About TLS connections
When a user wants to connect to a web resource over the HTTPS protocol, you must establish a secure encrypted connection between the user's computer and the web server hosting the required web resource. After a basic TCP/IP connection is established, the client and the server exchange security certificates and encryption settings. As a result, an encrypted data channel is created using the TLS (Transport Layer Security) protocol. For this reason, encrypted connections are also called TLS connections. Within this channel, data is transmitted over an application-layer protocol, such as HTTP.
If decryption of TLS/SSL connections is disabled in the application, the proxy server relays messages between the client and the server without intervening in the handshake. In this case, the protection modules of Kaspersky Web Traffic Security (Anti-Virus and Anti-Phishing) are unable to scan data transmitted inside the encrypted data channel. This reduces the level of protection of the corporate IT infrastructure. That is why it is recommended to enable decryption of TLS/SSL connections.
If decryption of TLS/SSL connections is enabled in the application settings, the proxy server can intervene in the handshake. If this is the case, the application can apply the actions configured in SSL rules or the default actions to traffic if the scanned traffic does not satisfy the conditions of any SSL rule.
The application provides the following actions for handling encrypted connections:
- Tunnel.
- Tunnel with SNI check.
- Bump.
- Terminate.
To ensure the maximum level of security, it is recommended to select the Bump action. It is recommended to use the Tunnel and Tunnel with SNI check actions only for web resources or applications that do not support operation involving decryption of transmitted traffic (for example, banking applications).
Application of the Tunnel, Tunnel with SNI check, or Terminate actions
The figure below illustrates the principles according to which encrypted connections are established after application of the Tunnel, Tunnel with SNI check, or Terminate actions.
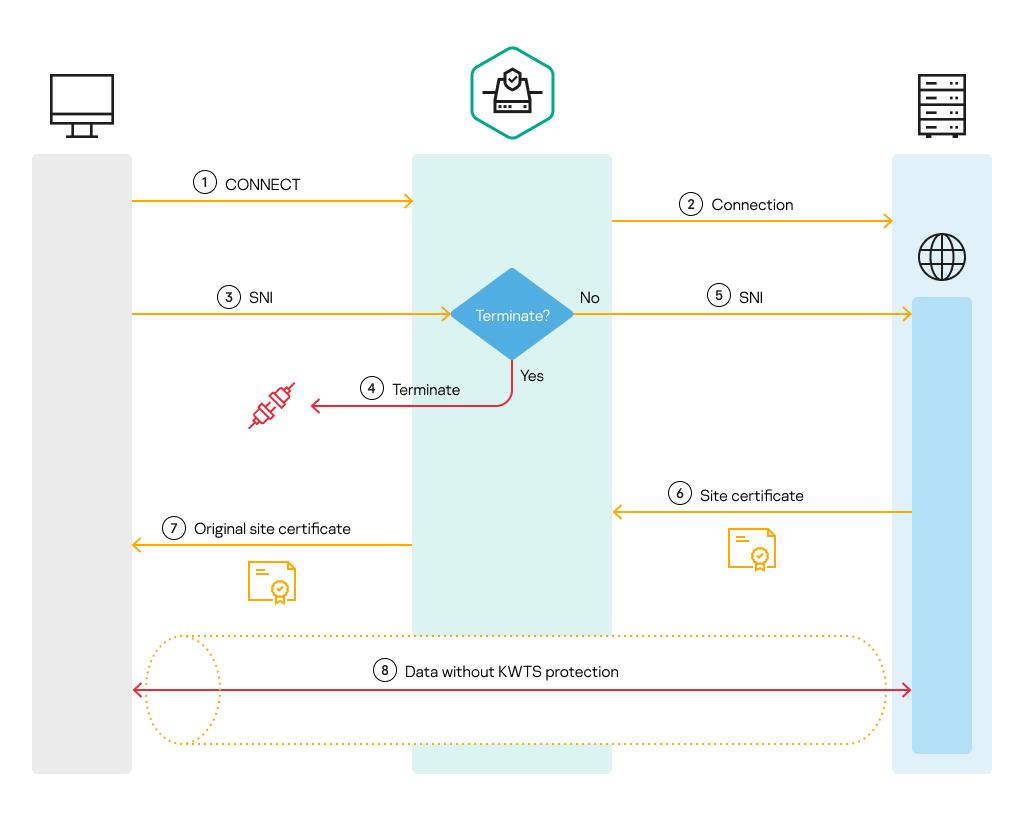
Principles according to which encrypted connections are established after application of the Tunnel, Tunnel with SNI check, or Terminate actions
Establishing an encrypted connection consists of the following steps:
- Client request
The client sends a CONNECT request to the proxy server to connect with the web server. This request contains the fully qualified domain name (FQDN) or IP address of the web server hosting the requested web resource.
- Request redirection to the server
The proxy server generates and sends a request for connection to a web server, receives a response from it, and relays this response to the client.
- Transmission of SNI and other encryption settings of the client to the proxy server
The client sends the proxy server its supported encryption settings and the SNI field, which indicates the fully qualified domain name (FQDN) of the relevant web resource (website).
- Checking whether the connection should be interrupted
If the Terminate action is applied to the request according to actions specified in SSL rules or the default action, the connection is terminated. A block page is not displayed to the user.
- Transmission of SNI and other encryption settings of the client to the web server
If the Terminate action has not been applied to the request, the proxy server relays the SNI field and other encryption settings to the web server on behalf of the client.
- Transmission of the certificate of a web resource to the proxy server
The web server returns to the proxy server its own set of supported encryption settings, and the certificate of the web resource to which the user requested access based on the SNI field.
- Transmission of the certificate of a web resource to the client
The proxy server relays the certificate and encryption settings received from the web server to the client.
- Establishment of a secure connection
The client and server coordinate the other details of the connection. The secure data channel is then created, and the client and server can exchange data within this channel.
Application of the Terminate and Bump actions
The figure below illustrate the principles of processing of encrypted connections after application of the Terminate and Bump actions. In this case, steps 5 and 7 differ from the basic mechanism by which encrypted connections are established. At step 5, the proxy server transmits the SNI field and other encryption settings on its own behalf and not on behalf of the client. The proxy server receives the certificate of the requested web resource from the web server, generates its own (replacement) certificate on its basis, and relays this replacement certificate to the client.
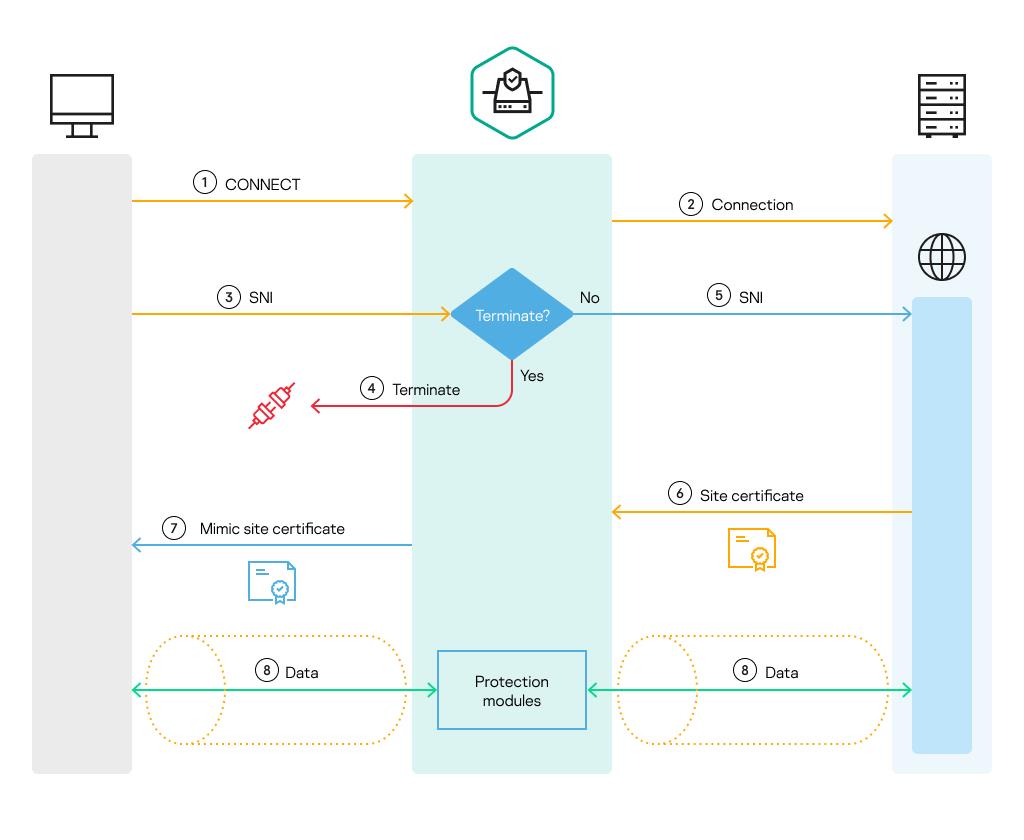
Principles of processing of encrypted connections after application of the Terminate and Bump actions
The table below illustrates how the application handles an encrypted connection depending on the configured action.
Processing encrypted connections depending on the configured action
Without proxy server involvement |
Tunnel |
Tunnel with SNI check |
Bump |
Terminate |
|---|---|---|---|---|
Client request. |
Client request. The proxy server allows the creation of a secure channel based on the IP address or fully qualified domain name (FQDN) of the web server. |
Client request. |
Client request. |
Client request. |
Server response. |
Server response. |
Server response. |
Server response. |
Server response. |
Transmission of SNI and other encryption settings of the client. |
Transmission of SNI and other encryption settings of the client. |
Transmission of SNI and other encryption settings of the client. The proxy server allows creation of a secure channel based on the SNI of the requested web resource. |
Transmission of SNI and other encryption settings of the client. The proxy server sends this data to the web server as if this data is from the proxy server and not from the client. |
The connection is terminated. A block page is not displayed to the user. |
Transmission of the certificate of the requested web resource. |
Transmission of the certificate of the requested web resource. |
Transmission of the certificate of the requested web resource. |
Transmission of the certificate of the requested web resource. The proxy server intercepts the certificate sent by the web server and generates its own replacement certificate on its basis. |
– |
Establishment of a secure connection. |
Establishment of a secure connection. The application cannot use the Anti-Virus and Anti-Phishing modules to scan transmitted data. |
Establishment of a secure connection. The application cannot use the Anti-Virus and Anti-Phishing modules to scan transmitted data. |
Establishment of a secure connection. Two channels are created: one between the client and proxy server, and one between the proxy server and the web server. The application can analyze the contents of encrypted channels and apply traffic processing rules to the data transmitted within the channel. |
– |