Parsing Kaspersky CyberTrace service events in McAfee Enterprise Security Manager
April 11, 2024
ID 183379
This section describes how to parse Kaspersky CyberTrace service events that have the following format:
Kaspersky CyberTrace Service Event| date=%Date% alert=%Alert% msg:%RecordContext%
Note that if you change the service events format, you have to change the parsing service event rules in McAfee Enterprise Security Manager.
To parse a service event, enter the following data in the Advanced Syslog Parser Rule dialog box:
- In the main window of McAfee Enterprise Security Manager, click Configuration.
- In the Physical Display tree, select a Receiver device, and then click Add Data Source.
Adding a data source
The Add Data Source dialog box appears.
- In the Add Data Source dialog box, enter the following data:
- Data Source Vendor: Generic
- Data Source Model: Advanced Syslog Parser
- Data Format: Default
- Data Retrieval: SYSLOG (Default)
- Enabled: Parsing
- Name: Kaspersky CyberTrace
- IP: The IP address of the computer from which Kaspersky CyberTrace will send events
- Syslog Relay: None
- Mask: 0
- Require syslog TLS: Cleared
- Port: 514
- Support Generic Syslogs: Log "unknown syslog" event
McAfee Enterprise Security Manager receives all events from Kaspersky CyberTrace. If McAfee Enterprise Security Manager cannot parse an event, the event displays as unknown.
- Time Zone: Select the time zone you need
- Encoding: None
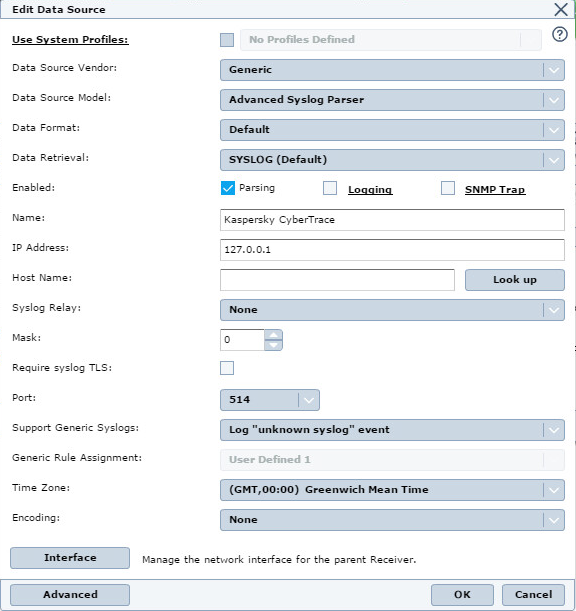
Configuration of the data source
- (Optional) Click Advanced to specify parameters for the data source in the Advanced options dialog box.
- Click OK.
McAfee ESM suggests that you roll out the policy you have set.
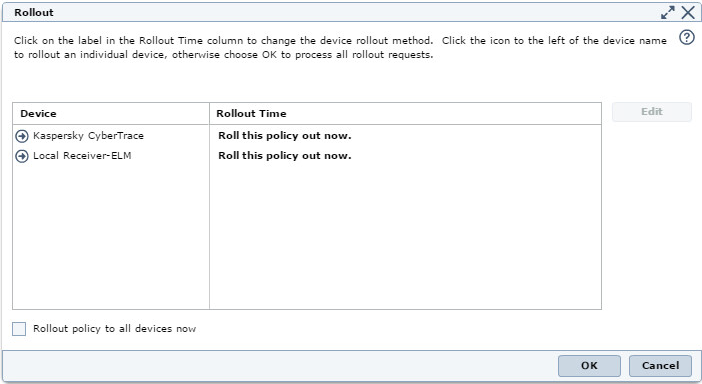
Rollout dialog box
- Select Kaspersky CyberTrace, and then click the Policy Editor toolbar button.
Selecting Policy editor
- In the Policy Editor window, select the Advanced Syslog Parser Rules rule type.
- Click New > Advanced Syslog Parser Rule.
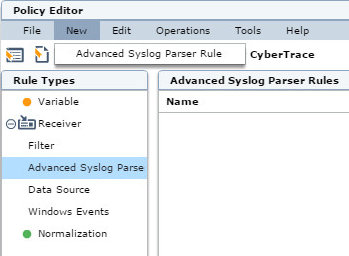
Policy Editor window
- To create a parser for parsing feed updating events, enter the following data in the Advanced Syslog Parser Rule dialog box:
- In the General tab, enter the following data:
- Name:
Kaspersky_CyberTrace_ServiceEvent - Tags: Select the tags that define the rule (that is, they will be used while filtering events)
- Rule Assignment Type: User Defined 1 or another user defined type
- Description: The Kaspersky Lab CyberTrace service event
- Name:
- In the Parsing tab, enter the following data:
- Provide content strings: Kaspersky CyberTrace Service Event
- Sample Log Data: Provide an example of a feed updating event. For example (in a single line, without newline symbols):
Kaspersky CyberTrace Service Event| date=Apr 17 19:08:28 alert=KL_ALERT_UpdatedFeed msg:feed=Demo_Botnet_CnC_URL_Data_Feed.json records=3907
- Add the following regular expressions in the Parsing tab:
Name
Regular Expression
ct_service_namealert\=(\S+)(?=\s)ct_context(msg.*)(?=$)ct_datedate\=(\S+\s\d+\s\S+)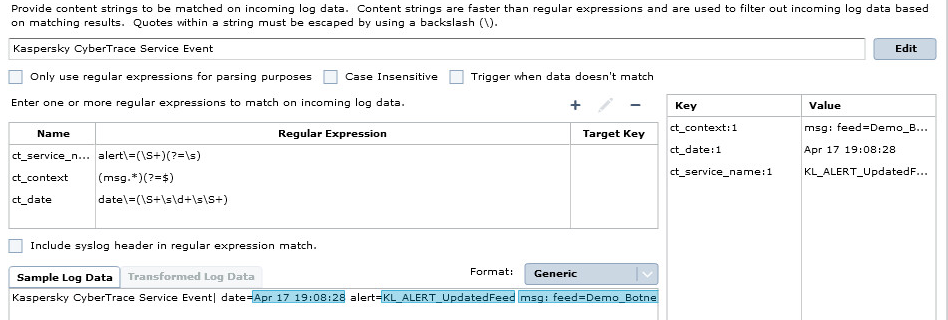
Parsing tab
- In the Field Assignment tab, enter the following data:
Field
Expression
Action
"0"Description
Drag
ct_contextin this fieldSeverity
"60"or another value you chooseReturn_Code
Drag
ct_service_namein this fieldFirst Time
Drag
ct_datein this field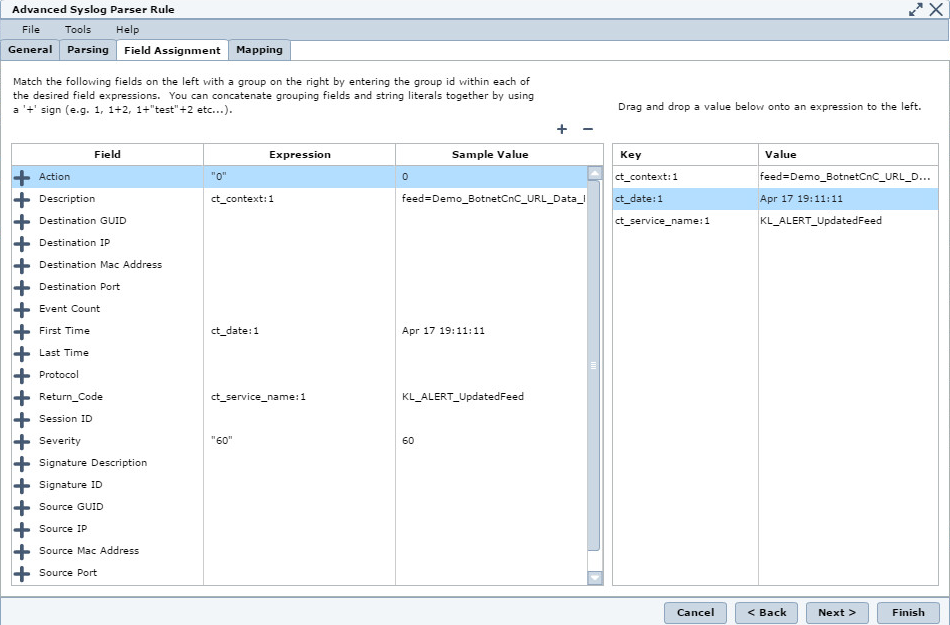
Field Assignment tab
You can add other fields here by clicking the + button.
- In the Mapping tab, enter the following data:
- In the time data table:
Time Format
Time Fields
%b %d %H:%M:%SFirst time- In the actions table:
Action Key
Action Value
0Success- In the severity table:
Severity Key
Severity Value
6060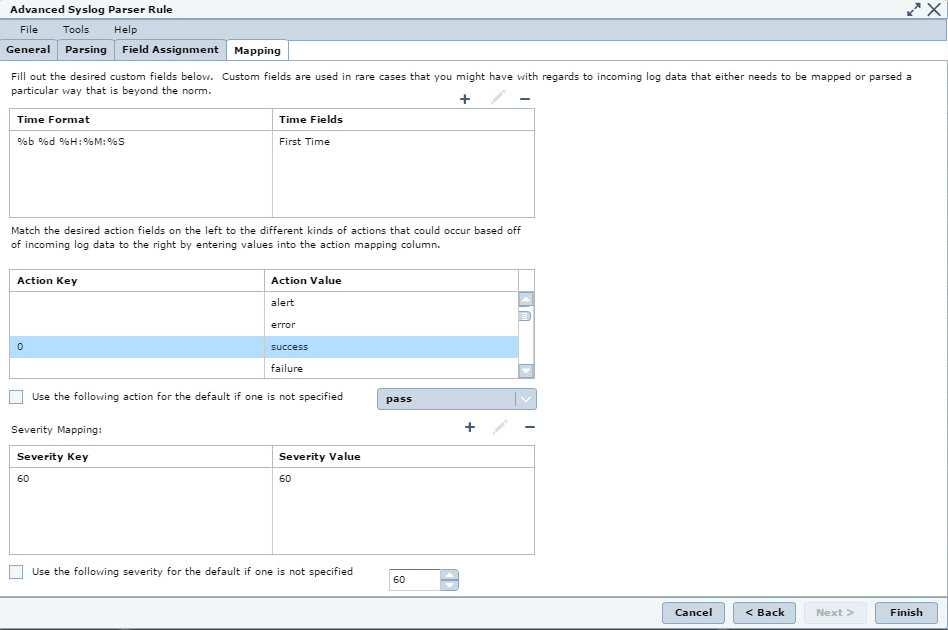
Mapping tab
- In the General tab, enter the following data:
- Click Finish to save the policy.
- In the Default Policy list, select the
Kaspersky CyberTracedevice, and then enable theKaspersky_CyberTrace_ServiceEventrule.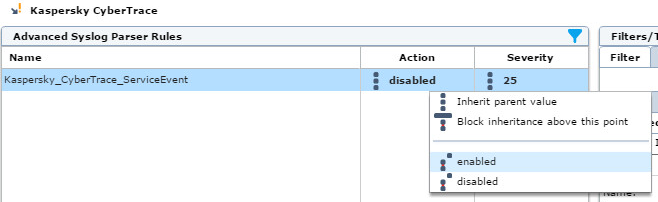
Enabling a rule
- Select File > Save to save the current state.
- Select Operations > Rollout to roll out the policy.
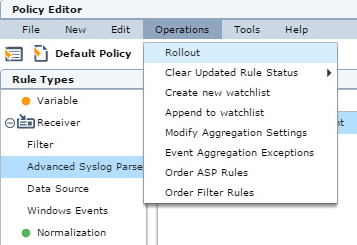
Rolling out a policy
- When prompted, agree to reinitialize the
Kaspersky CyberTracedevice in McAfee ESM. - Select the Operations > Modify Aggregation Settings menu item to change Kaspersky CyberTrace service events aggregation rules.
- In Modify Aggregation Settings, in
Field 2, set the valueReturn_Code, and then click OK.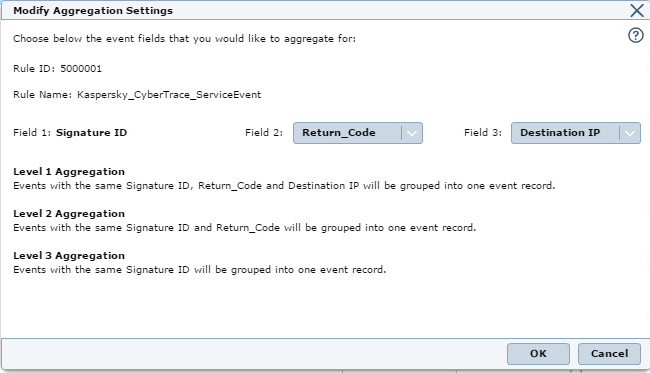
Modify Aggregation Settings
- Confirm the rollout request.
