Specifying the log source type
Perform the following procedure only if you had to add Feed Service to QRadar as a log source manually because you did not have the latest QRadar updates. Use the procedure to specify the Log Source Type property of the added custom event properties.
To specify the log source type of the added custom event properties:
- In QRadar, select Admin and under Data sources, in the Events section, select Custom Event Properties.
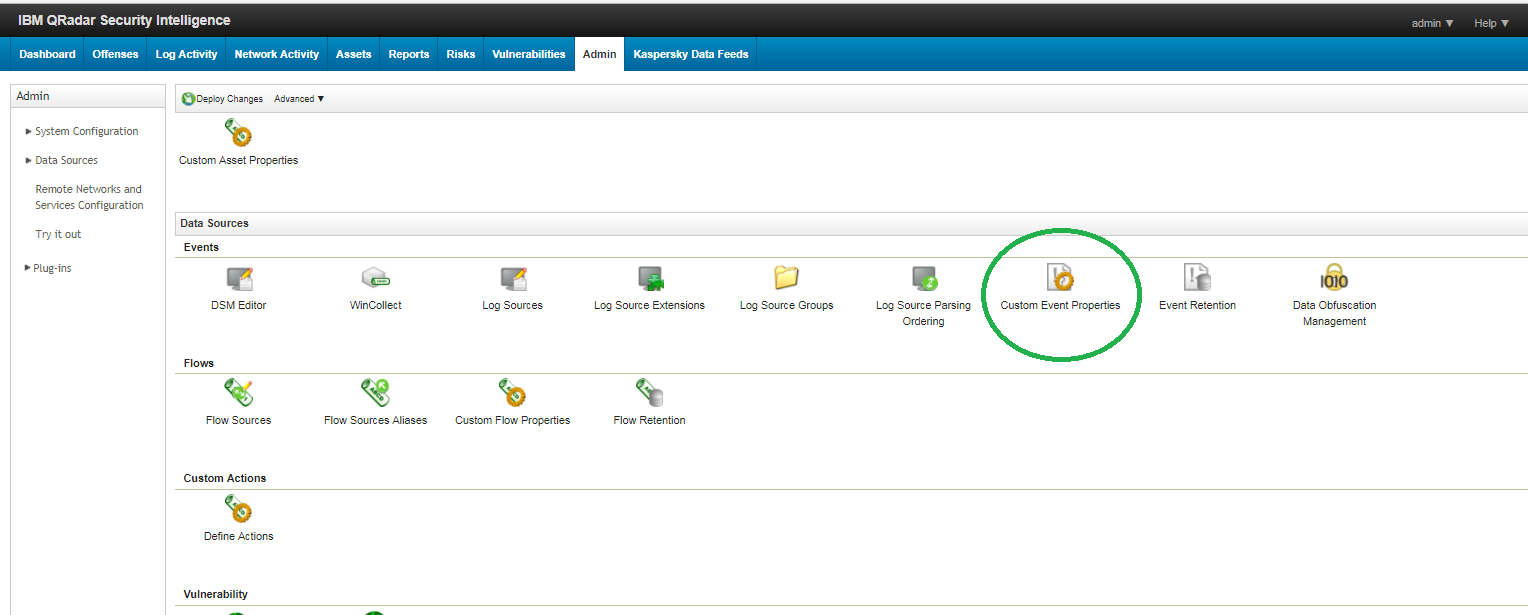
Admin tab of QRadar Console
The Custom Event Properties window opens.
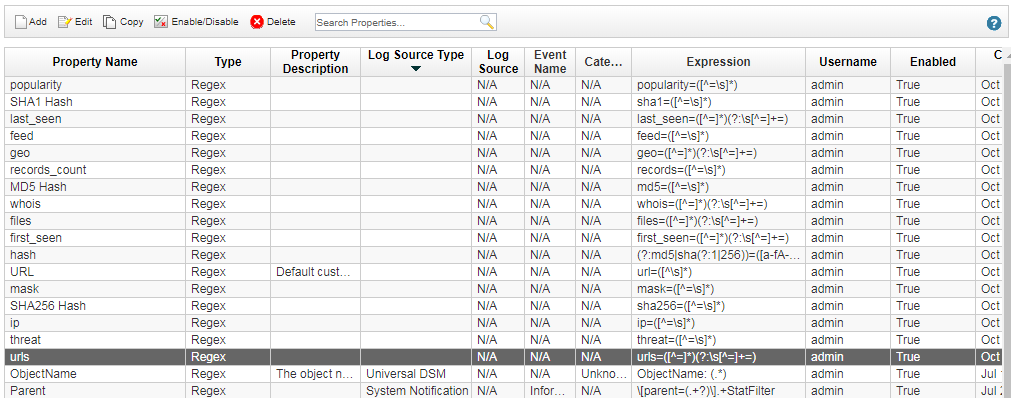
Custom event properties
- For each custom event property perform the following steps:
- Select the property.
- Click Edit.
A Custom Event Property Definition window opens.
- In the Log Source Type drop-down box, select Universal LEEF.
- Select the Existing Property option.
The Existing Property option was selected before you changed the value in the Log Source Type drop-down box. But after you changed the log source type, the New Property option was selected. Therefore, you have to select the Existing Property option again.
- Click Save.
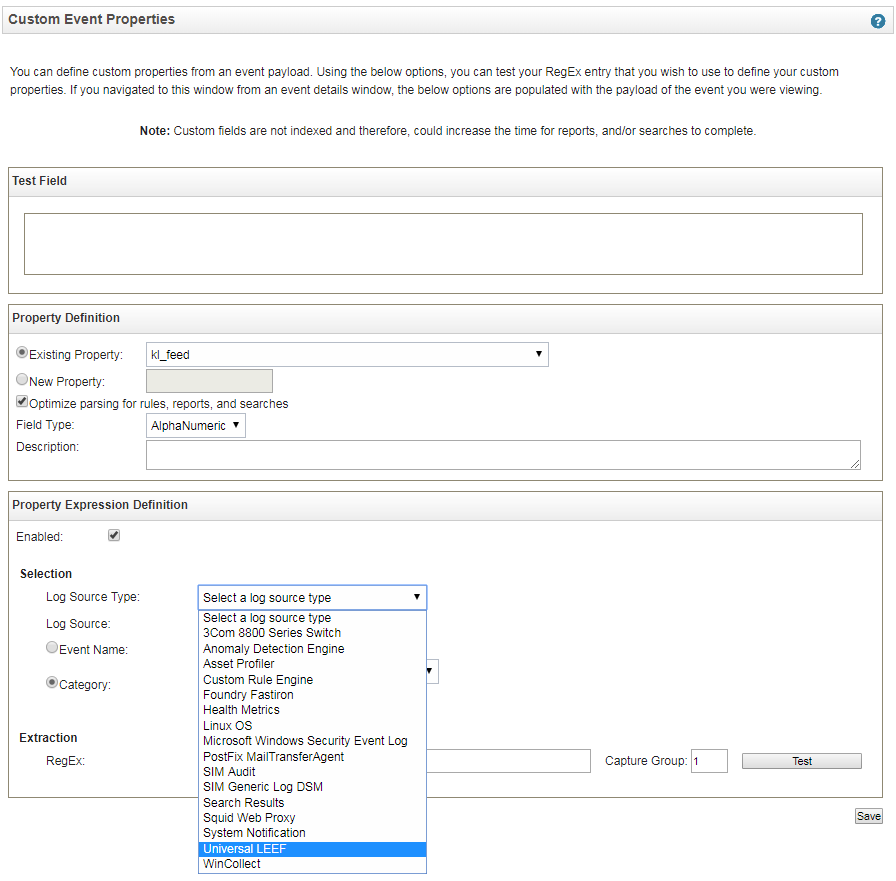
Custom event property definition
The log source type of every custom event property will now be Universal LEEF.