Kaspersky Endpoint Security for Windows 11.7.0
- Čeština (Česká republika)
- Deutsch
- Español (España)
- Español (México)
- Français
- Italiano
- Magyar (Magyarország)
- Nederlands (Nederland)
- Polski (Polska)
- Português (Brasil)
- Português (Portugal)
- Română (România)
- Tiếng Việt (Việt Nam)
- Türkçe (Türkiye)
- Русский
- العربية (الإمارات العربية المتحدة)
- 한국어 (대한민국)
- 简体中文
- 繁體中文
- 日本語(日本)
- Čeština (Česká republika)
- Deutsch
- Español (España)
- Español (México)
- Français
- Italiano
- Magyar (Magyarország)
- Nederlands (Nederland)
- Polski (Polska)
- Português (Brasil)
- Português (Portugal)
- Română (România)
- Tiếng Việt (Việt Nam)
- Türkçe (Türkiye)
- Русский
- العربية (الإمارات العربية المتحدة)
- 한국어 (대한민국)
- 简体中文
- 繁體中文
- 日本語(日本)
- Frequently asked questions
- What's new
- Kaspersky Endpoint Security for Windows
- Installing and removing the application
- Deployment through Kaspersky Security Center
- Installing the application locally using the Wizard
- Remotely installing the application using System Center Configuration Manager
- Description of setup.ini file installation settings
- Change application components
- Upgrading from a previous version of the application
- Remove the application
- Application licensing
- Data provision
- Getting started
- About the Kaspersky Endpoint Security for Windows Management Plug-in
- Special considerations when working with different versions of management plug-ins
- Special considerations when using encrypted protocols for interacting with external services
- Application interface
- Getting started
- Managing policies
- Task management
- Configuring local application settings
- Starting and stopping Kaspersky Endpoint Security
- Pausing and resuming computer protection and control
- Virus Scan of the computer
- Updating databases and application software modules
- Database and application module update scenarios
- Starting and stopping an update task
- Starting an update task under the rights of a different user account
- Selecting the update task run mode
- Adding an update source
- Configuring updates from a shared folder
- Updating application modules
- Using a proxy server for updates
- Last update rollback
- Working with active threats
- Computer protection
- File Threat Protection
- Enabling and disabling File Threat Protection
- Automatic pausing of File Threat Protection
- Changing the action taken on infected files by the File Threat Protection component
- Forming the protection scope of the File Threat Protection component
- Using scan methods
- Using scan technologies in the operation of the File Threat Protection component
- Optimizing file scanning
- Scanning compound files
- Changing the scan mode
- Web Threat Protection
- Enabling and disabling Web Threat Protection
- Changing the action to take on malicious web traffic objects
- Scanning URLs against databases of phishing and malicious web addresses
- Using heuristic analysis in the operation of the Web Threat Protection component
- Creating the list of trusted web addresses
- Exporting and importing the list of trusted web addresses
- Mail Threat Protection
- Enabling and disabling Mail Threat Protection
- Changing the action to take on infected email messages
- Forming the protection scope of the Mail Threat Protection component
- Scanning compound files attached to email messages
- Email messages attachment filtering
- Exporting and importing extensions for attachment filtering
- Scanning emails in Microsoft Office Outlook
- Network Threat Protection
- Firewall
- BadUSB Attack Prevention
- AMSI Protection
- Exploit Prevention
- Behavior Detection
- Enabling and disabling Behavior Detection
- Selecting the action to take on detecting malware activity
- Protection of shared folders against external encryption
- Enabling and disabling protection of shared folders against external encryption
- Selecting the action to take on detection of external encryption of shared folders
- Creating an exclusion for protection of shared folders against external encryption
- Configuring addresses of exclusions from protection of shared folders against external encryption
- Exporting and importing a list of exclusions from protection of shared folders against external encryption
- Host Intrusion Prevention
- Remediation Engine
- Kaspersky Security Network
- Encrypted connections scan
- File Threat Protection
- Computer control
- Web Control
- Enabling and disabling Web Control
- Actions with web resource access rules
- Exporting and importing the list of web resource addresses
- Monitoring user Internet activity
- Editing templates of Web Control messages
- Editing masks for web resource addresses
- Migrating web resource access rules from previous versions of the application
- Device Control
- Enabling and disabling Device Control
- About access rules
- Editing a device access rule
- Editing a connection bus access rule
- Adding a Wi-Fi network to the trusted list
- Monitoring usage of removable drives
- Changing the caching duration
- Actions with trusted devices
- Obtaining access to a blocked device
- Editing templates of Device Control messages
- Anti-Bridging
- Adaptive Anomaly Control
- Enabling and disabling Adaptive Anomaly Control
- Enabling and disabling an Adaptive Anomaly Control rule
- Modifying the action taken when an Adaptive Anomaly Control rule is triggered
- Creating an exclusion for an Adaptive Anomaly Control rule
- Exporting and importing exclusions for Adaptive Anomaly Control rules
- Applying updates for Adaptive Anomaly Control rules
- Editing Adaptive Anomaly Control message templates
- Viewing Adaptive Anomaly Control reports
- Application Control
- Application Control functionality limitations
- Enabling and disabling Application Control
- Selecting the Application Control mode
- Working with Application Control rules in the application interface
- Managing Application Control rules in Kaspersky Security Center
- Receiving information about the applications that are installed on users' computers
- Creating application categories
- Adding executable files from the Executable files folder to the application category
- Adding event-related executable files to the application category
- Adding and modifying an Application Control rule using Kaspersky Security Center
- Changing the status of an Application Control rule via Kaspersky Security Center
- Exporting and importing Application Control rules
- Testing Application Control rules using Kaspersky Security Center
- Viewing events resulting from test operation of the Application Control component
- Viewing a report on blocked applications in test mode
- Viewing events resulting from operation of the Application Control component
- Viewing a report on blocked applications
- Testing Application Control rules
- Application activity monitor
- Rules for creating name masks for files or folders
- Editing Application Control message templates
- Best practices for implementing a list of allowed applications
- Network ports monitoring
- Web Control
- Wipe Data
- Password protection
- Trusted zone
- Managing Backup
- Notification service
- Managing reports
- Kaspersky Endpoint Security Self-Defense
- Kaspersky Endpoint Security performance and compatibility with other applications
- Creating and using a configuration file
- Restoring the default application settings
- Messaging between users and the administrator
- Data Encryption
- Encryption functionality limitations
- Changing the length of the encryption key (AES56 / AES256)
- Kaspersky Disk Encryption
- Special features of SSD drive encryption
- Full disk encryption using Kaspersky Disk Encryption technology
- Creating a list of hard drives excluded from encryption
- Exporting and importing a list of hard drives excluded from encryption
- Enabling Single Sign-On (SSO) technology
- Managing Authentication Agent accounts
- Using a token and smart card with Authentication Agent
- Hard drive decryption
- Restoring access to a drive protected by Kaspersky Disk Encryption technology
- Updating the operating system
- Eliminating errors of encryption functionality update
- Selecting the Authentication Agent tracing level
- Editing Authentication Agent help texts
- Removing leftover objects and data after testing the operation of Authentication Agent
- BitLocker Management
- File Level Encryption on local computer drives
- Encrypting files on local computer drives
- Forming encrypted file access rules for applications
- Encrypting files that are created or modified by specific applications
- Generating a decryption rule
- Decrypting files on local computer drives
- Creating encrypted packages
- Restoring access to encrypted files
- Restoring access to encrypted data after operating system failure
- Editing templates of encrypted file access messages
- Encryption of removable drives
- Viewing data encryption details
- Working with encrypted devices when there is no access to them
- Detection and Response
- Managing the application from the command line
- Installing the application
- Activating the application
- Remove the application
- AVP commands
- SCAN. Virus Scan
- UPDATE. Updating databases and application software modules
- ROLLBACK. Last update rollback
- TRACES. Tracing
- START. Start the profile
- STOP. Stopping a profile
- STATUS. Profile status
- STATISTICS. Profile operation statistics
- RESTORE. Restoring files from Backup
- EXPORT. Exporting application settings
- IMPORT. Importing application settings
- ADDKEY. Applying a key file
- LICENSE. Licensing
- RENEW. Purchasing a license
- PBATESTRESET. Reset the disk check results before encrypting the disk
- EXIT. Exit the application
- EXITPOLICY. Disabling policy
- STARTPOLICY. Enabling policy
- DISABLE. Disabling protection
- SPYWARE. Spyware detection
- KSN. Global/Private KSN transition
- KESCLI commands
- Scan. Virus Scan
- GetScanState. Scan completion status
- GetLastScanTime. Determining the scan completion time
- GetThreats. Obtaining data on detected threats
- UpdateDefinitions. Updating databases and application software modules
- GetDefinitionState. Determining the update completion time
- EnableRTP. Enabling protection
- GetRealTimeProtectionState. File Threat Protection status
- Version. Identifying the application version
- Detection and Response management commands
- Error codes
- Appendix. Application profiles
- Managing the application through the REST API
- Sources of information about the application
- Contacting Technical Support
- Limitations and warnings
- Glossary
- Active key
- Additional key
- Administration group
- Anti-virus databases
- Archive
- Authentication Agent
- Certificate issuer
- Database of malicious web addresses
- Database of phishing web addresses
- Disinfection
- False alarm
- Infectable file
- Infected file
- IOC
- IOC file
- License certificate
- Mask
- Network Agent
- Normalized form of the address of a web resource
- OLE object
- OpenIOC
- Portable File Manager
- Protection scope
- Scan scope
- Task
- Trusted Platform Module
- Appendices
- Appendix 1. Application settings
- File Threat Protection
- Web Threat Protection
- Mail Threat Protection
- Network Threat Protection
- Firewall
- BadUSB Attack Prevention
- AMSI Protection
- Exploit Prevention
- Behavior Detection
- Host Intrusion Prevention
- Remediation Engine
- Kaspersky Security Network
- Web Control
- Device Control
- Application Control
- Adaptive Anomaly Control
- Endpoint Sensor
- Kaspersky Sandbox
- Endpoint Detection and Response
- Full Disk Encryption
- File Level Encryption
- Encryption of removable drives
- Templates (data encryption)
- Exclusions
- Application settings
- Reports and storage
- Network settings
- Interface
- Manage Settings
- Updating databases and application software modules
- Appendix 2. Application trust groups
- Appendix 3. File extensions for quick removable drives scan
- Appendix 4. File Types for the Mail Threat Protection attachment filter
- Appendix 5. Network settings for interaction with external services
- Appendix 6. Application events in the Windows Event Log
- Appendix 7. Application events in the Kaspersky Security Center event log
- Appendix 8. Supported file extensions for Execution prevention
- Appendix 9. Supported script interpreters
- Appendix 10. IOC scan scope in the registry (RegistryItem)
- Appendix 11. IOC file requirements
- Appendix 1. Application settings
- Information about third-party code
- Trademark notices
Managing policies
A policy is a collection of application settings that are defined for an administration group. You can configure multiple policies with different values for one application. An application can run under different settings for different administration groups. Each administration group can have its own policy for an application.
Policy settings are sent to client computers by Network Agent during synchronization. By default, the Administration Server performs synchronization immediately after policy settings are changed. UDP port 15000 on the client computer is used for synchronization. The Administration Server performs synchronization every 15 minutes by default. If synchronization fails after policy settings were changed, the next synchronization attempt will be performed according to the configured schedule.
Active and inactive policy
A policy is intended for a group of managed computers and can be active or inactive. The settings of an active policy are saved on client computers during synchronization. You cannot simultaneously apply multiple policies to one computer, therefore only one policy may be active in each group.
You can create an unlimited number of inactive policies. An inactive policy does not affect application settings on computers in the network. Inactive policies are intended as preparations for emergency situations, such as a virus attack. If there is an attack via flash drives, you can activate a policy that blocks access to flash drives. In this case, the active policy automatically becomes inactive.
Out-of-office policy
An out-of-office policy is activated when a computer leaves the organization network perimeter.
Settings inheritance
Policies, like administration groups, are arranged in a hierarchy. By default, a child policy inherits settings from the parent policy. Child policy is a policy for nested hierarchy levels, that is a policy for nested administration groups and secondary Administration Servers. You can disable the inheritance of settings from the parent policy.
Each policy setting has the ![]() attribute, which indicates if the settings can be modified in the child policies or in the local application settings. The
attribute, which indicates if the settings can be modified in the child policies or in the local application settings. The ![]() attribute is applicable only if inheritance of parent policy settings is enabled for the child policy. Out-of-office policies do not affect other policies through the hierarchy of administration groups.
attribute is applicable only if inheritance of parent policy settings is enabled for the child policy. Out-of-office policies do not affect other policies through the hierarchy of administration groups.
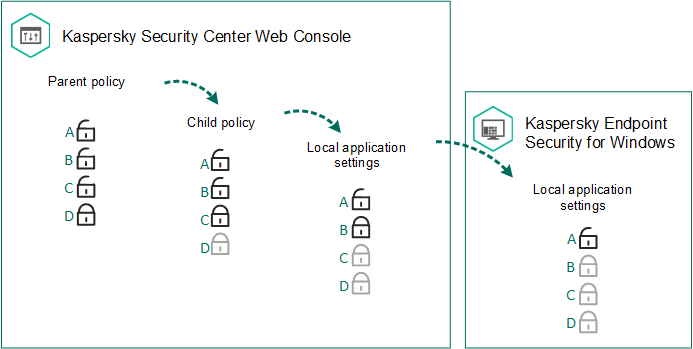
Settings inheritance
The rights to access policy settings (read, write, execute) are specified for each user who has access to the Kaspersky Security Center Administration Server and separately for each functional scope of Kaspersky Endpoint Security. To configure the rights to access policy settings, go to the Security section of the properties window of the Kaspersky Security Center Administration Server.
Creating a policy
How to create a policy in the Administration Console (MMC)
- Open the Kaspersky Security Center Administration Console.
- In the Managed devices folder in the Administration Console tree, select the folder with the name of the administration group to which the relevant client computers belong.
- In the workspace, select the Policies tab.
- Click the New policy button.
The Policy Wizard starts.
- Follow the instructions of the Policy Wizard.
How to create a policy in the Web Console and Cloud Console
- In the main window of Web Console, select Devices → Policies & profiles.
- Click the Add button.
The Policy Wizard starts.
- Select Kaspersky Endpoint Security and click Next.
- Please read and accept the terms of the Kaspersky Security Network (KSN) Statement and click Next.
- On the General tab, you can perform the following actions:
- Change the policy name.
- Select the policy status:
- Active. After the next synchronization, the policy will be used as the active policy on the computer.
- Inactive. Backup policy. If necessary, an inactive policy can be switched to active status.
- Out-of-office. The policy is activated when a computer leaves the organization network perimeter.
- Configure the inheritance of settings:
- Inherit settings from parent policy. If this toggle button is switched on, the policy setting values are inherited from the top-level policy. Policy settings cannot be edited if
 is set for the parent policy.
is set for the parent policy. - Force inheritance of settings in child policies. If the toggle button is on, the values of the policy settings are propagated to the child policies. In the properties of the child policy, the Inherit settings from parent policy toggle button will be automatically switched on and cannot be switched off. Child policy settings are inherited from the parent policy, except for the settings marked with
 . Child policy settings cannot be edited if
. Child policy settings cannot be edited if  is set for the parent policy.
is set for the parent policy.
- Inherit settings from parent policy. If this toggle button is switched on, the policy setting values are inherited from the top-level policy. Policy settings cannot be edited if
- On the Application settings tab, you can configure the Kaspersky Endpoint Security policy settings.
- Save your changes.
As a result, Kaspersky Endpoint Security settings will be configured on client computers during the next synchronization. You can view information about the policy that is being applied to the computer in the Kaspersky Endpoint Security interface by clicking the Support button on the main screen (for example, the policy name). To do so, in the settings of the Network Agent policy, you need to enable the receipt of extended policy data. For more details about a Network Agent policy, please refer to the Kaspersky Security Center Help.
Security level indicator
The security level indicator is displayed in the upper part of the Properties: <Policy name> window. The indicator can take one of the following values:
- High protection level. The indicator takes this value and turns green if all components from the following categories are enabled:
- Critical. This category includes the following components:
- File Threat Protection.
- Behavior Detection.
- Exploit Prevention.
- Remediation Engine.
- Important. This category includes the following components:
- Kaspersky Security Network.
- Web Threat Protection.
- Mail Threat Protection.
- Host Intrusion Prevention.
- Critical. This category includes the following components:
- Medium protection level. The indicator takes this value and turns yellow if one of the important components is disabled.
- Low protection level. The indicator takes this value and turns red in one of the following cases:
- One or multiple critical components are disabled.
- Two ore more important components are disabled.
If the indicator has the Medium protection level or Low protection level value, a link that opens the Recommended protection components window appears to the right of the indicator. In this window, you can enable any of the recommended protection components.