events and their sources, as well as threats of intrusion, and to take prompt measures to increase the protection of the data stored and processed with a computer by the Customer, the Customer agrees to provide the following information automatically in order to receive the Service:
- Information about the identifier, version, type, and timestamp of the record in the anti-virus database used to detect an information security event, the name of the threat based on AO Kaspersky Lab classification, timestamp of anti-virus databases being used, file type code, file format identifier, the task identifier of the software that detected the event, flag of the reputation verification, or file signature verification.
- Information to determine the reputation of files and web resources, including IP address and the domain name of the URL address at which the reputation is being requested, the name of the file that was executed at the time the event was detected, the file path and checksums (MD5) of the file, and its path.
- Information about emulation of the executable file, including file size and its checksums (MD5, SHA256, SHA1), the version of the emulation component, emulation depth, an array of properties of logical blocks and functions within logical blocks obtained during the emulation, and data from the executable file's PE headers.
- Information about all detected objects, including the name and size of the object, the full path to the object on the computer, checksums (MD5, SHA256) of the files being processed, the name of the event associated with the object, detection date and time, flag of the presence of the file's digital signature, the name of the organization that signed the file, the trust status and threat level of the file, the identifier and priority of the rule used for detection, and the type of detection technology.
- The type of source from which the object was downloaded, the source's IP address (or checksum (MD5) of the IP address, when it is local), the source's URL address, as well as the referrer URL address, the name, the domain's name and checksum (MD5) of the name of the host, that sent the downloading request, and the service information about the web-browser, that sent the downloading request.
- Checksums (MD5) of the local and domain parts of the sender's and the receiver's email addresses, as well as the checksum (MD5) of the email's subject.
- Local and remote IP addresses of the network connection, the numbers of the local and remote ports, and the connection's protocol identifier.
- URL address and name of the target host, and the host's IP addresses.
- The identifier of the operating system, that is installed on a virtual machine, that is used by the software to analyze objects.
- Additional information about events, including the frequency index of the file in the User's local network, the date of the file's intrusion in the local network and on the User's computer, the identifiers of the accounts the process was started from, checksums of their user names, as well as the names of their domains or workgroups, and information about the privileges of user accounts.
- Information about the network activity of the process, including the domain names of the network resources that are used to establish a connection, and IP addresses of the domains, the frequency of the connection to the selected network resource, the size and type of the transferred data.
- Information about the usage of the domain of the network resource, including the frequency index of the requests to the domain from the local network, the time stamp of the first request to the domain from the local network, the duration of the requests from different users and checksums of their names, the names of the computers that initiated the requests to the domain, and additional information about detection reasons.
- Service information about the statistics processing component, including the date and time of the beginning and the end of the term that was used to analyze the statistics data, the volume of the free and used disk memory, the time of the last event processing, the operating time of different detection algorithms, messages about the component's errors, and messages about the successful start of different detection algorithms.
- Data sent to technical support.
Data provision while using Kaspersky Endpoint Agent
For details about the provision of data while using Kaspersky Endpoint Agent, refer to Kaspersky Endpoint Agent for Windows.
Page top
Engaged sub-processors
The following sub-processors are engaged for the processing of user data, according to the Kaspersky Managed Detection and Response Data Processing Agreement:
Sub-processors engaged by AO Kaspersky Lab
Name and address of another processor |
Region of data processing |
Subject-matter of the subcontracting |
Information about a contract regarding subcontracting |
|---|---|---|---|
Amazon Web Services EMEA SARL, 38 Avenue John F. Kennedy, L-1855, Luxembourg Hd.: AWS EMEA Legal Sparkoo Technologies Ireland Co., Limited, Address 2nd Floor, Mespil Court, Mespil Road, Ballsbridge, Dublin 4, Dublin D04 E516 |
Europe, Canada |
Cloud Infrastructure service |
AWS GDPR Data Processing Addendum Sparkoo Technologies Ireland Co., Limited Data Processing Addendum |
General Cloud computing company (Alibaba Cloud), King Abdullah Financial District Floor 6 – P.O BOX 34555, Post Code 11312, Riyadh, Saudi Arabia |
Kingdom of Saudi Arabia |
Cloud Infrastructure service |
Data Processing Addendum and Standard Contractual Clauses (alibabacloud.com) |
Yandex.Cloud LLC, |
Russia |
Cloud Infrastructure service |
Offer to Enter into the Contract to Use Yandex.Cloud Platform Services |
Regions of data processing
User data is processed in the following regions, according to the Kaspersky Managed Detection and Response Data Processing Agreement:
Regions of data processing
Region of license use |
Region of data processing |
Europe, Canada |
Europe |
Kingdom of Saudi Arabia |
Kingdom of Saudi Arabia |
Russia and other regions, except those listed above |
Russia |
The region of data processing depends on the region you select when activating Kaspersky Managed Detection and Response to ensure compliance with legal requirements regarding the processing of user data.
Page top
About Kaspersky Security Network
Kaspersky Security Network (KSN) is an infrastructure of cloud services providing access to the online Kaspersky Knowledge Base that contains information about the reputation of files, web resources, and software.
For more detailed information about sending Kaspersky the statistical information that is generated during participation in KSN, and about the storage and destruction of such information, please refer to the Kaspersky Security Network Statement and the Kaspersky website.
KSN Infrastructure
Kaspersky Security Network has the following infrastructural solutions:
- Global KSN is the solution that is used by most Kaspersky applications. KSN participants receive information from Kaspersky Security Network and send Kaspersky information about the objects detected on the user's computer to be analyzed additionally by Kaspersky analysts, and to be included in the reputation and statistical databases of Kaspersky Security Network.
- KPSN (Kaspersky Private Security Network) is a solution that enables users of computers hosting Kaspersky applications to obtain access to the reputation databases of Kaspersky Security Network, and to other statistical data, without sending data to KSN from their own computers. KPSN is designed for corporate customers who are unable to participate in Kaspersky Security Network for any of the following reasons:
- Local workstations are not connected to the internet.
- Transmission of any data outside the country or outside the corporate LAN is prohibited by law or restricted by corporate security policies.
For operation of Kaspersky Managed Detection and Response, it is required to use KPSN. KPSN is configured automatically in Kaspersky Security Center during the activation of Kaspersky Managed Detection and Response solution. When you revoke your consent with the terms of using the MDR solution, KPSN is automatically disabled.
For details on configuring KPSN, refer to Kaspersky Security Center documentation.
Page top
Periodic update of KSN configuration files
To ensure secure transmission of customer telemetry to Kaspersky Managed Detection and Response, Kaspersky periodically updates the encryption keys for MDR telemetry data. The public key is transmitted as part of the KSN configuration file.
If you are using MDR Plug-in for Kaspersky Security Center Cloud Console or on-premises Kaspersky Security Center, in some cases (please check the details in the table below) the KSN configuration file will be updated automatically. However, in many cases you have to replace the installed KSN configuration file manually.
If the KSN configuration file is not updated on your assets, telemetry data will stop being sent to Kaspersky Managed Detection and Response.
No later than one month before the expiration of the current KSN configuration file, Kaspersky will notify you about the imminent expiration of the KSN configuration file. There are two notification options:
- An incident will be created, notifying you about the upcoming expiration of the current KSN configuration file.
- A notification about the upcoming expiration of the current KSN configuration file will be published in MDR Web Console. Any user logging in MDR Web Console will see this notification.
Actions required to update the KSN configuration file
The solution you use to manage your assets
The interface your SOC analysts use
Actions required
Kaspersky Security Center Cloud Console
MDR Plug-in installed in Kaspersky Security Center Cloud Console
Log in to Kaspersky Security Center Cloud Console. When you log in, MDR Plug-in tries to install the new KSN configuration file on Kaspersky Security Center Cloud Console.
If MDR Plug-in successfully updates the file, you will get a notification about the change of the KSN configuration file.
If MDR Plug-in fails to update the KSN configuration file, you will get a notification about the cause of the problem:
- Your account does not have sufficient access rights to update the file.
- An unexpected error occurred while updating the KSN configuration file.
If no notifications are displayed, it is likely that the KSN configuration file was successfully updated when another specialist connected to the Kaspersky Security Center Cloud Console.
If you see a notification about insufficient access rights to update the KSN configuration file, contact your Kaspersky Security Center Cloud Console administrator (Main administrator role) for help:
Ask the administrator to connect to Kaspersky Security Center Cloud Console. When the administrator connects, the KSN configuration file will be updated.
You can check if the KSN configuration file is up to date at any time. To do so, in the MDR section of Kaspersky Security Center click the MDR Usage tab. Information about the current version of the KSN configuration file will be shown. If a new version of the KSN configuration file is available, you can use a button to update the KSN configuration file.
If an unexpected error occurs while updating, contact Kaspersky technical support.
Kaspersky Security Center Cloud Console
MDR Web Console
OR
You use the API to download the incidents in order to process them in your own systemLog in to Kaspersky Security Center Cloud Console.
Start the Initial Configuration Wizard to activate the MDR Plug-in.
If your account does not have sufficient access rights to activate MDR Plug-in, contact your Kaspersky Security Center Cloud Console server administrator for help.
Then, follow the instructions for the Kaspersky Security Center Cloud Console server and MDR Plug-in above.
If an unexpected error occurs while updating, contact Kaspersky technical support.
On-premises Kaspersky Security Center version 14 and later
MDR Plug-in installed in on-premises Kaspersky Security Center
Log in to Kaspersky Security Center.
When you log in, MDR Plug-in tries to install the new KSN configuration file on the Kaspersky Security Center server.
If MDR Plug-in successfully updates the file, you will get a notification about the change of the KSN configuration file.
If MDR Plug-in fails to update the KSN configuration file, you will get a notification about the cause of the problem:
- Your account does not have sufficient access rights to update the file.
- An unexpected error occurred while updating the KSN configuration file.
If no notifications are displayed, it is likely that the KSN configuration file was successfully updated when another specialist connected to Kaspersky Security Center Cloud Console.
If you see a notification about missing access rights to update the KSN configuration file, contact your Kaspersky Security Center server administrator for help. Ask the administrator to connect to the Kaspersky Security Center server. When the administrator connects, the KSN configuration file will be updated.
If the administrator does not get the notification about the change of the KSN configuration file, the administrator should check the version of the installed MDR Plug-in, and update it to the current version if necessary (MDR Plug-in version 2.1.17 or later is required).
You can check if the KSN configuration file is up to date at any time. To do so, in the MDR section of Kaspersky Security Center, click the MDR Usage tab.
The information about the current version of the KSN configuration file will be shown.
If a new version of the KSN configuration file is available, you can use a button to update the KSN configuration file.If an unexpected error occurs while updating, contact Kaspersky technical support.
On-premises Kaspersky Security Center version 14 and later
MDR Web Console (MDR Plug-in not installed in on-premises Kaspersky Security Center
ORYou use the API to download the incidents in order to process them in your own system
Ask the MDR Web Console administrator to:
- Download the MDR ZIP archive from the Getting started page.
- Extract the KSN configuration file from the ZIP archive.
- Send this file to the Kaspersky Security Center Administration server administrator.
Ask the Kaspersky Security Center server administrator to upload the KSN configuration file by clicking Administration Server properties → KSN proxy server settings → KSN proxy server settings file.
If an unexpected error occurs while updating, contact Kaspersky technical support.
On-premises Kaspersky Security Center version 13.* or earlier
MDR Plug-in installed in on-premises Kaspersky Security Center
OR
You use the API to download the incidents in order to process them in your own system
If there are multiple Kaspersky Security Center servers installed in your network, you have to update the KSN configuration file on each server.
Updating the KSN configuration file on KATA servers
If there are KATA servers that are connected to Kaspersky Managed Detection and Response in your network, you have to update the MDR configuration file on these KATA servers.
Please ask the MDR Web Console administrator to download the MDR configuration ZIP archive from the Getting started page: https://mdr.kaspersky.com/guide.
The Getting started page in MDR Web Console is available for logged-in users only.
When you get the MDR configuration ZIP archive, please ask the KATA server administrator to upload the MDR configuration file to the KATA servers. In case of problems during an MDR configuration file update, the KATA server administrator should contact Kaspersky Technical Support for instructions on how to update the MDR configuration file on the KATA server.
Monitoring dashboards in MDR Web Console
MDR Web Console provides monitoring dashboards to view summary information.
To view the dashboards:
- In MDR Web Console, navigate to the Monitoring menu item.
The Summary page opens.
- The following dashboards are present on the Summary page:
- Maximum assets for license
This is a pie chart that shows the number of connected assets versus the maximum number of assets available for the license.
- Assets by status
This is a pie chart that shows the distribution of assets by their status.
- Active incidents
This is a pie chart that shows the distribution of active incidents, according to their statuses.
- Responses
This is a pie chart that shows the distribution of responses, according to their statuses.
The number of connected assets represents assets that were seen in MDR Web Console in the last 7 days. If you want to get the number of connected assets for a specific period of time, navigate to the Assets menu item of MDR Web Console.
- Telemetry statistics
This is a dashboard that shows the telemetry statistics of the MDR solution for a client, including statistics by specific tenants. You can view data for 1 day, 7, 30, 90, 180 days, for 1 year, or for the entire period a client continuously uses the MDR solution.
This dashboard displays the number of each of the following objects:
- Telemetry events are all of the events sent from a client’s assets to Kaspersky Managed Detection and Response.
- Suspicious events are telemetry events that Kaspersky Managed Detection and Response determines as events that require additional check.
- Security events are telemetry events that the detection rules determine as potential incidents.
- Incidents are actions that the detection technology determines as critical. Incidents require immediate reaction (response action) from Kaspersky Managed Detection and Response.
- Detection rules triggered is a number of unique detection rules triggered on specified telemetry events for a specified time period.
- Number of incidents
This is a dashboard that shows the number of incidents and their statuses, by day of the week.
- Maximum assets for license
Dashboards are updated with every refresh of the Summary page.
To switch dashboards to tenant-specific statistics:
- At the top of the Summary page, click Filter by tenant.
- In the invoked menu, select one or multiple tenants.
- Click Save.
Tenant-specific statistics are available for the following widgets:
- Assets limit for this license
- Assets by status
- Active incidents
- Number of incidents
- Responses
- Telemetry statistics
Receiving summary information
Kaspersky Managed Detection and Response provides several types of summary information that you can receive via email. This section describes how to configure receiving summary information.
Receiving a summary of all assets in a CSV file (MDR Web Console)
You can receive a summary as a CSV file that contains all the assets from your account. No filters are applied to the summary, i.e., the number of the assets in this summary represents all assets that were seen in MDR Web Console.
You can hide assets with the Absent status in the summary by selecting the corresponding check box in the Settings.
To receive a CSV summary:
- In the MDR Web Console, navigate to the Assets menu item.
The asset list opens.
- Click the Receive a CSV summary by email button in the upper part of the window.
The summary is sent to the email address that was specified during the activation of Kaspersky Managed Detection and Response.
Receiving incident information as a PDF (MDR Web Console)
You can receive a summary information about a particular incident as a PDF.
To receive a PDF summary:
- In MDR Web Console, navigate to the Incidents menu item.
The incident list opens.
- Click the incident whose summary you want to receive.
The incident card appears.
- Click the Receive a PDF summary by email link in the upper part of the window.
The summary is sent to the email address that was specified during the activation of Kaspersky Managed Detection and Response.
Setting up regular report delivery in MDR Web Console
This feature is only available in MDR Web Console.
You can schedule receiving a summary report that contains data about open incidents. Each set of delivery settings is saved as a schedule. You can create no more than 50 schedules for an organization, and no more than 10 schedules for each tenant.
To create or edit report delivery schedules, you must have the MDR Administrator user role.
The report is sent by email in an open, unencrypted PDF format to the addresses you specified and according to the defined schedule.
The report always contains data for the last seven days, and the report generation day is not included. In other words, if you configure to receive the summary report every day, your daily report will contain data for the previous seven days, excluding the current day. If you configure receiving the summary report every Wednesday, report will contain data from the previous Wednesday to the following Tuesday.
To set up receiving the summary report as a PDF file:
- In the Settings section of the MDR Web Console, click the Schedules tab.
- Click the Add button.
The Add new schedule window opens.
- Turn on the toggle switch to the Enabled position.
- Carefully read the notification below regarding the terms and conditions of sending the summary reports. Then, select the check box to confirm that you have read and understand the terms and conditions. If the check box is not selected, you cannot save the changes you make.
- Specify the following settings:
- In the Schedule name field, specify an arbitrary, human-readable name of the summary report. The name should contain Latin letters, digits, and special characters; it cannot be longer than 1000 characters.
- In the Tenant field, select the tenant for which you want to receive a summary report. The report will contain data from the selected tenant only. Alternatively, if you want to receive a summary report about all of the tenants, select All tenants.
- In the To emails field, specify an email address or comma-separated list of email addresses of users who will be receiving the summary.
Double check the email addresses entered, since they will be added without further confirmations. The summary reports can contain sensitive data, and will be sent in an open, unencrypted PDF format.
- In the Sending day field, select the days of the week when the summary should be sent to the specified email addresses. You can choose one day or Every day.
- In the Time, UTC field, specify time in 24-hour UTC format. For example, 15:00.
The schedule only affects the time when the report is received, but does not affect the period of data in the report.
The report always contains data for the last seven days, and the report generation day is not included. In other words, if you configure to receive the summary report every day, your daily report will contain data for the previous seven days, excluding the current day. If you configure receiving the summary report every Wednesday, report will contain data from the previous Wednesday to the following Tuesday.
- Click the Save button.
The summary report will be sent to the specified email addresses on a weekly or daily basis.
Page top
Receiving notifications
You can configure the delivery of notifications about events occurring with incidents and responses as they are being processed in Kaspersky Managed Detection and Response.
Kaspersky Managed Detection and Response sends notifications to clients via Telegram or email, depending on the settings that you specify. The notification body contains a description of the event and a link to the object where the event has occurred.
You can configure the notifications in MDR Web Console and in the MDR section of Kaspersky Security Center.
Setting up notifications in MDR Web Console
To configure the delivery of notifications in the MDR Web Console:
- In the Settings section of MDR Web Console, click the Notification settings tab.
- Select the check boxes corresponding to the events that you want to receive email notifications for.
Available check boxes are:
- All—All events that Kaspersky Managed Detection and Response sends notifications about.
- Incidents—Notifications about creating, updating, resolving, and closing incidents.
- Extended notifications—A description of the attack detected as the incident, and the response recommendations. This check box is available if the extended notifications feature is enabled on the General settings tab.
- Comments—Notifications on creating, updating, and deleting comments within incidents.
- Responses—Notifications on creating, accepting, and rejecting responses.
- Information on license expiration—Notifications about the following events: less than 30 days left before the license expires, the license has expired. Kaspersky Managed Detection and Response sends these notifications every day but not after the license has expired or the license is renewed.
- Click the Subscribe button located above the check boxes, to subscribe to notifications from the Telegram chatbot. When you click the Subscribe button, the application generates and displays a unique link to activate the chatbot in Telegram. You can use this link for one Telegram account.
Use this link only on a device (desktop or mobile) where the Telegram app is installed. The link cannot activate the chatbot in the web version of Telegram.
If you want to receive notifications to another Telegram account, click the Unsubscribe button, and then repeat the subscription procedure to generate a new link and use it to activate the chatbot for another account.
- Click the Save button in the lower part of the window to save settings. The Save button becomes active only if you changed the settings.
The delivery of notifications is configured.
Page top
Setting up notifications in Kaspersky Security Center
To configure the delivery of notifications in the MDR section of Kaspersky Security Center:
- In the MDR section of Kaspersky Security Center, click the Notifications tab.
The Notifications tab opens.
- If you want to receive notifications via email, enable the Notify via email option, specify the email address, and the following notification settings:
- Specify an email address in the Email field, and then select at least one of the check boxes. Otherwise, the settings cannot be saved.
- Incidents—Notifications on creating, resolving, and closing incidents.
- Extended notifications—Notifications that contain a description of the attack detected as the incident, and the response recommendations. This check box is available if the extended notifications feature is enabled on the Settings tab.
- Comments—Notifications about creating, updating, and deleting comments within incidents.
- Responses—Notifications about creating, accepting, and rejecting responses.
- If you want to receive notifications via Telegram, enable the Notify via Telegram option, and then select at least one of the following check boxes:
- Incidents—Notifications about creating, resolving, and closing incidents.
- Comments—Notifications about creating, updating, and deleting comments within incidents.
- Responses—Notifications about creating, accepting, and rejecting responses.
Click the Get Link button located above the check boxes to subscribe to notifications from the Telegram chatbot. When you click the Get Link button, the application generates and displays a unique link to activate the chatbot in Telegram. You can use this link for one Telegram account.
- Click the Save button in the lower part of the window to save the settings. The Save button becomes active only if you changed the settings.
If you select notification via email, a unique verification code is sent to the email address that you specified. The verification code expires in 10 minutes.
The verification block appears.
In the verification block that opens, paste the confirmation code for the specified email address.
If you paste an incorrect code three times in a row or paste an expired code, the Resend button appears. Click this button to receive a new verification code.
- Once the email address is verified, the block with the corresponding message appears.
- Click the Close button in the lower part of the block.
The delivery of notifications is configured.
Receiving extended notifications
You can configure the delivery of extended incident notifications via email to MDR users. Extended notifications contain a description of the attack detected as the incident, and the response recommendations. The attack description includes some data that the MDR solution receives as telemetry from devices connected to the MDR solution, so the description can include the following sensitive information:
- Host names
- Host IP addresses
- Account names
- Account passwords (if a script containing a password was run on a device)
- Service URLs
- Filenames
- Email addresses
- Names of the departments and tenants
The complete list of data received by the MDR solution is contained in the Data provision section.
Enabling extended notifications in MDR Web Console
To enable the delivery of the extended notifications:
- In the Settings section of MDR Web Console, click the General settings tab.
- Turn on the Enable extended notification option, and then select the check box below to confirm that you have read and understand the terms of sending extended notifications.
- Click the Save button.
Now, you can subscribe to extended notifications in Notification settings of MDR Web Console.
Page top
Enabling extended notifications in Kaspersky Security Center
To enable the delivery of the extended notifications:
- In the MDR section of Kaspersky Security Center, select the Settings tab.
- Turn on the Enable extended notifications via email option, and then select the check box below to confirm that you have read and understand the terms of sending extended notifications.
- Click the Save button.
Now, you can subscribe to extended notifications in the Notifications tab.
Page top
Managing users
Kaspersky Managed Detection and Response users can have different roles, with a different functionality available for each role. The role model is a set of rules that specify user roles.
The following roles are present in Kaspersky Managed Detection and Response:
Inviting new users in MDR Web Console
To invite a new user to Kaspersky Managed Detection and Response:
- In the MDR Web Console window, navigate to the Settings menu item.
The user list opens.
- Click the Add button located above the user list.
The invitation card appears.
- In the Email field, specify an email address.
- In the User role field, specify a role for the new user.
The following user roles are available:
- MDR Administrator
Only a user with the MDR Administrator role assigned can assign the MDR Administrator role to a new user.
- Senior Security Officer
- Security Officer
- MDR Administrator
- If necessary, select the value (or values) in the Tenant drop-down list.
Tenants that already exist in Console and have the Root without tenants value are suggested.
The user can view only the assets and incidents related to the specified tenants. If you have assets and incidents not assigned to any tenants, the user can view them if you select the Root without tenants value.
You can select the Root without tenants value, in addition to specifying tenant names.
- Click Invite.
The invitation card disappears.
Enter the email address. The email address must first be registered and verified on the auth.hq.uis.kaspersky.com web portal.
A message with the invitation link is sent from noreply@mail.account.uis.kaspersky.com to the specified email address.
The invited user must verify his or her email address by following the link from the message. The user cannot log in and use Kaspersky Managed Detection and Response until their email is verified. Permissions corresponding to the user role will be granted after the first login of the user.
Page top
Changing user roles in MDR Web Console
You can change the role for an existing user. For example, an employee with the Security Officer role is assigned additional responsibilities that require the Senior Security Officer role to be assigned.
To change a role for an existing user:
- In the MDR Web Console window, navigate to the Settings menu item.
The user list opens.
- Click the string containing the user whose role you want to change.
The user card appears.
- In the user card, change the role for the existing user by selecting another role from the drop-down list of roles.
The role for the existing user is changed.
Page top
Editing user notification methods in MDR Web Console
Editing user notification methods is available only for the user who has the MDR Administrator role assigned. The user with that role can edit notification settings for all active users, including themselves.
Users with the active status can receive notifications from Kaspersky Managed Detection and Response via email and/or Telegram.
To edit the user notification methods for an existing user:
- In the MDR Web Console window, navigate to the Settings menu item.
The user list opens.
- Click the string containing the user whose role you want to change.
The user card appears.
- In the user card, specify the following options:
- Email notifications enabled
The user receives notifications to the email address specified when this user was invited.
- Telegram notifications enabled
The user receives notifications from the Telegram chatbot.
If a user has lost access to their Telegram account, select the Unsubscribe Telegram account from notifications check box. Then, ask the user to log in to MDR Web Console, go to Settings → Notification settings, and then repeat the subscription procedure to generate a new link in order to activate a Telegram subscription for another Telegram account.
- Email notifications enabled
- In the lower part of the user card, click the Save button to close the card.
The user notifications methods are edited and saved.
Editing user access to tenants in MDR Web Console
You can change user access to the tenants in your account, for example, if you add a new tenant and want an existing user to have access to it.
To change access to tenants:
- In the MDR Web Console window, navigate to the Settings menu item.
The user list opens.
- Click the string containing the user whose access rights you want to change.
The user card appears.
- In the user card, change the value (or values) in the Tenant drop-down list.
- In the lower part of the user card, click the Save button to close the card.
User access to tenants is changed.
Managing assets
An asset is a device with a Kaspersky EPP application installed (for example, Kaspersky Endpoint Security for Windows). This section provides information about viewing, sorting, and filtering assets.
Viewing and searching assets in MDR Web Console
You can view and search through available assets by using the asset list.
To view assets:
- In the MDR Web Console window, navigate to the Assets menu item.
The asset list opens. Each line represents one asset. You can click anywhere on the line to view asset information.
The following asset attributes are available to show above the list:
- If you want to change the number of assets shown per page of the list, select the number by clicking the entries per page option at the bottom of the page.
You can select 10, 20, or 50 assets per page.
You can hide assets with the Absent status in the asset list by selecting the check box in the Settings.
If you want to navigate the list of assets, select the page from below the list. You can use the Previous and Next options to switch between adjacent pages.
By default, the asset list contains assets that were seen in Console in the last 30 days.
To change this period:
- Click the funnel icon above the list.
- On the Filter panel on the right, select the period in the Last seen field.
- Click Save.
You can search through the assets by clicking the magnifying glass icon located next to the funnel icon above the asset list.
Filtering assets in MDR Web Console
You can create and apply filters to the asset list.
To create a filter for the asset list:
- In MDR Web Console, navigate to the Assets menu item.
The asset list opens.
- Click the funnel icon located above the asset list.
The Filter menu appears.
Parameters available for filtering are:
- Last seen
The moment when the asset was last seen in Console.
- Asset name
Available asset names.
An asset name is the network name of a computer.
- Tenant
Available tenant names.
You can select the Root without tenants value to view assets that are not assigned to any of your tenants.
You can select the Root without tenants value in addition to specifying tenant names.
- Status
- Isolation
Whether network isolation is enabled or not. The possible filter values are:
- Isolated
Network isolation is enabled.
- Not isolated
Network isolation is disabled.
- Isolated
- Last seen
- Click Save to apply the created filter.
Only assets that meet the selected parameters of the filter are shown in the asset list after the filter is applied.
You can hide assets with the Absent status in the asset list by selecting the check box in the Settings.
Page top
Viewing detailed information about assets in MDR Web Console
To view detailed information about assets:
- In the MDR Web Console window, navigate to the Assets menu item.
The asset list opens.
- Click the string with the asset whose details you want to view.
The asset card appears. The asset card contains two tabs:
- Properties has general information about the asset
- Incidents has information on incidents that have occurred with the asset
General information on the Properties tab contains the following information:
- Asset name
- Status
- IP address
- Physical address
- Tenant
- First seen
- Last seen
- Operating system
- Kaspersky applications that work with MDR
- Domain
The Incidents tab contains the list of incidents. The ID/Created column of the list contains an incident identifier and time the incident was created. The Status column of the list contains information on the incident status.
Asset statuses
The status reflects the current asset state. For assets in the OK, Warning, or Critical statuses, the application additionally lists the problems (if any) for the last 72 hours.
For assets with the Kaspersky Endpoint Security for Windows in the Endpoint Detection and Response Agent (EDR Agent) configuration, the Warning and Critical statuses for protection and control components may be displayed incorrectly.
The assets have one of the following statuses:
- OK (green)
Telemetry is being sent, protection is fully operational.
- Warning (yellow)
Possible reasons of the Warning status:
- Minor telemetry losses. Refer to this article: How to avoid loss of telemetry data from assets.
- At least one of the following EPP application components on the asset is disabled or not installed:
- Firewall—See how to enable or configure this component in Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, or Kaspersky Security for Virtualization Light Agent.
- Network Threat Protection—See how to enable or configure this component in Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, or Kaspersky Endpoint Security for Mac.
- Mail Threat Protection and Additional Microsoft Office Outlook Extension—See how to enable or configure these components in Kaspersky Endpoint Security for Windows.
- Web Threat Protection—See how to enable or configure this component in Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, Kaspersky Endpoint Security for Mac, or Kaspersky Security for Virtualization Light Agent.
- Product Self Defense—See how to enable or configure this component in Kaspersky Endpoint Security for Windows or Kaspersky Security for Virtualization Light Agent.
- Anti-virus databases are outdated by more than 7 days.
These components affect the fullness of sent telemetry. If a component is disabled or missing, Kaspersky Managed Detection and Response does not send the telemetry events related to this component. The installed EPP application may not include all of the listed components.
- KSN configuration file is expiring. The application displays the expiration date. Consider updating the KSN configuration file. If you keep working with the current configuration file, the status changes to Critical few days before the expiration date.
The Warning status is applicable for assets with Kaspersky Endpoint Security for Windows 11 or later, Kaspersky Endpoint Security for Linux 11.2 or later, Kaspersky Endpoint Security for Mac 11.2 or later, or Kaspersky Security for Virtualization Light Agent 5.2 or later installed. For assets with the Kaspersky Endpoint Security for Windows in the Endpoint Detection and Response Agent (EDR Agent) configuration, this status is not displayed.
- Critical (red)
Possible reasons of the Critical status:
- Major telemetry losses, telemetry data is insufficient for analysis. Refer to this article: How to avoid loss of telemetry data from assets.
- At least one of the following EPP application components on the asset is disabled or not installed:
- System Watcher or Behavior Detection—See how to enable or configure these components in Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, or Kaspersky Security for Virtualization Light Agent.
- File Threat Protection—See how to enable or configure this component in Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, Kaspersky Endpoint Security for Mac, or Kaspersky Security for Virtualization Light Agent.
If any of these components are disabled or missing, Kaspersky Managed Detection and Response stops sending telemetry from the asset. The installed EPP application may not include all of the listed components.
- KSN configuration file is expiring soon or is already expired. The application displays the expiration date. Consider updating the KSN configuration file.
This status is applicable for assets with Kaspersky Endpoint Security for Windows 11 or later, Kaspersky Endpoint Security for Linux 11.2 or later, Kaspersky Endpoint Security for Mac 11.2 or later, or Kaspersky Security for Virtualization 5.2 Light Agent or later installed. For assets with the Kaspersky Endpoint Security for Windows in the Endpoint Detection and Response Agent (EDR Agent) configuration, this status is not displayed.
- Offline (black)
No telemetry for more than 7 days (default value). You can change the number of days of absence of telemetry, after which the Offline status is displayed for the asset, in the Settings section. The available range is 2–29 days.
If you see the Offline status for your assets:
- Make sure the EPP application components listed with Warning and Critical statuses are installed and enabled on the assets.
- Make sure Kaspersky Managed Detection and Response is properly deployed in your infrastructure.
Offline status is not applicable for VDI assets (temporary virtual machines).
- Absent (black)
No telemetry for more than 30 days for physical assets or for more than 24 hours for VDI assets (temporary virtual machines).
If you see the Absent status for your assets:
- Make sure the EPP application components with Warning and Critical statuses are installed and enabled on the assets.
- Make sure Kaspersky Managed Detection and Response is properly deployed in your infrastructure.
You can hide assets with the Absent status in the asset list, in the reports, and in the data received via the API interface.
Checking assets status in Kaspersky Security Center
You can check the status of your assets by using the MDR Health functionality. It enables you to check which assets are currently protected by Kaspersky Managed Detection and Response and which ones never sent
to Kaspersky Managed Detection and Response.For assets with Kaspersky Endpoint Security for Windows 12.3 and later working in the Endpoint Detection and Response Agent (EDR Agent) configuration, the displayed status in MDR does not reflect the actual status.
Statuses of the assets that have sent telemetry at least once
To check the assets status:
- In the MDR section of Kaspersky Security Center, navigate to the MDR Health tab.
- Select the All assets ever seen tab.
A list of all assets that have sent telemetry to Kaspersky Managed Detection and Response at least once is displayed.
The following details are displayed for each asset:
- Use the following sorting and filtering options to work with this list:
- Click any column header to sort the list by the selected column values.
- Click the Status column, and then select the required statuses. The list will be filtered to show only the assets with the selected statuses.
- Click the filter icon (
 ), and then select the time period to view only those assets that were last seen during the selected time period. You can also specify a custom time period.
), and then select the time period to view only those assets that were last seen during the selected time period. You can also specify a custom time period. - Click the export icon (
 ) above the asset list to make a CSV export.
) above the asset list to make a CSV export. - Use the Search field to search for assets by name.
Statuses of the assets that never sent telemetry
This feature is working properly in Kaspersky Security Center 15.1 Windows and later versions, Kaspersky Security Center 15.1 Linux and later versions, and Kaspersky Security Center Cloud Console.
To view the assets that never sent telemetry:
- In the MDR section of Kaspersky Security Center, navigate to the MDR Health tab.
- Select the Malfunctioning assets tab.
The MDR Web Console displays a list of the assets that have been added to Kaspersky Security Center, but never sent telemetry to Kaspersky Managed Detection and Response.
The following details are displayed for each asset:
- If necessary, you can filter the assets by MDR status. To do so, click the filter icon (
 ), and then select the required MDR statuses. The MDR Web Console will display only those assets on which the MDR component has one of the selected MDR statuses. Alternatively, select one of the following options:
), and then select the required MDR statuses. The MDR Web Console will display only those assets on which the MDR component has one of the selected MDR statuses. Alternatively, select one of the following options:- Installed and activated—The list will be filtered to display the assets that have one of the following MDR statuses: Unknown, Stopped, Paused, Starting, Running, or Failed.
- License is missing or expired—The list will be filtered to display the assets that have the No license MDR status.
- If necessary, click the Export button to export the asset list to a CSV file.
How to avoid loss of telemetry data from assets
Assets send telemetry data to Kaspersky Managed Detection and Response to detect and analyze security incidents in your infrastructure. If you see that there are telemetry losses in the asset status, make sure the following instructions are completed:
- The recommended versions of Kaspersky applications are installed on your assets (see Recommended versions and their term of support column in the Compatible Kaspersky applications versions section of Hardware and software requirements).
- Your network channel throughput meets the specifications provided in the Network channel section of Hardware and software requirements.
- Your KSN proxy server provides sufficient throughput capacity.
If there are issues with the KSN proxy server throughput capacity, disable the KSN proxy in the KSC policy, to force the assets to connect to KSN directly:
- In the Kaspersky Security Center main menu, go to Devices → Policies & profiles.
- Click the policy for Kaspersky Endpoint Security for Windows, Linux, or Mac. The properties window of the selected policy opens.
- In the policy properties, click Application settings → Advanced Threat Protection → Kaspersky Security Network.
- Enable the Use KSN servers when KSN Proxy is not available option (if applicable for the policy).
- Click OK.
- KSN Proxy is enabled on the distribution point side in Kaspersky Security Center Cloud Console or Kaspersky Security Center Web Console to optimize the network load.
- Your Kaspersky Security Center Administration Server workload does not exceed the limitations.
- The recommended version of Kaspersky Security Center specified in Hardware and software requirements is used, latest available hotfixes and patches are installed.
Managing incidents
An incident is an activity evaluated as critical by the detection technology and which requires immediate reaction from the online service. This section provides information about managing existing incidents and adding new incidents.
With the release of MDR Plug-in version 2.3.1, the incidents management functions have been removed from the MDR section in Kaspersky Security Center. You can manage incidents in MDR Web Console.
If you use MDR Plug-in version 2.3.0 or earlier, we recommend managing incidents in MDR Web Console, since the incident management functions in Kaspersky Security Center with MDR Plug-in are no longer being developed.
To manage the incidents in MDR Web Console, you should create a Kaspersky Account and ask your MDR administrator (the user of MDR Web Console with MDR Administrator role) to invite you in MDR Web Console by using the email address you use for your Kaspersky Account.
Then, you receive the invitation email containing the link to MDR Web Console.
About the incidents
What is an incident
In the context of information security, an incident is any unforeseen or undesirable event that could disrupt normal activity or information security.
An event is the identified external signs of a particular state of a system, service, or network.
Within the framework of the Kaspersky MDR solution, the main criterion for deciding whether the observed activity is an incident is the ability to implement efficient measures to counter, prevent, or reduce possible damage resulting from this activity. See the table below for examples of possible incident criteria and responsive measures depending on the event source.
Examples of incident detection criteria and response measures
Event source |
Possible incident criteria |
Possible incident responses |
|---|---|---|
Endpoint device |
|
|
Endpoint device + network |
Security event from a supported network detection technology that has been confirmed on the endpoint device |
|
Incident detection scenarios
Scenario 1. Incident detection by the Kaspersky MDR solution
In this scenario, an information security incident is detected as a result of the Kaspersky MDR operation. The incident is logged automatically in the incidents tracking system. The default incident priority level can be changed later, but it will require to specify the reason of the change according to the incident priority level table (see below). Kaspersky MDR processes the logged incidents to promptly obtain information about the status of the customer's IT infrastructure.
If root causes of the incident are identified as a result of the analysis, then response recommendations are provided to the customer. If there is not enough information to identify the root cause of the incident, all the available information and the results of analysis are provided to the customer for independent research.
Scenario 2. Incident detection by the customer (creating custom incidents is not available in some of the commercial license tiers)
In this scenario, an information security incident is detected by the customer, independently from the Kaspersky MDR operation. If the incident needs to be processed by Kaspersky MDR, the customer may log the incident manually and provide all the available information about the detected incident by using the Kaspersky MDR features. By default, the incident priority level is set to Low, unless specified otherwise by the customer while logging the incident.
Further processing of the incident is similar to Scenario 1.
Incident priority levels
Incident priority levels and their descriptions
Incident priority level |
Description |
|---|---|
High |
Incidents that, in AO Kaspersky Lab expert opinion, may result in major disruptions or unauthorized access to the customer's assets monitored by Kaspersky MDR. For example, identified traces of a targeted attack or of an unknown threat, requiring further investigation by using digital forensic methods. |
Medium |
Incidents that, in AO Kaspersky Lab expert opinion, may affect the efficiency or performance of the customer's assets monitored by Kaspersky MDR, or may result in a one-time data corruption. |
Low |
Incidents that, in AO Kaspersky Lab expert opinion, do not significantly affect the efficiency or performance of the customer's assets monitored by Kaspersky MDR. For example, identified potentially unwanted software such as adware or riskware. |
The default incident priority level is Low.
Performance targets of the solution delivery
Target reaction time and value of Kaspersky MDR delivery depending on the incident priority
Incident priority level |
Reaction time* |
Target value** |
|---|---|---|
High |
1 hour |
90% |
Medium |
4 hours |
90% |
Low |
24 hours |
90% |
The incident is considered as resolved if recommendations of response measures were provided to the customer.
*Reaction time is the time between incident detection (creation time) and publishing it to MDR Web Console (update time).
**Target value is the percentage of incidents where the reaction time meets the objective specified in the table.
Page top
Viewing and searching incidents in MDR Web Console
To view incidents:
- In the MDR Web Console, navigate to the Incidents menu item.
The incident list opens. Each line represents one incident. You can click anywhere on the line to view incident information.
The following incident attributes are present above the list:
- ID/Created—Numeral identifier of the incident in the Console / date the incident was created.
- Status—One of the following incident statuses:
- Open—The incident has to be processed by the security team.
- Resolved—The incident received a response created by the security team.
- On hold—The incident has temporarily stopped being processed by the security team.
- Closed—The incident was processed by the security team and no more work needs to be done on it.
- Summary—Brief commentary about the whole incident.
- Tenant—A tenant that an incident is assigned to.
- Updated—Date and time when the incident was updated.
Incidents are sorted according to their update time in descending order.
You can add or remove attributes (columns) and reorder them by clicking the gear icon above the list.
- If you want to change the number of incidents shown per page of the list, select a number by clicking the Entries per page option in the lower part of the page. You can select 10, 20, or 50 incidents per page.
To navigate the list of incidents, select a page from below the list. You can use the Previous and Next options to switch between adjacent pages.
In order to filter the incidents, click the funnel icon above the list.
You can search through the incidents by clicking the magnifying glass icon located next to the funnel icon above the incident list.
Filtering incidents in MDR Web Console
To view specific incidents, you can create and apply filters to the incident list.
To create a filter for the incident list:
- In MDR Web Console, click the Incidents menu item.
The incident list opens.
- Click the funnel icon located above the incident list.
The Filter block appears.
Parameters available for filtering are:
- Created
Time period for incident creation.
- Updated
Time period for incident update.
- Priority
Incident priority. Available priorities are Low, Medium, and High.
- Status
Incident status.
- Resolution
Resolution for incident.
- Assets
Available assets.
- Tenant
Available tenant names.
You can select the Default tenant value to view incidents that are not assigned to any of your tenants.
You can select the Default tenant value in addition to specifying tenant names.
- Tactics
Available MITRE tactics for incident response.
- Response statuses
Show only incidents with the selected statuses of corresponding responses.
- Created
- Click Save to apply the created filter. Click Clear to discard the created filter.
Only incidents that meet the selected parameters of the filter are shown in the incident list after the filter is applied.
Page top
Creating custom incidents in MDR Web Console
Creating custom incidents is not available in some of the commercial license tiers.
If you consider some activity in your infrastructure to be a threat but Kaspersky Managed Detection and Response did not create an incident automatically, you can add a new incident manually.
According to the terms of the service level agreement (SLA), the number of manually created incidents that are eligible for processing by the security team is limited. Information about the limitations is available on the MDR Usage tab in Kaspersky Security Center. On this tab, you can track the usage of the manually created incidents for the current period (for example, for the current week):
- The total number incidents that you can create for the current period. These incidents are to be processed by the security team, according to the SLA. You can create more incidents than specified in the MDR Agreement, but compliance with the SLA time frames is not guaranteed for processing of such incidents.
- The remaining number of incidents that you can create for the current period.
To add a new incident:
- In the MDR Web Console window, navigate to the Incidents menu item.
The incident list opens.
- In the upper part of the window, click the Add button.
The new incident block appears.
- Fill in the following fields:
- If necessary, fill in the Tenant field.
For the Tenant field, tenants that already exist in Console and the Root without tenants value are suggested.
- Click the Send button.
The new incident block disappears.
The new incident is added to the incident list in MDR Web Console. You can view detailed information about this incident and the processing responses to it.
Page top
Viewing detailed information about incidents in MDR Web Console
To view detailed information about incidents:
- In the MDR Web Console window, navigate to the Incidents menu item.
The incident list opens.
- Click the string with the incident whose details you want to view.
The incident page opens.
The page title contains an incident identifier. Below the title there are four tabs:
- Summary
Contains general information on the incident.
- Responses
Contains information on responses to the incident.
- Communication
Contains information on communication and files related to the incident.
- History
Contains information on the incident changes.
General information on the Summary tab starts with a brief incident summary. Additional information listed in this section includes:
- Incident priority
- Incident status
- Incident resolution
- Timestamps of the incident create time and update time
- MITRE Tactics
- MITRE Techniques
- Detection technology
Below the incident summary, the following information is listed:
- Affected assets
- Asset-based IOCs
- Network-based IOCs
General information on the Summary tab concludes with a client description and a Close incident button.
- Summary
- If you know that the incident is a duplicate or you are not going to solve it, click the Close incident button.
- Refer to the Responses tab to view information on response requests.
The information on the Responses tab is presented as a list. The columns of the list are:
- Status
- Asset ID
- Type
- Details
- Comment
- Changed by
- Update time
- If you want to add a comment to an incident:
- On the Communication tab of the incident details page, type your comment in the text field.
Markdown and attaching files are supported. The maximum file size is 10 MB.
- Click the Send button.
The comment is added to the Communication tab on the incident details page. You can edit or delete your comment within 10 minutes after you post it.
- On the Communication tab of the incident details page, type your comment in the text field.
- Refer to the History tab to view information on the incident changes.
Below the title there is a switch for showing changes related to:
- All events
- Only incidents
- Only responses
- Only communication
Next to this switch, there are the following buttons:
- The Columns button with a gear icon, to select which columns to show on the History tab.
- The Filter button with a funnel icon, to show changes related only to the selected check boxes.
- The Search button with loupe icon, to show changes related only to the entered words or characters.
Response types
MDR SOC analysts examine incidents and create responses that you can either accept or reject. This is the default way of how incidents are handled in Kaspersky Managed Detection and Response.
However, you can manually create responses by using the Kaspersky Endpoint Detection and Response Optimum features.
This article only describes the types of SOC analyst responses.
Each response can have a set of parameters that are present on the Responses tab of an incident.
The available response types are:
- Get file
- Isolate
- Disable isolation
- Delete registry key
- Memory dump
- Terminate process
- Run script
- Put file in quarantine
- Restore file from quarantine
Processing responses to incidents in MDR Web Console
You can view, accept, and reject responses to incidents.
To view responses to an incident:
- In the MDR Web Console window, navigate to the Incidents menu item.
The incident list opens.
- Click the string with the incident whose details you want to view.
The incident page opens.
- On the incident page, click the Responses tab.
The response list opens.
Each line represents one response. The following information about the response is displayed:
- Status
Status of the response.
- Asset ID
Identifier of the asset for the response to be executed.
- Type
Type of the object that makes up the response.
- Parameters
OS-specific local path to get the response file and expected file size in MB. The maximum file size is 10 MB.
- Comment
Last comment to the response.
- Changed by
Last user who modified the response description.
- Status
To view the response description, click on the string with the response.
To accept or reject responses to an incident:
- In the Console window, navigate to the Incidents menu item.
The incident list opens.
- Click the string with the incident whose details you want to view.
The incident page opens.
- On the incident page, click the Responses tab.
The response list opens.
- Select a response that you want to approve or reject by selecting the check box at the left end of the string that contains response.
You can also select several responses by selecting their check boxes at the left. To select all responses, select the check box at the left part of response table heading.
- To approve or reject a response or responses, select either the Accept or Reject button located below the response list. The comment box appears. Enter your comment, and then click the Send button.
You can also click a response on the Responses tab to check its details and either accept or reject it in the side pane that appears. To reject the response, you have to enter your comment in the field on the side pane.
The response status is changed.
Page top
Auto-accepting responses in MDR Web Console
You can enable auto-acceptance of the offered responses. In this case, the actions offered within responses, for example, deleting an infected file, will be performed automatically. When this feature is disabled, the measures offered within responses need to be accepted or rejected manually.
If you use tenants, you can enable the auto-acceptance of responses for all tenants or only for the tenants that you select. If you do not use tenants, you enable or disable this feature for your current organization.
To enable auto-acceptance of responses:
- In the MDR Web Console window, navigate to the Settings menu item.
- Click the Incidents tab.
- Select one of the following options:
- Enabled for all tenants
When this option is selected, the auto-acceptance of responses is enabled both for the existing and newly created tenants.
- Enabled for the tenants selected below
Select the tenants for which you want to enable the auto-acceptance of responses. For newly created tenants, the auto-acceptance of responses is disabled by default.
- Enabled for all tenants
- Click the Save button.
Auto-acceptance of responses is enabled and the actions offered within responses will be performed automatically for all tenants or the tenants that you selected. You can disable this option at any time.
Access rights to view or change the auto-acceptance settings
The user roles of Kaspersky Managed Detection and Response have the following access rights to the auto-acceptance settings:
Operation |
MDR Administrator |
Senior Security Officer |
Security Officer |
|---|---|---|---|
Access the Incidents tab |
|
|
|
Change the currently selected option |
|
|
|
View the currently selected option |
|
|
|
Enable auto-acceptance for all tenants |
|
|
|
Enable auto-acceptance for specific tenants |
|
(only for the tenants the user has access to) |
|
View the auto-acceptance setting of a specific tenant |
|
(only for the tenants the user has access to) |
|
Auto-accepting responses in Kaspersky Security Center
You can enable auto-acceptance of the offered responses. In this case, the response actions offered within responses, for example, deleting an infected file, will be performed automatically. When this feature is disabled, the measures offered within responses need to be accepted or rejected manually.
If you use tenants, you can enable the auto-acceptance of responses for all tenants or only for the tenants that you select. If you do not use tenants, you enable or disable this feature for your current organization.
You can change the auto-acceptance settings if you have the MDR Administrator user role. Users with the Security Officer role are not allowed to change the settings. Users with the Senior Security Officer role are allowed to perform the following operations:
- View the currently selected option
- Enable or disable the auto-acceptance of responses for specific tenants if the Allow changing the response auto-acceptance option for each tenant option is selected
To configure auto-acceptance of responses:
- In the MDR section of Kaspersky Security Center, click the Settings tab.
- In the Auto-acceptance of responses group of parameters, select the required option:
- Disable auto-acceptance of responses for all tenants
Select this option, if you want to accept or reject response actions manually.
- Allow changing the response auto-acceptance option for all tenants
Select this option, if you want to enable the auto-acceptance of responses for all the tenants in your organization, including the existing and newly created tenants.
- Allow changing the response auto-acceptance option for each tenant
Select this option, if you want to configure the auto-acceptance of responses for each tenant individually. Then, select the check boxes for those tenants for which you want the response actions to be performed automatically. For newly created tenants, the auto-acceptance of responses is disabled by default.
If you select the All tenants option, the auto-acceptance of responses is enabled for the newly created tenants by default.
- Disable auto-acceptance of responses for all tenants
- Click the Save button.
The Save button becomes active only if you changed the settings.
Closing incidents in MDR Web Console
You can close an incident if you know that it is a duplicate or you are not going to solve it. In other cases, you must not close incidents, as they need to be solved by MDR SOC analysts. MDR SOC analysts resolve an incident if the measures that they recommended within this incident are applied. A resolved incident automatically closes after 72 hours.
To close an incident:
- In MDR Web Console, navigate to the Incidents menu item.
The incident list opens.
- Click the string with the incident whose details you want to view.
The incident page opens.
- On the Summary tab of the page, click the Close incident button in the lower part of the window.
There is no Close incident button for incidents with the Closed status.
The Close incident block appears.
- In the Reason why you are closing this incident field, specify any additional information that you want to communicate to Kaspersky Managed Detection and Response SOC analysts. For example, you can give details why you consider this incident to be a standard, non-threatening situation for your infrastructure. You can leave this field empty.
- Below the comment field, select the True positive or False positive option, depending on the closure reason.
Select the True positive option if Kaspersky Managed Detection and Response detected a threat, but you do not want MDR SOC analysts to investigate and solve the incident.
Select the False positive option if Kaspersky Managed Detection and Response detected a non-threatening activity as a threat. Kaspersky Managed Detection and Response uses this information for improving the automated detection algorithms.
- In the lower part of the block, click the Close button.
The Close incident block disappears.
The incident is closed. From now on, Kaspersky Managed Detection and Response will perform no actions in relation to this incident.
Page top
Using Kaspersky Endpoint Detection and Response Optimum features
The Kaspersky Endpoint Detection and Response Optimum solution provides the following response features (hereupon also referred to as EDR responses), which you can run and configure manually.
- Network isolation
- Move file to Quarantine
- Send files to Cloud Sandbox
- Delete file
- Run Critical Areas Scan
- IOC Scan
- Execution prevention
- Start a process
- Terminate process
- Get file
You can find more details about these EDR responses in Kaspersky Endpoint Detection and Response Optimum Online Help.
The EDR responses described in this section are available for assets with Kaspersky Endpoint Security for Windows 11.7 or later. If you use Kaspersky Endpoint Security for Windows 11.6 or an earlier version on your assets, Kaspersky Endpoint Agent must be installed on these assets in order to work with EDR responses.
To activate Kaspersky Endpoint Detection and Response Optimum functions, you must add one of the following activation codes on your assets via Kaspersky Security Center:
- Kaspersky Endpoint Detection and Response Optimum
- Kaspersky Endpoint Detection and Response Optimum add-on
To manage EDR alert responses actions, in Kaspersky Security Center go to the Monitoring & Reporting → Alerts section.
.
Multitenancy
Multitenancy is a mechanism allowing you to become a Kaspersky Managed Detection and Response supplier for other organizations. Once you have an MDR account, you can create
in your MDR account.Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
If your organization has multiple licenses, you can only manage tenants in Kaspersky Security Center.
To become an MDR supplier, you must have access to your tenant's infrastructure to be able to perform deployment scenarios.
All tenants are independent and isolated, which means no data from one tenant can be accessed by other tenants.
Only users with the MDR Administrator role assigned can add, edit, and delete tenants in MDR Web Console.
You can create up to 100 tenants in your MDR account. Each tenant has the following settings:
Managing tenants in Kaspersky Security Center
This section provides information about managing existing tenants and adding new tenants in Kaspersky Security Center.
Viewing tenants in Kaspersky Security Center
You can view available tenants by using the tenants list.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To view tenants:
- In the MDR section of Kaspersky Security Center, click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- The following tenant attributes are present above the list:
You can also view tenants in MDR Web Console.
Page top
Viewing tenant settings in Kaspersky Security Center
You can view the settings of every tenant in your account.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To view tenant settings:
- In the MDR section of Kaspersky Security Center, click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- Click the line with the tenant whose details you want to view.
The Tenant settings block appears.
The setting starts with the Active toggle button showing whether a tenant is active or not. If necessary, you can switch the Active toggle button. Below, the following fields are present:
- In the lower part of the Tenant settings block, click the Close button to close the block.
You can also view tenant settings in MDR Web Console.
Editing tenant settings in Kaspersky Security Center
You can edit the settings of every tenant in your account.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To edit tenant settings:
- In the MDR section of Kaspersky Security Center, click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- Click the line with the tenant whose details you want to edit.
The Tenant settings block appears. Here you can perform the following actions:
- Activating or deactivating the tenant by switching the Active toggle button.
- Changing the value of the Description field.
- Deleting a configuration file by clicking the X button. You can only delete a configuration file if another configuration file is added to the tenant.
- Adding a new configuration file by clicking the Add button. Specify the license and the expiration date.
- In the lower part of the Tenant settings block, click the Save button.
- The Tenant settings block disappears. After clicking the Save button, Kaspersky Managed Detection and Response generates the new MDR configuration file that complies with the updated tenant settings. You can click the Download the configuration file link to download the ZIP archive that contains the MDR configuration file.
The tenant settings are edited. The updated settings are applied to the assets of the selected administration groups.
You can also edit tenant settings in MDR Web Console.
Page top
Adding new tenants in Kaspersky Security Center
If you want to become a Kaspersky Managed Detection and Response supplier for another organization, you need to add a new tenant to your account.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To add a new tenant:
- In the MDR section of Kaspersky Security Center, click the Tenants tab.
The Tenants list appears.
- In the upper part of the window, click the plus sign icon (
 ).
).The Tenant settings block appears.
- If necessary, switch the Active toggle button.
The Active toggle button is on by default.
- Fill in the following fields:
- In the lower part of the Tenant settings block, click the Save button.
The Tenant settings block disappears. After clicking the Save button, Kaspersky Managed Detection and Response generates an MDR configuration file for the new tenant. You can click the Download the configuration file link to download the ZIP archive that contains the MDR configuration file.
The new tenant is added.
You can also add new tenants in MDR Web Console.
Deleting tenants in Kaspersky Security Center
When you delete a tenant that contains some assets, all its assets are disconnected from MDR solution. To continue managing tenant's assets, you can move them to the root tenant or a new tenant before deleting the tenant.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To delete a tenant:
- In the MDR section of Kaspersky Security Center, click the Tenants tab.
The Tenants list appears.
- In the Tenants list, point to the tenant that you want to delete, and then click the trash can icon (
 ) on the right side of the line.
) on the right side of the line. - Confirm the deletion.
The selected tenant is deleted.
You can also delete tenants in MDR Web Console.
Page top
Moving assets between tenants
When you delete a tenant that contains some assets, all its assets stop sending telemetry to MDR solution. Before deleting a tenant, move all its assets to the root tenant or a new tenant.
Your account in Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console must have a role with the following access rights: Incident access and Tenant management, and the ability to view, add, edit, and delete tenants in the MDR section in Kaspersky Security Center.
To move assets to a new tenant:
- In the MDR section of Kaspersky Security Center, create a new tenant. Later, you will add assets to this tenant.
When you create a new tenant, you download an MDR configuration file.
- In Kaspersky Security Center Web Console, create a new administration group.
- Add the assets that you want to move to the new tenant to the new administration group.
- Create a new policy for Kaspersky Endpoint Agent or an EPP application for the created administration group.
- Apply the MDR configuration file to the created policy.
For details on different deployment scenarios, refer to Deployment of Kaspersky Managed Detection and Response.
After the policy is applied to the assets of the administration group, the assets are moved from the root tenant to the newly created tenant.
To move assets to the root tenant:
- Download an MDR configuration file for root tenant:
- In MDR Web Console (https://mdr.kaspersky.com/guide), go to Getting started page and click the MDR configuration file (BLOB file included) or MDR configuration file (BAT file included) link.
- In your Kaspersky Security Center Web Console or Kaspersky Security Center Cloud Console, go to MDR > Getting Started and click the Download link.
- In Kaspersky Security Center Web Console, create a new administration group.
- Add the assets that you want to move to the new tenant to the new administration group.
- Create a new policy for Kaspersky Endpoint Agent or an EPP application for the created administration group.
- Apply the MDR configuration file to the created policy.
After the policy is applied to the assets of the administration group, the assets are moved from the default tenant to the newly created tenant.
Page top
Managing tenants in MDR Web Console
This section provides information about managing tenants in MDR Web Console.
Viewing tenants in MDR Web Console
To view tenants:
- In the MDR Web Console window, navigate to the Settings menu item.
- Click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- The following tenant attributes are present above the list:
Viewing tenant settings in MDR Web Console
To view tenant settings:
- In MDR Web Console, navigate to the Settings menu item.
- Click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- Click the line with the tenant whose details you want to view.
The Tenant settings block appears.
The setting starts with the Active toggle button showing whether a tenant is active or not. If necessary, you can switch the Active toggle button. Below, the following fields are present:
- In the lower part of the Tenant settings block, click the Cancel button to close the block.
Editing tenant settings in MDR Web Console
The ability to add, edit, and delete tenants is available only for the user who has the MDR Administrator role assigned.
To edit tenant settings:
- Open MDR Console.
- In the Settings section of MDR Console, click the Tenants tab.
The Tenants list appears. Each line represents one tenant. You can click anywhere on the line to view tenant information.
- Click the line with the tenant whose details you want to edit.
The Tenant settings block appears.
- If necessary, switch the Active toggle button.
- If necessary, change the values of the fields.
- In the lower part of the Tenant settings block, click the Save button.
The Tenant settings block disappears. After clicking the Save button, Kaspersky Managed Detection and Response generates a new MDR configuration file that complies with the updated tenant settings.
- In the Tenants list, click the line with the edited tenant.
The Tenant settings block appears. In the lower part of the block, there are two buttons for downloading the MDR configuration file for the tenant deployment:
- File for assets with KEA
The file to use in deployment for Kaspersky programs with Kaspersky Endpoint Agent.
- File for assets without KEA
The file to use in deployment for Kaspersky Endpoint Security without Kaspersky Endpoint Agent.
- File for assets with KEA
- Click the File for assets with KEA or File for assets without KEA button to download the new MDR configuration file.
- In the lower part of the Tenant settings block, click the Cancel button to close the block.
The tenant settings are edited. Now, you need to deploy the new MDR configuration file on the tenant's assets to apply the edited settings.
Page top
Adding new tenants in MDR Web Console
The ability to add, edit, and delete tenants is available only for the user who has the MDR Administrator role assigned.
To add a new tenant:
- In the MDR Web Console window, navigate to the Settings menu item.
- Click the Tenants tab.
The Tenants list appears.
- In the upper part of the window, click the Add button.
The Tenant settings block appears.
- If necessary, switch the Active toggle button.
The Active toggle button is on by default.
- Fill in the following fields:
- In the lower part of the Tenant settings block, click the Save button.
The Tenant settings block disappears. After clicking the Save button, Kaspersky Managed Detection and Response generates an MDR configuration file for the new tenant.
- In the Tenants list, click the line with the new tenant.
The Tenant settings block appears. In this block you can download the MDR configuration file for the tenant deployment:
- Click the File for assets with KEA or File for assets without KEA button to download the new MDR configuration file.
- In the lower part of the Tenant settings block, click the Cancel button to close the block.
The new tenant is added. Now, you can deploy the downloaded MDR configuration file on the tenant's assets.
Please note that the tenants created in MDR Console are not available in the MDR section of Kaspersky Security Center. Please use MDR Web Console to work with these tenants.
Page top
Deleting tenants in MDR Web Console
When you delete a tenant that contains some assets, all its assets are disconnected from MDR solution. Before deleting a tenant, move all its assets to the root tenant or a new tenant.
The ability to add, edit, and delete tenants is available only for the user who has the MDR Administrator role assigned.
To delete a tenant:
- In MDR Web Console, navigate to the Settings menu item.
- Click the Tenants tab.
The Tenants list appears.
- In the tenants list, hover the mouse pointer over the tenant you want to delete, and click the Delete tenant button with trash bin icon on the right.
The Confirm tenant deletion windows appears.
- Click the Delete button to delete the tenant.
Please note that the tenants created in MDR Console are not available in the MDR section of Kaspersky Security Center. Please use MDR Web Console to work with these tenants.
Managing the solution through the REST API
This feature is available in MDR Expert, MDR Advanced, (available in some regions only), and MDR Prime (available in some regions only). See the comparison of license solutions in this section.
To have access to the REST API in Kaspersky Security Center, your account in Kaspersky Security Center Web Console needs to have the following access rights: Incident access and REST API access.
For some commercial license tiers it will only be possible to generate a refresh token in MDR Web Console to use it for setting up MDR Plug-in, without access to the REST API in Kaspersky Security Center.
Kaspersky Managed Detection and Response allows you to programmatically get, create, and update MDR entities via the REST API. The REST API operates over HTTP and consists of a set of request/response methods. In other words, you can manage Kaspersky Managed Detection and Response through a third-party solution, not MDR Web Console.
To start working with the REST API, you need to create a refresh token and an access token.
Scenario: performing token-based authorization
This scenario explains how to perform a token-based authorization in order to work with the REST API.
Prerequisites
Make sure that you have an MDR account with one of the following roles assigned:
- The MDR Administrator role
- A custom role with the following access rights (applicable only for Kaspersky Security Center):
- Incident Access
- REST API access
Stages
The token-based authorization proceeds in stages:
- Creating a refresh token in MDR Web Console
You need a refresh token for creating an access token. A refresh token is valid for 24 hours. You can use a refresh token only once.
- Creating an access token via the REST API
You need an access token to work with the REST API. An access token is valid for 1 hour. You can use an access token multiple times during its lifetime.
When you create an access token, the REST API generates a new refresh token and includes it in the response. When the access token expires, you can create a new access token by using the most recent API-generated refresh token.
An API-generated refresh token is valid for 7 days.
Results
Upon completion of this scenario, you can start working with the REST API by sending requests with the access token.
Creating an API connection in Kaspersky Security Center
When you create a new API connection, a refresh token is generated. A refresh token is a unique sequence of letters, digits, and symbols. Once created, a refresh token allows you to create an access token.
To create an API connection:
- In the MDR section of Kaspersky Security Center, click the API tab.
The API connections list appears.
- In the upper part of the window, click the plus sign icon (
 ).
).The Add a new API connection block appears.
- Specify the following settings:
- Connection name
A connection name can contain Latin letters, digits, and special characters. A connection name is specified as
author_namein REST API responses and displayed as the comment author on the Communication tab of an incident. - Access rights
Select which access rights to grant for performing actions via the HTTP API:
- Tenant
If necessary, select the value (or values) in the Tenant drop-down list.
The user can view only the assets and incidents related to the specified tenants.
- Connection name
- Click the Generate button.
The JWT token field appears.
- Click the Close button.
The new API connection appears in the API connections list. Now, you can use the refresh token to create an access token.
You can also create API connections in MDR Web Console.
Creating an API connection in MDR Web Console
A refresh token is a unique sequence of letters, digits, and symbols. Once created, a refresh token allows you to create an access token.
To create a refresh token:
- In the MDR Web Console window, navigate to the Settings menu item.
- Click the API tab.
The All tokens list appears.
- In the upper part of the window, click the Add button.
The Generate token block appears.
- Specify the following settings:
- Connection name
The name of a token.
The name of a token can contain Latin letters, digits, and special characters. The name of a token is specified as
author_namein REST API responses and displayed as the comment author on the Communication tab of an incident.For some commercial license tiers, this is the only available field while creating a refresh token.
- User role
The user role to specify permissions that will be granted for performing actions via the HTTP API.
The following user roles are available:
- Tenant
If necessary, select the value (or values) in the Tenant drop-down list.
The tenants already existing in Console and the Root without tenants value are suggested.
The user can view only the assets and incidents related to the specified tenants. If you have assets and incidents not assigned to any tenants, the user can view them if you select the Root without tenants value.
You can select the Root without tenants value, in addition to specifying tenant names.
- Connection name
- In the lower part of the block, click the Generate button.
The Token info block replaces the Generate token block.
- Click the Close button in the lower part of the Token info block.
The refresh token that you have created appears in the All tokens list. Now, you can use this refresh token to create an access token.
Editing an API connection in Kaspersky Security Center
You can edit existing API connections.
To edit an API connection:
- In the MDR section of Kaspersky Security Center, click the API tab.
The API connections list appears.
- Click the API connection that you want to edit.
A block containing the connection information appears.
- Change the connection settings.
- Click the Save button.
The new settings of the selected API connection are saved.
Page top
Editing an API connection in MDR Web Console
You can edit existing API connections.
To edit an API connection:
- In MDR Web Console, click the API tab.
The All tokens list appears.
- Click the token of the API connection that you want to edit.
A block containing the connection information appears.
- Change the connection settings.
- Click the Save button.
The new settings of the selected API connection are saved.
Page top
Creating an access token in Kaspersky Security Center
An access token is a unique sequence of characters (letters, digits, and special characters) that authorizes you to use the methods of the REST API.
To create an access token:
- In the MDR section of Kaspersky Security Center, click the API tab.
The API connections list appears.
- Click a connection with a Pending activation status.
A block containing the connection information appears.
- In the JWT token field, click the Refresh button.
A refresh token appears.
- Select and save the value from the Client ID field.
- Select and save the token's sequence of characters to the clipboard.
- Send a POST request to the
/session/confirmendpoint.Replace
{client_id}and{refresh_token}with the values selected and saved in the previous steps.
Example (Python): ###################################################
# General part
###################################################
import time
import datetime
import requests
import jwt
# The certificate is required for authentication of an external resource
# You can download the certificate from https://mdr.kaspersky.com,
# save it to your disk, and add the path to it in the variable:
VERIFY_CERT_PATH = "C:\\tools\\DigiCert Global Root G2.crt"
# MDR REST API URL:
API_URL = "https://mdr.kaspersky.com/api/v1"
# Your client's ID and your tokens.
# For details about getting your ID and the tokens, refer to the help https://support.kaspersky.com/MDR/en-US/258285.htm
CLIENT_ID = "9ed43ed54sAmpleIdf349323951f" # (Paste your value)
REFRESH_TOKEN = "ReFrEsHToKeN" # (Paste your value)
ACCESS_TOKEN = "AcCeSsToKeN" # (Paste your value)
###################################################
# Get access token and a refresh token for the next access token update
###################################################
if REFRESH_TOKEN:
refresh_token_exp = jwt.decode(REFRESH_TOKEN, options={"verify_signature": False}).get("exp")
print(f"REFRESH_TOKEN expiration date and time: {datetime.datetime.fromtimestamp(refresh_token_exp)}")
if refresh_token_exp > time.time():
print("REFRESH_TOKEN is actual")
else:
print(
"You should update REFRESH_TOKEN. Please take it from MDR Console (https://support.kaspersky.com/MDR/en-US/258285.htm)."
)
exit()
else:
print(
"You should fill REFRESH_TOKEN value. Please take it from MDR Console (https://support.kaspersky.com/MDR/en-US/258285.htm)."
)
exit()
# Check the presence and validity of the access token
need_update_access_token = False
if ACCESS_TOKEN:
access_token_exp = jwt.decode(ACCESS_TOKEN, options={"verify_signature": False}).get("exp")
print(f"ACCESS_TOKEN expiration date and time: {datetime.datetime.fromtimestamp(access_token_exp)}")
if access_token_exp > time.time():
print("ACCESS_TOKEN is actual")
else:
need_update_access_token = True
else:
need_update_access_token = True
# If necessary, update the access token and refresh token for the next access token update
access_token = ACCESS_TOKEN
if need_update_access_token:
request_body = {"refresh_token": REFRESH_TOKEN}
result = requests.post(url=f"{API_URL}/{CLIENT_ID}/session/confirm", json=request_body, verify=VERIFY_CERT_PATH)
result_json = result.json()
if "error" in result_json:
print(result_json)
exit()
# It is necessary to save the refresh token in order to obtain next access token after the expiration of the current access token
refresh_token = result_json["refresh_token"]
print(
f'!!! Your new REFRESH_TOKEN for the next time for request ACCESS_TOKEN (please replace value of REFRESH_TOKEN with this value): "{refresh_token}"'
)
# A new access token is required to retrieve the data
access_token = result_json["access_token"]
print(f'!!! Your new ACCESS_TOKEN (please replace value of ACCESS_TOKEN with this value): "{access_token}"')
# The access token is added to the request header
headers = {"Authorization": f"Bearer {access_token}"}
|
Example (Shell): curl -X POST https://mdr.kaspersky.com/api/v1/{client_id}/session/confirm -H "Content-Type: application/json" -d '{"refresh_token": "{refresh_token}"}'
|
The REST API sends a response with the access token and a new refresh token:
Now, you can send requests to the REST API by using the access token. Each request to the REST API requires an access token; a request without an access token will return an authorization error only.
You can also create an access token in MDR Web Console.
Creating an access token in MDR Web Console
To create an access token:
- In the MDR Web Console window, navigate to the Settings menu item.
- Click the API tab.
The All tokens list appears. Each line represents one token. You can click anywhere on the line to view token information.
- Click a token with a Pending activation status.
A Token info block appears.
- In the JWT token field, click the Refresh button.
A refresh token appears.
- Select and save the value from the Client ID field.
- Select and save the token's sequence of characters to the clipboard.
- Send a POST request to the
/session/confirmendpoint (see the examples below).Replace
{client_id}and{refresh_token}with the values selected and saved in the previous steps.
Example (Python): ###################################################
# General part
###################################################
import time
import datetime
import requests
import jwt
# The certificate is required for authentication of an external resource
# You can download the certificate from https://mdr.kaspersky.com,
# save it to your disk, and add the path to it in the variable:
VERIFY_CERT_PATH = "C:\\tools\\DigiCert Global Root G2.crt"
# MDR REST API URL:
API_URL = "https://mdr.kaspersky.com/api/v1"
# Your client's ID and your tokens.
# For details about getting your ID and the tokens, refer to the help https://support.kaspersky.com/MDR/en-US/258285.htm
CLIENT_ID = "9ed43ed54sAmpleIdf349323951f" # (Paste your value)
REFRESH_TOKEN = "ReFrEsHToKeN" # (Paste your value)
ACCESS_TOKEN = "AcCeSsToKeN" # (Paste your value)
###################################################
# Get access token and a refresh token for the next access token update
###################################################
if REFRESH_TOKEN:
refresh_token_exp = jwt.decode(REFRESH_TOKEN, options={"verify_signature": False}).get("exp")
print(f"REFRESH_TOKEN expiration date and time: {datetime.datetime.fromtimestamp(refresh_token_exp)}")
if refresh_token_exp > time.time():
print("REFRESH_TOKEN is actual")
else:
print(
"You should update REFRESH_TOKEN. Please take it from MDR Console (https://support.kaspersky.com/MDR/en-US/258285.htm)."
)
exit()
else:
print(
"You should fill REFRESH_TOKEN value. Please take it from MDR Console (https://support.kaspersky.com/MDR/en-US/258285.htm)."
)
exit()
# Check the presence and validity of the access token
need_update_access_token = False
if ACCESS_TOKEN:
access_token_exp = jwt.decode(ACCESS_TOKEN, options={"verify_signature": False}).get("exp")
print(f"ACCESS_TOKEN expiration date and time: {datetime.datetime.fromtimestamp(access_token_exp)}")
if access_token_exp > time.time():
print("ACCESS_TOKEN is actual")
else:
need_update_access_token = True
else:
need_update_access_token = True
# If necessary, update the access token and refresh token for the next access token update
access_token = ACCESS_TOKEN
if need_update_access_token:
request_body = {"refresh_token": REFRESH_TOKEN}
result = requests.post(url=f"{API_URL}/{CLIENT_ID}/session/confirm", json=request_body, verify=VERIFY_CERT_PATH)
result_json = result.json()
if "error" in result_json:
print(result_json)
exit()
# It is necessary to save the refresh token in order to obtain next access token after the expiration of the current access token
refresh_token = result_json["refresh_token"]
print(
f'!!! Your new REFRESH_TOKEN for the next time for request ACCESS_TOKEN (please replace value of REFRESH_TOKEN with this value): "{refresh_token}"'
)
# A new access token is required to retrieve the data
access_token = result_json["access_token"]
print(f'!!! Your new ACCESS_TOKEN (please replace value of ACCESS_TOKEN with this value): "{access_token}"')
# The access token is added to the request header
headers = {"Authorization": f"Bearer {access_token}"}
|
Example (Shell): curl -X POST https://mdr.kaspersky.com/api/v1/{client_id}/session/confirm -H "Content-Type: application/json" -d '{"refresh_token": "{refresh_token}"}'
|
The REST API sends a response with the access token and a new refresh token:
Now, you can send requests to the REST API by using the access token. Each request to the REST API requires an access token; a request without an access token will return an authorization error only.
Working with the REST API
Working with MDR through the REST API includes getting, creating, and updating assets, incidents, responses, and users.
The REST API methods require client_id value. You can get your client_id value in the Token info block of any refresh token in MDR Web Console.
Following are examples of script for Python and Shell that demonstrate core REST API capabilities:
- Define the certificate path, REST API URL, client ID, and the tokens
- Get access token and refresh token for the next access token update
- Get the number of asset
- Get the list of assets or asset details
- Get the number of incidents, the list of the incidents, or the incident details
- Get the list of responses for the incident
- Confirm, decline the response, or update the response list
- Get the list of comments for the specified incident, or create a new comment for the specified incident
Example (Python):
|
Example (Shell):
|
REST API reply example with the access token and new refresh token:
{
"access_token": "SamPLET346yoKEnSamPLEToK25EnSamPLEToK35EnS",
"refresh_token": "tOKenSaMPlet259OKenS123aMPle926tOKenSaMPle"
}
REST API reply example with the structure and values of comments:
[{
"comment_id": "bfu6TiNghqp",
"author_name": "John Doe",
"text": "<p>The first comment.</p>",
"creation_time": 1601295428640
}, {
"comment_id": "bfu6TiNghqt",
"author_name": "Jane Doe",
"text": "<p>The second comment.</p>",
"creation_time": 1601295433441
}]
REST API reply example when REST API creates a new comment and sends a response with the comment details:
{
"comment_id": "AXTej0Qi4bfu6TiNgmvT",
"author_name": "Token name",
"text": "This is a new comment created via the REST API.",
"creation_time": 1601461748122
}
Revoking a refresh token in Kaspersky Security Center
You can revoke refresh tokens from API connections that currently have the Active or Idle status.
To revoke a refresh token:
- In the MDR section of Kaspersky Security Center, click the API tab.
The API connections list appears.
- Click the API connection from which you want to revoke a refresh token.
A block containing the connection information appears.
- Click the Revoke button.
The refresh token is revoked.
Page top
Deleting an API connection in Kaspersky Security Center
You can delete existing API connections.
To delete an API connection:
- In the MDR section of Kaspersky Security Center, click the API tab.
The API connections list appears.
- Point to the API connection that you want to delete, and then click the trash can icon (
 ) on the right side of the line.
) on the right side of the line.
The selected API connection is deleted.
Page top
Deleting an API connection in MDR Web Console
You can edit existing API connections.
To edit an API connection:
- In MDR Web Console, click the API tab.
The All tokens list appears.
- Point to the API connection that you want to delete, and then click the trash can icon (
 ) on the right side of the line.
) on the right side of the line.
The selected API connection is deleted.
Page top
Known issues
Kaspersky Managed Detection and Response has a number of limitations that are not critical to operation of the application:
- If you clone a virtual or physical asset with Kaspersky Endpoint Security for Linux that is already connected to the MDR solution, telemetry data from the cloned assets is not transmitted correctly. For these cloned assets, remove Kaspersky Endpoint Security for Linux, delete install_id file in /var/opt/kaspersky/epagent/ folder, and then reinstall Kaspersky Endpoint Security for Linux.
- For assets with the Kaspersky Endpoint Security for Windows in the Endpoint Detection and Response Agent (EDR Agent) configuration, the Warning and Critical statuses for protection and control components are not displayed.
- You can not use Kaspersky Endpoint Detection and Response Optimum features for the assets with Kaspersky Endpoint Security for Windows in EDR Agent configuration.
- The Kaspersky applications that work with MDR section of the asset card in MDR Web Console can contain outdated Endpoint Protection Platform (EPP) applications, that are no longer used to work with Kaspersky Managed Detection and Response. It occurs when an outdated EPP application was replaced with a new one on the asset. For these outdated applications, the Last seen field contains the old date, while for the new EPP application, the Last seen field contains the newer date.
Contact Technical Support
This section describes how to get technical support and the terms on which it is available.
How to get technical support
If you can't find a solution to your issue in the Kaspersky Managed Detection and Response documentation or in any of the sources of information about Kaspersky Managed Detection and Response, contact Kaspersky Customer Service. Technical Support specialists will answer all your questions about installing and using Kaspersky Managed Detection and Response.
Kaspersky provides support of Kaspersky Managed Detection and Response during its lifecycle (see the application support lifecycle page). Before contacting Technical Support, please read the support rules.
You can contact Technical Support in one of the following ways:
- By visiting the Technical Support website
- By sending a request to Technical Support from the Kaspersky CompanyAccount portal
Technical support via Kaspersky CompanyAccount
Kaspersky CompanyAccount is a portal for companies that use Kaspersky applications. The Kaspersky CompanyAccount portal is designed to facilitate interaction between users and Kaspersky specialists through online requests. You can use Kaspersky CompanyAccount to track the status of your online requests and store a history of them as well.
You can register all of your organization's employees under a single account on Kaspersky CompanyAccount. A single account lets you centrally manage electronic requests from registered employees to Kaspersky and also manage the privileges of these employees via Kaspersky CompanyAccount.
The Kaspersky CompanyAccount portal is available in the following languages:
- English
- Spanish
- Italian
- German
- Polish
- Portuguese
- Russian
- French
- Japanese
To learn more about Kaspersky CompanyAccount, visit the Technical Support website.
Page top
Sources of information about the solution
On the Kaspersky Managed Detection and Response page, you can view general information about the solution, its functions, and its features.
Page topGlossary
Asset
A device with an installed Kaspersky EPP application (for example, Kaspersky Endpoint Security for Windows).
Endpoint Protection Platform (EPP)
An integrated system of complex protection for endpoint devices (for example, mobile devices, computers, or laptops) that includes various security technologies. An example of an Endpoint Protection Platform is Kaspersky Endpoint Security for Business.
EPP application
An application included in a protection system for endpoint devices (Endpoint Protection Platform, or EPP). EPP applications are installed on endpoint devices within the IT infrastructure of an organization (for example, mobile devices, computers, or laptops). An example of an EPP application is Kaspersky Endpoint Security for Windows, as part of the EPP solution Kaspersky Endpoint Security for Business.
Incident
An activity evaluated as critical by the detection technology and which requires immediate reaction from Kaspersky Managed Detection and Response.
IOC
An indicator of compromise (or IOC) shows the evidence on a device that points to a security breach.
MITRE tactic
The objective that an attacker wanted to achieve during a cyber attack on the Client infrastructure.
MITRE technique
The method used by the attacker to perform malicious actions during a cyberattack on the Client infrastructure. Each MITRE tactic contains an array of MITRE techniques.
Response
Incident response is a structured methodology for handling security incidents, breaches, and cyberthreats.
Telemetry
Data that is sent from assets to Kaspersky Managed Detection and Response.
Tenant
A tenant is an organization to which you supply Kaspersky Managed Detection and Response.
Page top
Information about third-party code
Third-party code has been used in the development of the solution.
For information about third-party code in Kaspersky Managed Detection and Response Console, contact Kaspersky Managed Detection and Response Support.
Information about third-party code used in MDR Plug-in is contained in the file legal_notices.txt.
Page top
Trademark notices
Registered trademarks and service marks are the property of their respective owners.
Apple, Mac, macOS, and Safari are trademarks of Apple Inc.
Amazon AWS, Amazon Web Services are trademarks of Amazon.com, Inc. or its affiliates.
Active Directory, Internet Explorer, Microsoft, Microsoft Edge, Outlook, PowerShell, Windows PowerShell, Windows, and Windows Server are trademarks of the Microsoft group of companies.
Firefox and Mozilla are trademarks of the Mozilla Foundation in the U.S. and other countries.
Google and Google Chrome are trademarks of Google LLC.
Linux is the registered trademark of Linus Torvalds in the U.S. and other countries.
Python is a trademark or registered trademark of the Python Software Foundation.
Page top
Configuring audit settings for work with Kaspersky Managed Detection and Response
We recommend configuring the following audit settings to ensure stable operation and maximize efficiency of Kaspersky Managed Detection and Response:
Onboarding video
Watch the video to learn more about the main features of the MDR solution.
MDR Solution. Onboarding video
Page top
Onboarding video
Watch the video to learn more about the main features of the MDR solution.
MDR solution. Onboarding video
Page top