Step 1. Importing the ARB package
April 11, 2024
ID 167562
This section describes how to import the ARB package to ArcSight.
The ARB package contains objects (active channels, dashboards, field sets, reports, rules, filters, users) that are necessary for integrating the service with ArcSight. When you import this file, these objects are created in ArcSight.
To import the ARB package:
- Run ArcSight Console.
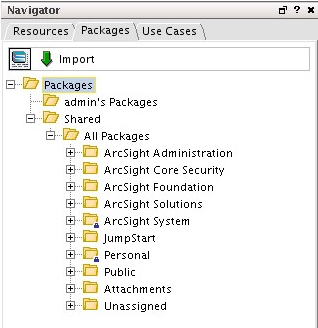
- In the Navigator pane (tree view), select the Packages tab.
- Click the Import button.
ArcSight packages
- In the Open window, select the Kaspersky_CyberTrace_Connector.arb file, located in the
/integration/arcsight/directory of the distribution kit.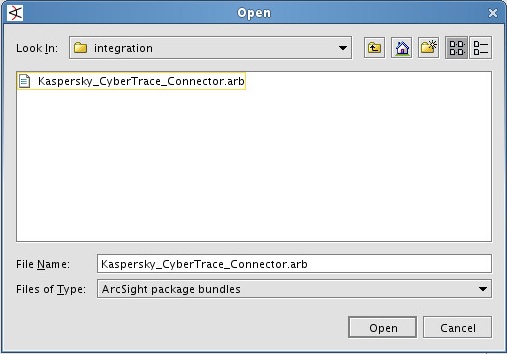
ARB file selection
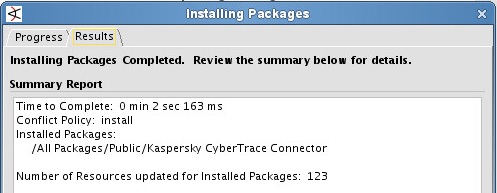
The import process will be performed.
ARB import complete
After all objects from the ARB file are imported to ArcSight, all the imported rules are real-time rules, that is, they will be applied in real time.
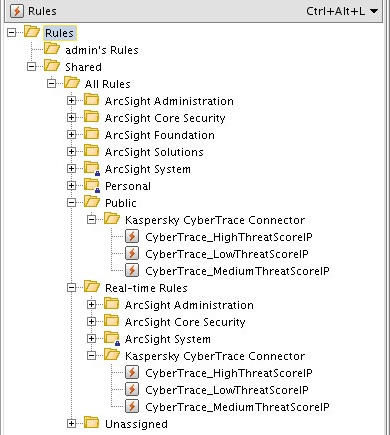
To browse and manage the list of real-time rules:
- In the tree view, click the Resources tab.
- Open the Active Channels drop-down list and select Rules.
- In the tree, select Rules > Shared > All Rules > Real-time Rules.
Real-time rules
- Expand Real-time Rules and remove unnecessary nested items from it.
After the ARB package is imported, new objects are created in ArcSight.
- When the Active Channels item in the tree view is selected, the following objects will be at the Active Channels > Shared > All Active Channels > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace alerts
Displays service events from Kaspersky CyberTrace in real time.
Turned on
CyberTrace all matches
Displays detection events from Kaspersky CyberTrace in real time.
Turned on
CyberTrace hash matches
Displays hash detection events from Kaspersky CyberTrace in real time.
Turned off
CyberTrace URL matches
Displays URL detection events from Kaspersky CyberTrace in real time.
Turned off
CyberTrace IP matches
Displays IP detection events from Kaspersky CyberTrace in real time.
Turned off
- When the Dashboards item in the tree view is selected, the following objects will be at the Dashboards > Shared > All Dashboards > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace detection map
Displays all devices that sent events containing malicious URLs, IP addresses, or hashes. Displays all feeds that were involved in the detection process.
Turned off
CyberTrace match statistics
Detection statistics: how many objects of a specific category were detected.
Turned on
CyberTrace Top 10 matched indicators
Top 10 detected indicators.
Turned off
The
CyberTrace detection mapandCyberTrace Top 10 matched indicatorsdashboards are turned off by default so as not to overload ArcSight. You can turn them on if you need these dashboards. - When the Field Sets item in the tree view is selected, the following objects will be at the Field Sets > Shared > All Field Sets > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace alerts
Displayed fields of service events from Kaspersky CyberTrace.
Static
CyberTrace all matches
Displayed fields of detection events from Kaspersky CyberTrace.
Static
CyberTrace matched hashes
Displayed fields of hash detection events from Kaspersky CyberTrace.
Static
CyberTrace matched URLs
Displayed fields of URL detection events from Kaspersky CyberTrace.
Static
CyberTrace matched IPs
Displayed fields of IP address detection events from Kaspersky CyberTrace.
Static
- When the Reports item in the tree view is selected, the following objects will be at the Reports > Shared > All Reports > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace all matches
Report that contains detection events from Kaspersky CyberTrace.
Static
- When the Rules item in the tree view is selected, the following object will be at the Rules > Shared > All Rules > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace_HighThreatScoreIP
Rule for assigning high severity level and storing high priority IP detection events from Kaspersky CyberTrace.
Turned on
CyberTrace_MediumThreatScoreIP
Rule for assigning medium severity level and storing medium priority IP detection events from Kaspersky CyberTrace.
Turned on
CyberTrace_LowThreatScoreIP
Rule for assigning low severity level and storing low priority IP detection events from Kaspersky CyberTrace.
Turned on
- When the Filters item in the tree view is selected, the following objects will be at the Filters > Shared > All Filters > Public > Kaspersky CyberTrace Connector location:
Object
Description
Default state
CyberTrace all matches
Filter for selecting detection events sent by Kaspersky CyberTrace.
Static
CyberTrace forwarding events
Filter for forwarding to Kaspersky CyberTrace those events that contain URLs, IP addresses, or hashes.
Static
CyberTrace matched hashes
Filter for selecting hash detection events sent by Kaspersky CyberTrace.
Static
CyberTrace matched URLs
Filter for selecting URL detection events sent by Kaspersky CyberTrace.
Static
CyberTrace matched IPs
Filter for selecting IP detection events sent by Kaspersky CyberTrace.
Static
- When the Users item in the tree view is selected, the following objects will be at the Users > Shared > Custom User Groups > Kaspersky CyberTrace Connector location:
Object
Description
Default state
FwdCyberTrace
Account that is used for configuring ArcSight event forwarding.
Static
After the import is finished, make sure that the FwdCyberTrace user is created. To check, navigate to Users > Shared > Custom User Groups > Kaspersky CyberTrace Connector in ArcSight Console. If there is no FwdCyberTrace user, create it manually.
